Question: Need help comparing and contrasting these two studies. Comparre and contrast the methods and conclusions used.( I labeled them Study 1 and Study 2) STUDY
Need help comparing and contrasting these two studies. Comparre and contrast the methods and conclusions used.( I labeled them Study 1 and Study 2)
STUDY 1



..............................................................................................................................................................................................
Study 2


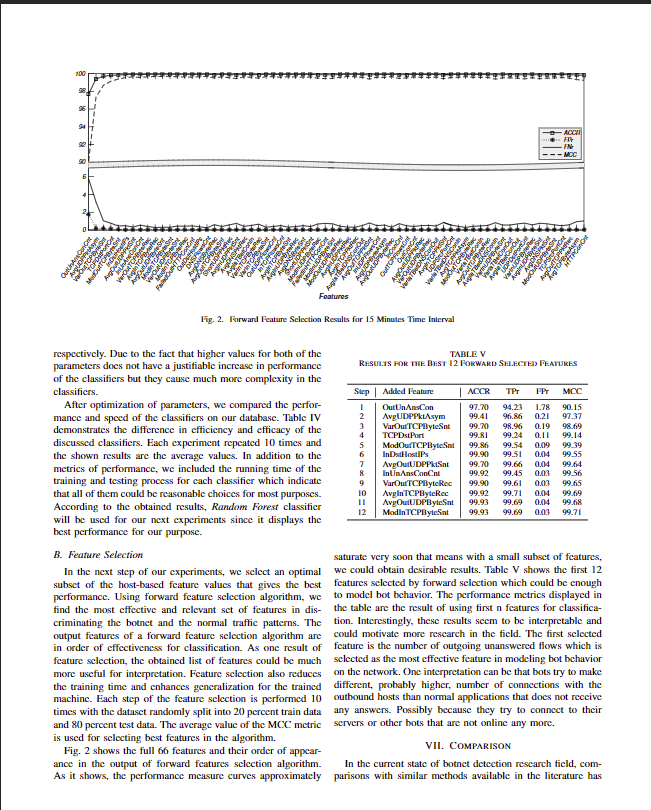
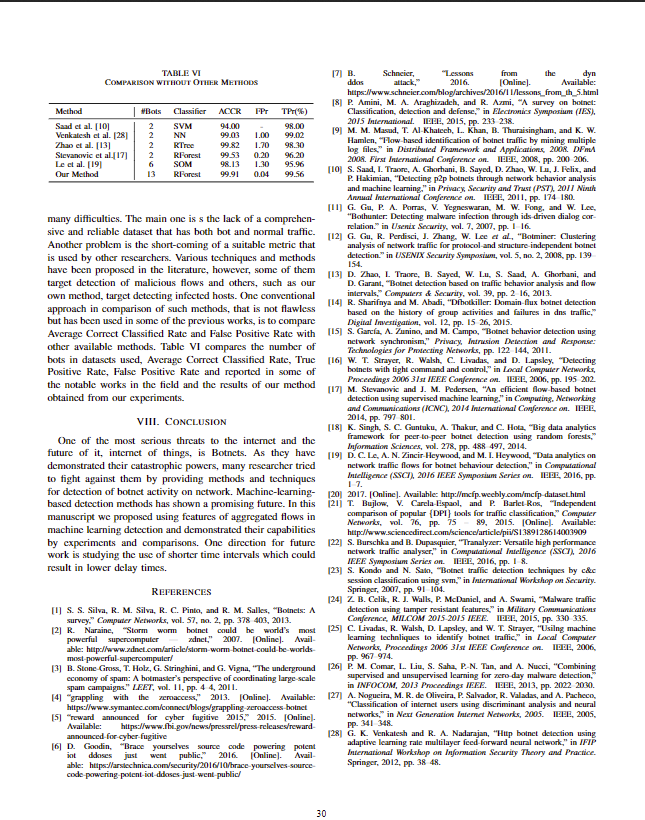
An efficient flow-based botnet detection using supervised machine learning Matija Stevanovic and Jens Myrup Pedersen Networking and Security Section, Depariment of Electronic Systems Aalborg University, Fredrik Bajers Vej 7, DK-9220 Aalborg, Denmark Abstract-Botnet detection represents one of the most crucia mails, Distributed Denial of Service (DDoS) attacks, malware prerequisites of successful botnet neutralization. This paper distribution, click fraud, information theft and attacks on explores how accurate and timely detection can be achieved by industrial control systems and other critical infrastructure. using supervised machine learning as the tool of inferring about malicious botnet traffic. In order to do so, the paper i a novel flow-based detection system that relies on supervised detection approach is needed, that could provide high accuracy machine learning for identifying botnet network traffic. For use of detection and low time and computational requirements in the system we consider eight highly regarded machine learning of operation. This paper explores how accurate and timely algorithms, indicating the best performing one. Furthermore, detection can be achieved In order to successfully neutralize botnet threats an efficient paper evaluates how much traffic needs to be observed analysis and supervised machine learning as a tool for identi fying malicious botnet traffic. The contribution of the paper is per flow in order to capture the patterns of malicious traffic. The proposed system has been tested through the series of experiments using traffic traces originating from two well-known P2P botnets and diverse non-malicious applications. of experiments indicate that the system is able to accurately and timely detect botnet traffic using purely flow-based traffic analysis ond, the paper evaluates performances of eight highly regarded and supervised machine learning. Additionally, the results sho that in order to achieve accurate detection traffic flows need to be of classifying botnet traffic within the proposed system. Third, monitored for only a limited time period and number of packets per flow. This indicates a strong potential of using the proposed The results system that relies on flow-based traffic analysis and supervised supervised Machine Learning Algorithms ( explores how much traffic needs to be observed the per flow so the malicious traffic patterns could be captured and accurate classification of traffic could be achieved. As a Keywords-Botnet, Botnet detection, Traffic analysis, Trafic resut the proposed approach obtains detection performances features and limited amount of traffic per flow. Furthermore, Botnets are one of the most serious threats to the Internet being used in more adaptable on-line setup. security and one of the most challenging topics within the fields of computer and network security today. Botnets rep- resent a usually large collections of computers compromised a ow-based botnet detection system by elaborating with a sophisticated bot malware, that puts them under control of a remote attacker [1]. The compromised computers Section IV are often referred to as "zombis" or "bots" while attackers is referred to as the "botmaster". Contrary to other more con- ventional malware types, such as viruses, trojans and worms, presents how detection performances are dependent on the bot malware has an advantage of being able to communicate ow duration and the number of packets observed per flow with an attacker through a specially deployed Command and Section V discusses presented results and possibilities for Control (C&C) communication channel. Botnets deploy C&C channel using a variety of communication protocols, such as: IRC, HTTP HTTPS and in the most recent botnets, P2HP paper is organized as follows. Section II presents an overview of related work. Section III introduces on the employed principles of flow-based traffic analysis. presents the results of experimenting with the system, analyzing the performances of the systerm eight contemporary supervised MLAs. This chapter also further improvements. Finally, Section VI concludes the paper ng the findings and outlining future work. II. RELATED wORK techniques that make C&C channel more resilient to detection such as encryption, protocol obfuscation, Fast-flux and DGA (Domain Generation Algorithm 12J. Using the C&Cc methods is detection based on the identification of botnet the botmaster can remotely control the behavior of the bo traffic (both C&C and attack) using machine learning algo- malware, making the operation of bots more flexible and rithms [] The main assumption of the machine 1 adaptable to the miscreant's needs. Controlled and coordinated based approaches is that botnets create distinguishable by the botmaster, botnets represent a collaborative and highly fic patterns that could be efficiently detected using MLAs distributed platform for the implementation of a wide range These approaches have a number of advantages comparing of malicious and illegal activities, such as: sending SPAMo conventional signature-based and anomaly-based detection
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


