Question: Networking The Internet is a(n) 1) core ISP O2) access ISP 3) content provider network 4) network of networks Question 2 (1 point) Suppose a
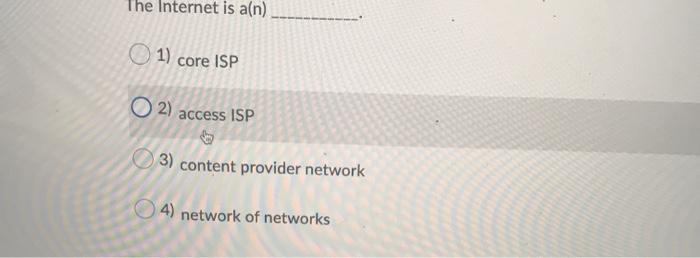
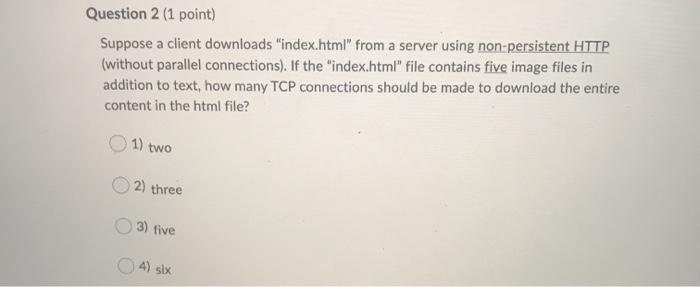

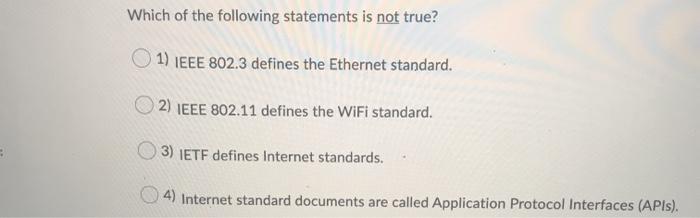
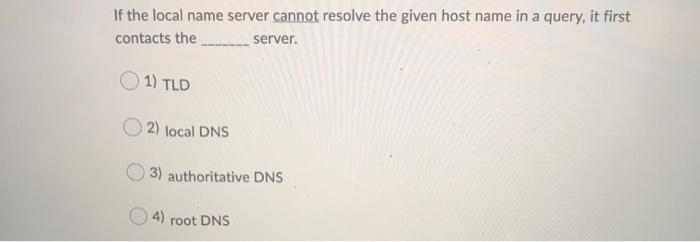


The Internet is a(n) 1) core ISP O2) access ISP 3) content provider network 4) network of networks Question 2 (1 point) Suppose a client downloads "index.html" from a server using non-persistent HTTP (without parallel connections). If the "index.html" file contains five image files in addition to text, how many TCP connections should be made to download the entire content in the html file? 1) two 2) three 3) five 4) six Which of the following statements is not true? 1) Both clients and servers are always on in the client-server architecture. 2) In the peer-to-peer architecture, there is minimal reliance on dedicated servers in data centers. 3) The peer-to-peer architecture has a property of self-scalability. 4) In the client-server architecture, clients communicate directly with one or more convers Which of the following statements is not true? 1) IEEE 802.3 defines the Ethernet standard. 2) IEEE 802.11 defines the WiFi standard. 3) IETF defines Internet standards. 4) Internet standard documents are called Application Protocol Interfaces (APIs). If the local name server cannot resolve the given host name in a query, it first contacts the server. 1) TLD 2) local DNS 3) authoritative DNS 4) root DNS Which of the following statements is not true? 1) Today's computer networks utilize circuit switching for reliable data exchange. 2) The Internet relies on packet switching for forwarding packets. Unsaved 3) A circuit in a link is implemented with either FDM or TDM. 4) Packet switches typically use store-and-forward transmission at the inputs to the links. establishes a number of half-open or fully open TCP connections at the target host 1) Bandwidth flooding on 2 Urvsaved 2) Connection flooding 3) Vulnerability attack 4) Sniffing attack Consider two hosts, A and B, connected by a single link of rate p bps. Suppose that the two hosts are separated by a meters, and suppose the signal propagation speed along the link is r meter/sec. Host A is to send a packet of size s bits to Host B. What is the propagation delay? 2: 11 a/ 2) pls 3) / 04 5/1
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


