Question: N 2 . 1 6 . In an MITM attack, the attacker M tries to intercept the communication between A and B that are on
N In an MITM attack, the attacker M tries to intercept the communication between A and
that are on the same LAN. Please describe what M needs to do so it can modify the
packets from to
N In the MITM attack described in the book, the attacker M uses the ARP cache poison
ing attack to redirect the AtoB packets to M If the IP forwarding on the attacker
machine is turned off, what will happen to the packets? If the IP forwarding on
is turned on what will happen to the packets? If the attacker wants to modify the
packet, should the attacker turn on or off the IP forwarding.
N In the MITM attack described in the book, the attacker M uses the ARP cache poisoning
attack to redirect the AtoB packets to M How does the attacker get this packet?
N In the MITM attack code, the attacker tries to modify the packets from A to B After
intercepting such a packet, the attacker makes a copy of the packet, and then does the
following. Why does the attacker have to delete the IP and TCP checksums?
newpkt
del chksum
del chksum
N Machines A B and M are on the same LAN, and their IP addresses and MAC
addresses are listed below.
:
:
:
MAC address:
::::: MAC
address: :::::
The attacker on M wants to use the ARP cache poisoning to launch the MITM Man
In TheMiddle attack against A and B ie intercepting the communication between
A and
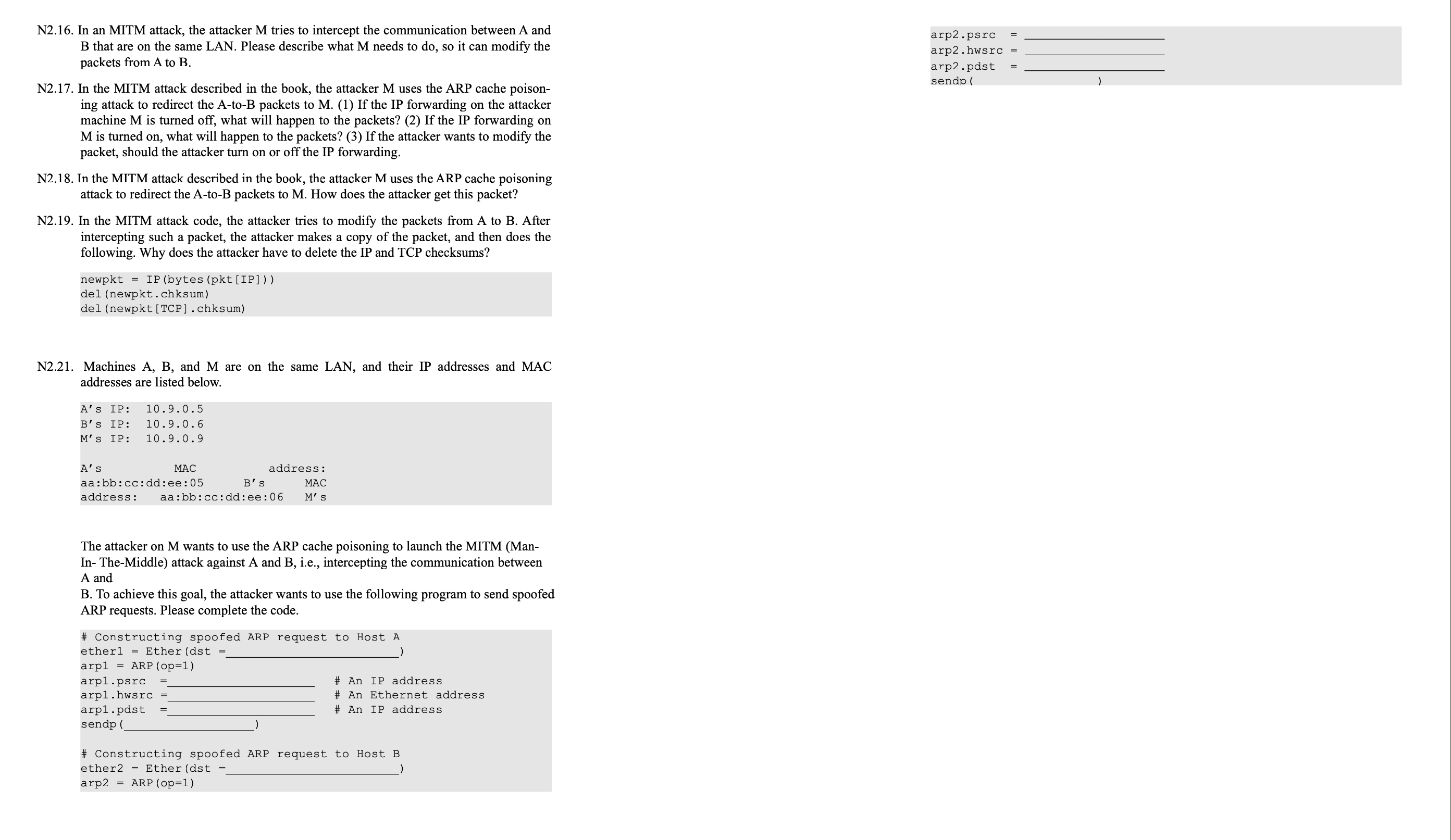
B To achieve this goal, the attacker wants to use the following program to send spoofed
ARP requests. Please complete the code.
# Constructing spoofed ARP request to Host A
ether Ether dst
arpARP
arppsrc # An IP address
arphwsrc # An Ethernet address
arppdst # An IP address
sendp
# Constructing spoofed ARP request to Host B
ether Ether dst
arpARP
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


