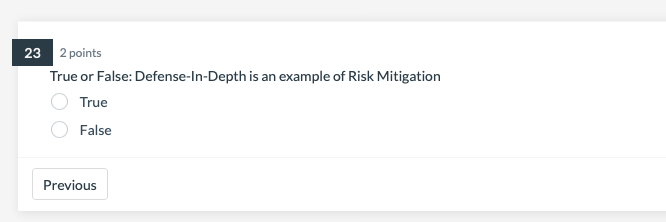
Question: Need help with these problems ASAP! 2 points True or False: Defense-In-Depth is an example of Risk Mitigation True False 4 points Risk management programs
Need help with these problems ASAP!
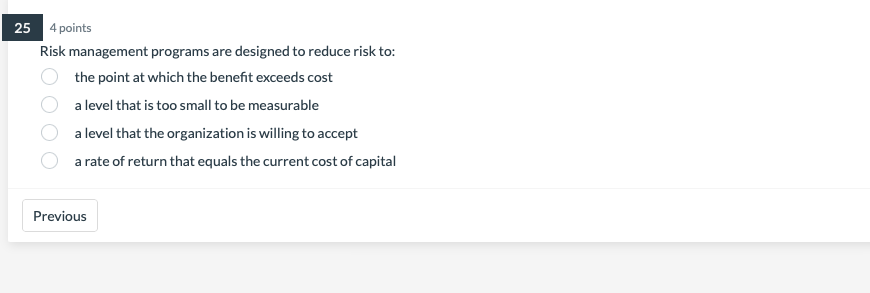
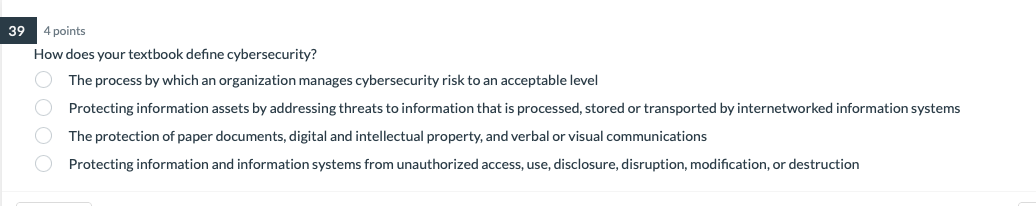
2 points True or False: Defense-In-Depth is an example of Risk Mitigation True False 4 points Risk management programs are designed to reduce risk to: the point at which the benefit exceeds cost a level that is too small to be measurable a level that the organization is willing to accept a rate of return that equals the current cost of capital 4 points How does your textbook define cybersecurity? The process by which an organization manages cybersecurity risk to an Protecting information assets by addressing threats to information that is processed, stored or transported by internetworked information systems The protection of paper documents, digital and intellectual property, and verbal or visual communications Protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


