Question: MODULE : INFORMATION SYSTEMS AUDIT AND CONTROL PLEASE HELP ON ALL QUESTIONS What is meant by Business Continuity Planning? [3 marks] Identify and briefly explain
MODULE : INFORMATION SYSTEMS AUDIT AND CONTROL
PLEASE HELP ON ALL QUESTIONS

What is meant by Business Continuity Planning? [3 marks]
Identify and briefly explain the areas covered by Business Continuity. [6 marks]
Discuss briefly about recovery plan [5 marks]
Elaborate on the audit of the disaster recovery [5 marks]
Describe the role of an IS auditor in the evaluation of physical access control. [5 marks]
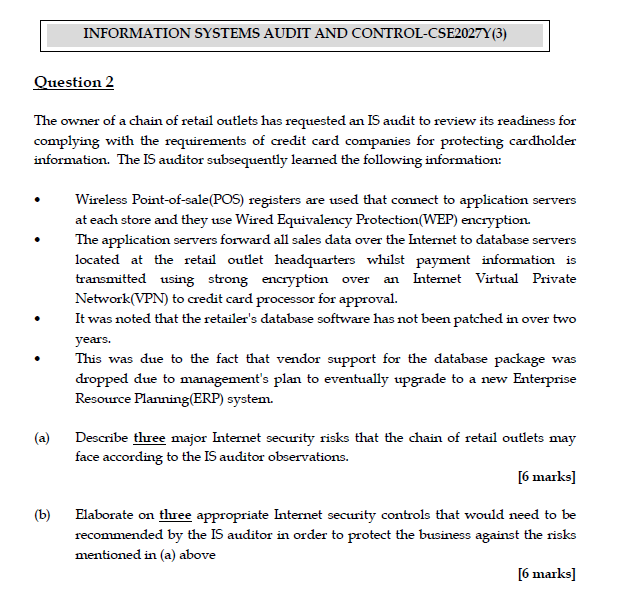
INFORMATION SYSTEMS AUDIT AND CONTROL-CSE2027Y(3) Question 2 The owner of a chain of retail outlets has requested an IS audit to review its readiness for complying with the requirements of credit card companies for protecting cardholder information. The IS auditor subsequently learned the following information: Wireless Point-of-sale(POS) registers are used that connect to application ser servers at each store and they use Wired Equivalency Protection(WEP) encryption. The application servers forward all sales data over the Internet to database servers located at the retail outlet headquarters whilst payment information is transmitted using strong encryption over an Internet Virtual Private Network(VPN) to credit card processor for approval. It was noted that the retailer's database software has not been patched in over two years. This was due to the fact that vendor support for the database package was dropped due to management's plan to eventually upgrade to a new Enterprise Resource Planning (ERP) system. (a) Describe three major Internet security risks that the chain of retail outlets may face according to the IS auditor observations. [6 marks] (b) Elaborate on three appropriate Internet security controls that would need to be recommended by the IS auditor in order to protect the business against the risks mentioned in (a) above [6 marks] Question 3 ABC is a leading company in the manufacturing of food items. The company is in the process of automation of its various business processes. During this phase, technical consultant of the company has highlighted the importance of information security and has suggested introducing it right from the beginning. He has also suggested to perform the risk assessment activity and accordingly, to mitigate the assessed risk. For carrying out all these suggestions, various best practices have been followed by the company. In addition, after each activity, appropriate standards' compliances have been tested to check the quality of each process. Various policies related with business continuity planning and disaster recovery planning has been implemented to ensure three major expectations from the software, namely, resist, tolerate and recover
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


