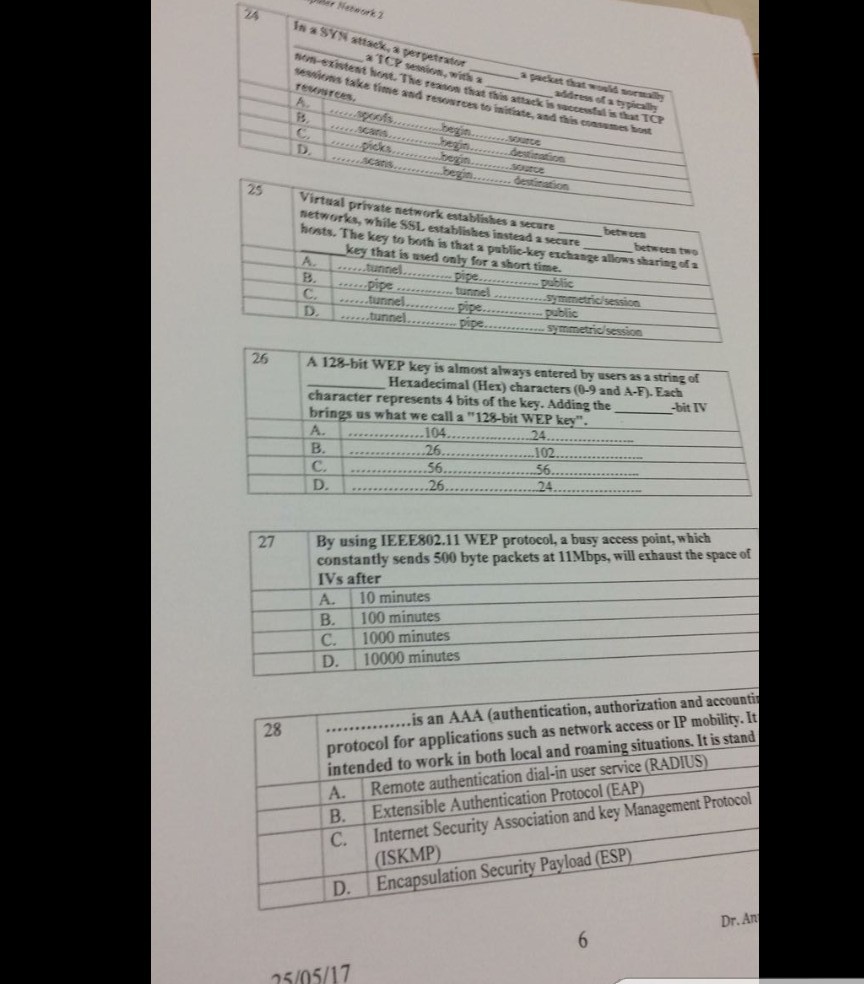
Question: network q In a SYN attack, a perpetrator ___ a packet that would ___ a TCP sessions, with a ___ address of a typically -existent
network q
In a SYN attack, a perpetrator ___ a packet that would ___ a TCP sessions, with a ___ address of a typically -existent host. The season that this attack is successful is that TCP sessions take time and resources to initiate and this consumes host resources. A. ......spoofs........begin.......source B. .....scans.........begin........destination C. ......picks........begin........source D. ......scans........begin........destination Virtual private network establishes a secure ____ between networks, while SSI, establishes instead a secure ___ between two hosts. The key to both is that a public-key exchange allows staring of a ___ key that is used only for a short time. A. ......tunnel........pipe........public B. ......pipe........tunnel........symmetric/session C. ......tunnel........pipe........public D. ......tunnel........pipe........symmetric/session A 128-bit WEP key is almost always entered by users as a string of ____ Hexadecimal (Hex) characters (0-9 and A-F). Each character represents 4 bits of the key. Adding the ___ -bit IV brings us what we call a "128-bit WEP key". A. .......104.........24........ B. .......26.........102........ C. ........56.........56........ D. ........26.........24........ A. 10 minutes B. 100 minutes C. 1000 minutes D. 10000 minutes
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


