Question: need help answering the second and third question A piece of malware is running on a Windows 7 machine via process injection, so it does
need help answering the second and third question
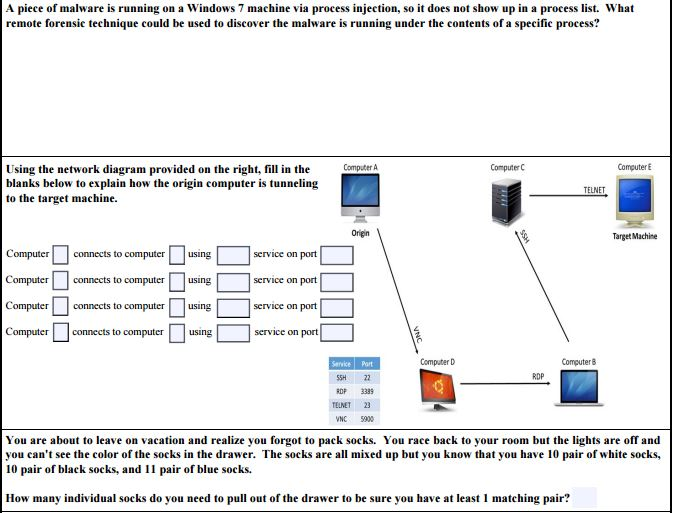
A piece of malware is running on a Windows 7 machine via process injection, so it does not show up in a process list. What remote forensic technique could be used to discover the malware is running under the contents of a specific process? Using the network diagram provided on the right, fill in the blanks below to explain how the origin computer is tunneling to the target machine. Computer connects to computer using service on port Computer connects to computer using service on port Computer connects to computer using service on port Computer connects to computer using service on port You are about to leave on vacation and realize you forgot to pack socks. You race back to your room but the lights are off and you can't see the color of the socks in the drawer. The socks are all mixed up but you know that you have 10 pair of white socks, 10 pair of black socks, and 11 pair of blue socks. How many individual socks do you need to pull out of the drawer to be sure you have at least 1 matching pair
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


