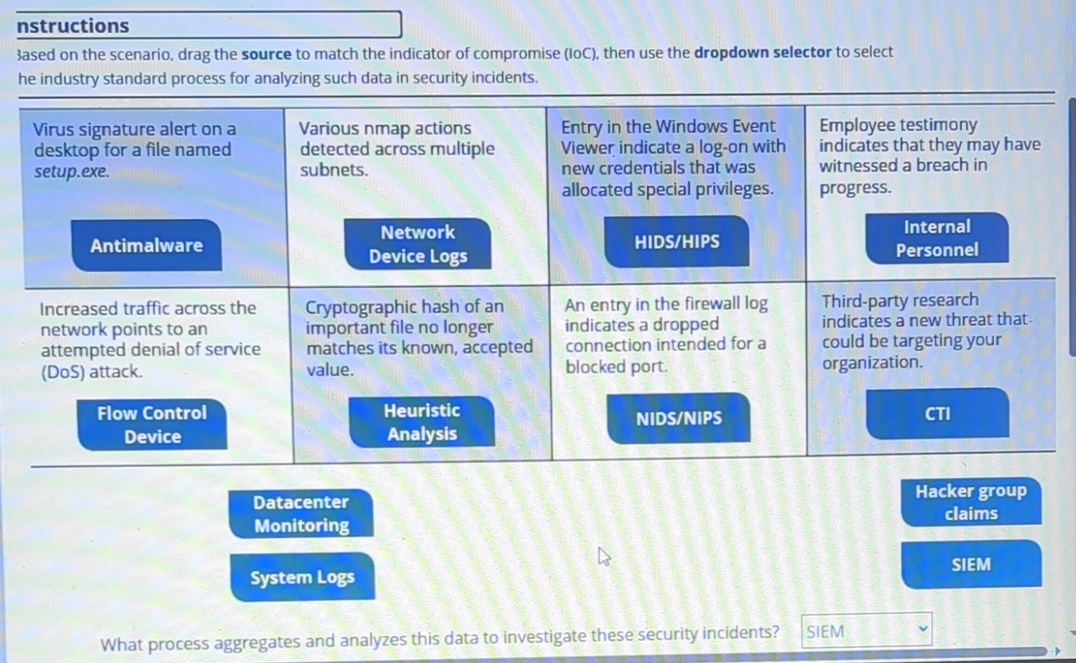
Question: nstructions 3 ased on the scenario, drag the source to match the indicator of compromise ( 1 0 C ) , then use the dropdown
nstructions
ased on the scenario, drag the source to match the indicator of compromise C then use the dropdown selector to select he industry standard process for analyzing such data in security incidents.
tableVirus signature alert on a desktop for a file named setup.exe.,tableVarious nmap actions detected across multiple subnets.Network Device LogsEntry in the Windows Event Viewer indicate a logon with new credentials that was allocated special privileges.,tableEmployee testimony indicates that they may have witnessed a breach in progress.InternalPersonnelIncreased traffic across the network points to an attempted denial of service DoS attack.,Cryptographic hash of an important file no longer matches its known, accepted value.,An entry in the firewall log indicates a dropped connection intended for a blocked port.,Thirdparty research indicates a new threat thatcould be targeting your organization.tableHeuristicAnalysis
What process aggregates and analyzes this data to investigate these security incidents?
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


