Question: Need help to code this in java please. Please add commnets. I will rate. The objective of the project is to demonstrate, from an attackers
Need help to code this in java please. Please add commnets. I will rate.
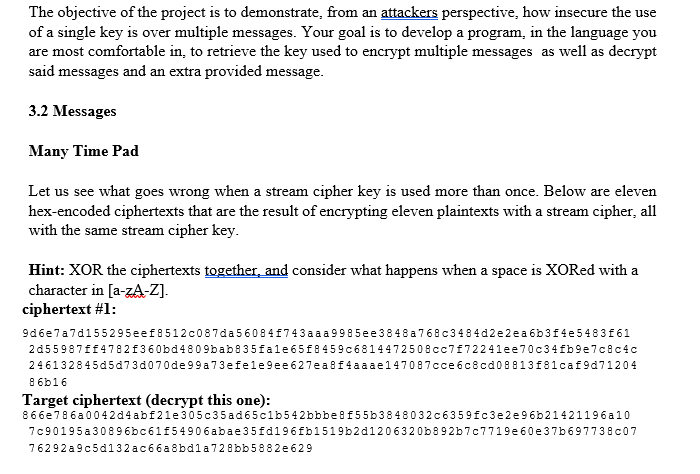


The objective of the project is to demonstrate, from an attackers perspective, how insecure the use of a single key is over multiple messages. Your goal is to develop a program, in the language you are most comfortable in, to retrieve the key used to encrypt multiple messages as well as decrypt said messages and an extra provided message 3.2 Messages Many Time Pad Let us see what goes wrong when a stream cipher key is used more than once. Below are eleven hex-encoded ciphertexts that are the result of encrypting eleven plaintexts with a stream cipher, all with the same stream cipher key Hint: XOR the ciphertexts together, and consider what happens when a space is XORed with a character in [a-zA-Z] ciphertext #1 9d6e7a7d155295eef8512c087da56084f743aaa9985ee3848a768c3484d2e 2ea 6b3f4e548361 2d55987ff4782f360bd4809bab835fale65f8459c6814472508cc7172241ee70c34fb9e7c8c4 c 246132845d5d7 3 d 0 7 0 d e 9 9 a 7 3 e fe 1 e 9 e e 6 2 7 e a 8 f 4 a a a e 1 4 7 0 8 7 cce6c8cd08813f81caf9d7 1204 8 6b16 Target ciphertext (decrypt this one) 866e786a 0042d4abf21e 305c35ad65cib542bbbe8f55b3848032c6359fc3e2e96b21421196a10 7c90195a 30896bc61f5490 6abae 35fd196fb1519b2d1206320b892b7c7719e 60e 37b697738 c07 7 6292a9c5d132ac66a8bd1a728bb5882e 629 Hints OTP A one time pad works by XORing a key with a given plaintext. The key is looped to fit the message if necessary. Should the key be used more than once the key can be retrieved and messages exposed. Message 1 XOR key= Cipher 1 Message 2 XOR key- Cipher 2 (Cipher 1) XOR (Cipher 2)-(Message 1) XOR (Message 2) Crib Dragging Despite the insecurity that results from the XOR of two cipher texts. The resultant text is quite illegible. This is where crib dragging comes in, crib dragging is where you take frequently used words and xor them with the result of (Cipher 1) XOR (Cipher 2). If the word is contained in one message then you will get the legible text of the other message. This portion will take some guessing as you may receive incomplete words or parts of sentences. Guess the rest of the word and then use that as the new crib. You will be uncovering the two, or more, of the messages involved simultaneously. When you have one completed message you can then use that to recover the original key ASCII, Hex, Binary The project requires that at some point you XOR two given strings. These strings can be in ASCII, HEX, or Binary. The original strings are provided in HEX format. Feel free to convert, or not covert, between formats if it makes it easier Length and padding An XOR is ,typically, done between two objects of the same length. You will notice that no two hex strings provided are the same length. Depending on the language used, there may or may not, be a third party library that will deal with this for you using padding. In either case, padding can either precede or come after that actual content. Note: 54686520736b792069732066616c6c696e67 XOR 4974206973206e6f740a0000000000000000 Does not equal 54686520736b792069732066616c6c696e67 XOR 00000000000000004974206973206e6f740a The objective of the project is to demonstrate, from an attackers perspective, how insecure the use of a single key is over multiple messages. Your goal is to develop a program, in the language you are most comfortable in, to retrieve the key used to encrypt multiple messages as well as decrypt said messages and an extra provided message 3.2 Messages Many Time Pad Let us see what goes wrong when a stream cipher key is used more than once. Below are eleven hex-encoded ciphertexts that are the result of encrypting eleven plaintexts with a stream cipher, all with the same stream cipher key Hint: XOR the ciphertexts together, and consider what happens when a space is XORed with a character in [a-zA-Z] ciphertext #1 9d6e7a7d155295eef8512c087da56084f743aaa9985ee3848a768c3484d2e 2ea 6b3f4e548361 2d55987ff4782f360bd4809bab835fale65f8459c6814472508cc7172241ee70c34fb9e7c8c4 c 246132845d5d7 3 d 0 7 0 d e 9 9 a 7 3 e fe 1 e 9 e e 6 2 7 e a 8 f 4 a a a e 1 4 7 0 8 7 cce6c8cd08813f81caf9d7 1204 8 6b16 Target ciphertext (decrypt this one) 866e786a 0042d4abf21e 305c35ad65cib542bbbe8f55b3848032c6359fc3e2e96b21421196a10 7c90195a 30896bc61f5490 6abae 35fd196fb1519b2d1206320b892b7c7719e 60e 37b697738 c07 7 6292a9c5d132ac66a8bd1a728bb5882e 629 Hints OTP A one time pad works by XORing a key with a given plaintext. The key is looped to fit the message if necessary. Should the key be used more than once the key can be retrieved and messages exposed. Message 1 XOR key= Cipher 1 Message 2 XOR key- Cipher 2 (Cipher 1) XOR (Cipher 2)-(Message 1) XOR (Message 2) Crib Dragging Despite the insecurity that results from the XOR of two cipher texts. The resultant text is quite illegible. This is where crib dragging comes in, crib dragging is where you take frequently used words and xor them with the result of (Cipher 1) XOR (Cipher 2). If the word is contained in one message then you will get the legible text of the other message. This portion will take some guessing as you may receive incomplete words or parts of sentences. Guess the rest of the word and then use that as the new crib. You will be uncovering the two, or more, of the messages involved simultaneously. When you have one completed message you can then use that to recover the original key ASCII, Hex, Binary The project requires that at some point you XOR two given strings. These strings can be in ASCII, HEX, or Binary. The original strings are provided in HEX format. Feel free to convert, or not covert, between formats if it makes it easier Length and padding An XOR is ,typically, done between two objects of the same length. You will notice that no two hex strings provided are the same length. Depending on the language used, there may or may not, be a third party library that will deal with this for you using padding. In either case, padding can either precede or come after that actual content. Note: 54686520736b792069732066616c6c696e67 XOR 4974206973206e6f740a0000000000000000 Does not equal 54686520736b792069732066616c6c696e67 XOR 00000000000000004974206973206e6f740a
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


