Question: Moving to the next question prevents changes to this answer. Question 22 What is the difference between proactive and reactive security? Explain with examples TT
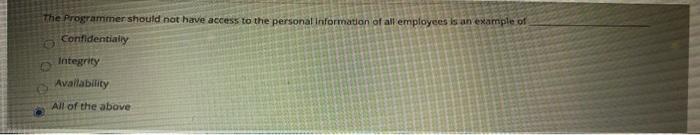
Moving to the next question prevents changes to this answer. Question 22 What is the difference between proactive and reactive security? Explain with examples TT T T Paragraph Arial 3 (12pt) - E-T- %DO TT. - The Programmer should not have access to the personal Information of all employees is an example of Confidentially Integrity Availability All of the above
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


