Question: Need help with this one, especially #3. I've seen some say this is usage and auditing review, while others say off-boarding procedures. Please explain. A
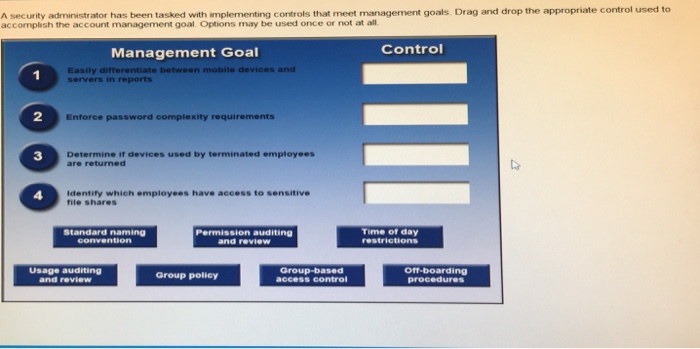
Need help with this one, especially #3. I've seen some say this is usage and auditing review, while others say off-boarding procedures. Please explain.
A security administrator has been tasked with plementing controls that meet management goals Drag and drop the appropriate control used to accomplish the account management goal Options may be used once or not at all Control Management Goal Easily diferentiate between mobile devices and servers in reports Enforce password complexity requirements Determine if devices used by terminated employees are returned Identity which employees have access to sensitive file shares Standard naming convention Permission auditing and review Time of day restrictions Usage auditing and review Group policy Group-based access control Of boarding procedures A security administrator has been tasked with plementing controls that meet management goals Drag and drop the appropriate control used to accomplish the account management goal Options may be used once or not at all Control Management Goal Easily diferentiate between mobile devices and servers in reports Enforce password complexity requirements Determine if devices used by terminated employees are returned Identity which employees have access to sensitive file shares Standard naming convention Permission auditing and review Time of day restrictions Usage auditing and review Group policy Group-based access control Of boarding procedures
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


