Question: Nelson is using the basic Schnorr identification scheme to remotely log into his home computer which has stored the values of p, o and a
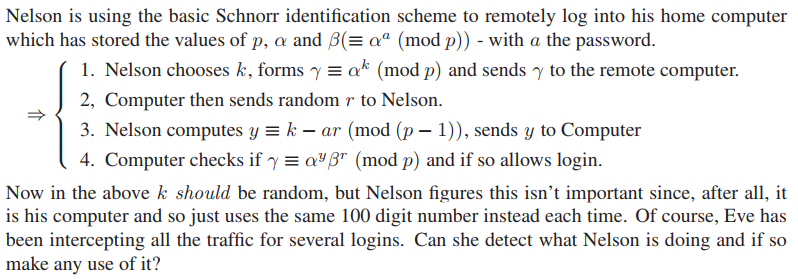
Nelson is using the basic Schnorr identification scheme to remotely log into his home computer which has stored the values of p, o and a (mod p)) -with a the password. I. Nelson chooses k, forms ok (mod p) and sends to the remote computer. 2, Computer then sends random r to Nelson. 3. Nelson computes y k-ar (mod (p-1), sends y to Computer 4. Computer checks if (mod p) and if so allows login. Now in the above k should be random, but Nelson figures this isn't important since, after all, it is his computer and so just uses the same 100 digit number instead each time. Of course, Eve has been intercepting all the traffic for several logins. Can she detect what Nelson is doing and if so make any use of it? Nelson is using the basic Schnorr identification scheme to remotely log into his home computer which has stored the values of p, o and a (mod p)) -with a the password. I. Nelson chooses k, forms ok (mod p) and sends to the remote computer. 2, Computer then sends random r to Nelson. 3. Nelson computes y k-ar (mod (p-1), sends y to Computer 4. Computer checks if (mod p) and if so allows login. Now in the above k should be random, but Nelson figures this isn't important since, after all, it is his computer and so just uses the same 100 digit number instead each time. Of course, Eve has been intercepting all the traffic for several logins. Can she detect what Nelson is doing and if so make any use of it
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


