Question: Objective: Upon completion of this activity, you will be able to explain how the SHA-514 algorithm uses one-way functions to make it impossible to compute
Objective: Upon completion of this activity, you will be able to explain how the SHA-514 algorithm uses one-way functions to make it impossible to compute the inverse function thereby implementing the one-way property required of all cryptographic hash functions.
Student Instructions: 1. Read the section on the SHA-514 round function on page 346 of the William Stallings textbook (Cryptography and Network Security Principles and Practice Fifth Edition William Stallings). Then do the exercises given below.
Answer: The majority function MAJ(a,b,c) will return 0 if at least two out of the three values of a, b, and c are 0. The majority function MAJ(a,b,c) will return 1 if at least two out of the three values of a, b, and c are 1. MAJ(a,b,c): the majority function is true only of the majority (two or three) of the arguments are true. COND(a,b,c) (conditional function) will return b if a=1 or c if a=o. In other words: "If a then b else c". Please fill in the following tables showing how SHA-514 computes the MAJ and COND functions.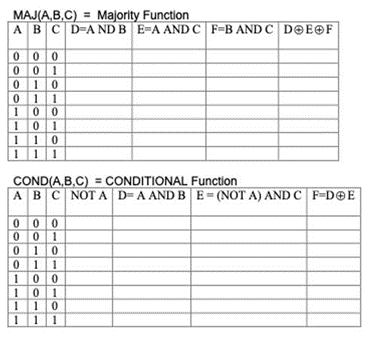
MAJ(A,B,C)=Majority Function \begin{tabular}{|l|l|l|l|l|l|l|} \hline A & B & C & D=A ND B & E=A AND C & F=B AND C & DEF \\ \hline 0 & 0 & 0 & & & & \\ \hline 0 & 0 & 1 & & & & \\ \hline 0 & 1 & 0 & & & & \\ \hline 0 & 1 & 1 & & & & \\ \hline 1 & 0 & 0 & & & & \\ \hline 1 & 0 & 1 & & & & \\ \hline 1 & 1 & 0 & & & & \\ \hline 1 & 1 & 1 & & & \\ \hline \end{tabular} COND(A,B,C)=CONDITIONAL Function \begin{tabular}{|l|l|l|l|l|l|l|} \hline A & B & C & NOT A & D=A AND B & E=(NOTA)ANDC & F=DE \\ \hline 0 & 0 & 0 & & & & \\ \hline 0 & 0 & 1 & & & & \\ \hline 0 & 1 & 0 & & & & \\ \hline 0 & 1 & 1 & & & & \\ \hline 1 & 0 & 0 & & & & \\ \hline 1 & 0 & 1 & & & & \\ \hline 1 & 1 & 0 & & & & \\ \hline 1 & 1 & 1 & & & & \\ \hline \end{tabular}
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


