Question: Old MathJax webview Old MathJax webview Old MathJax webview I edited and add new informations to make it very clear I submitted it all again,
Old MathJax webview



I edited and add new informations to make it very clear
I submitted it all again, read from page after the previous submission
It's repeated because I submitted again ignor the first three pages. I can't delete the previous submission.
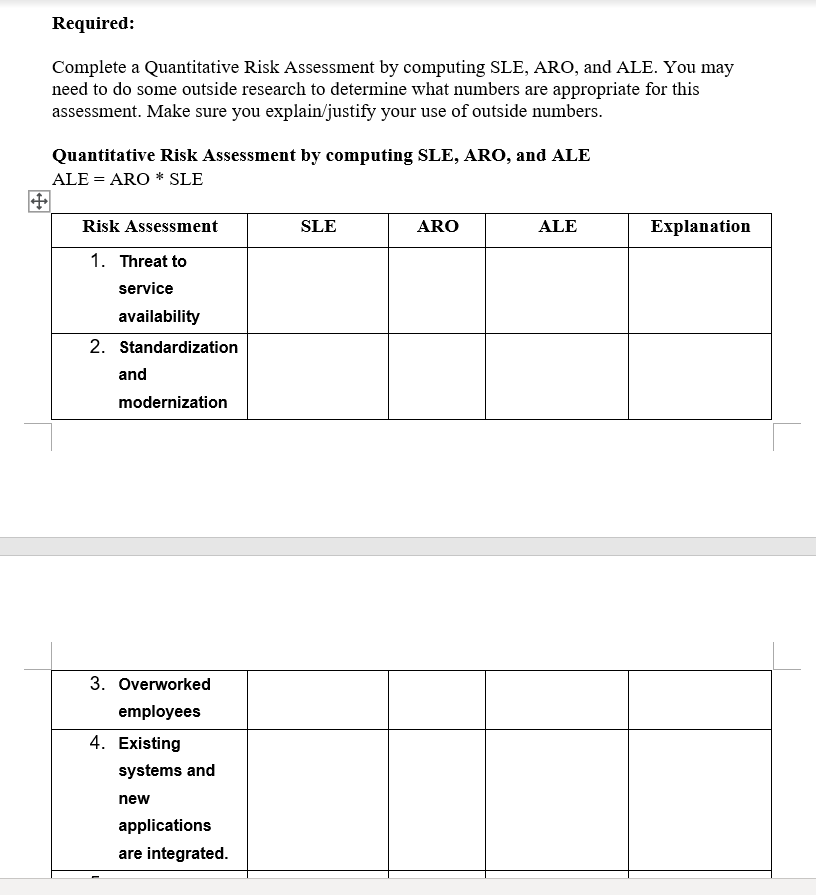
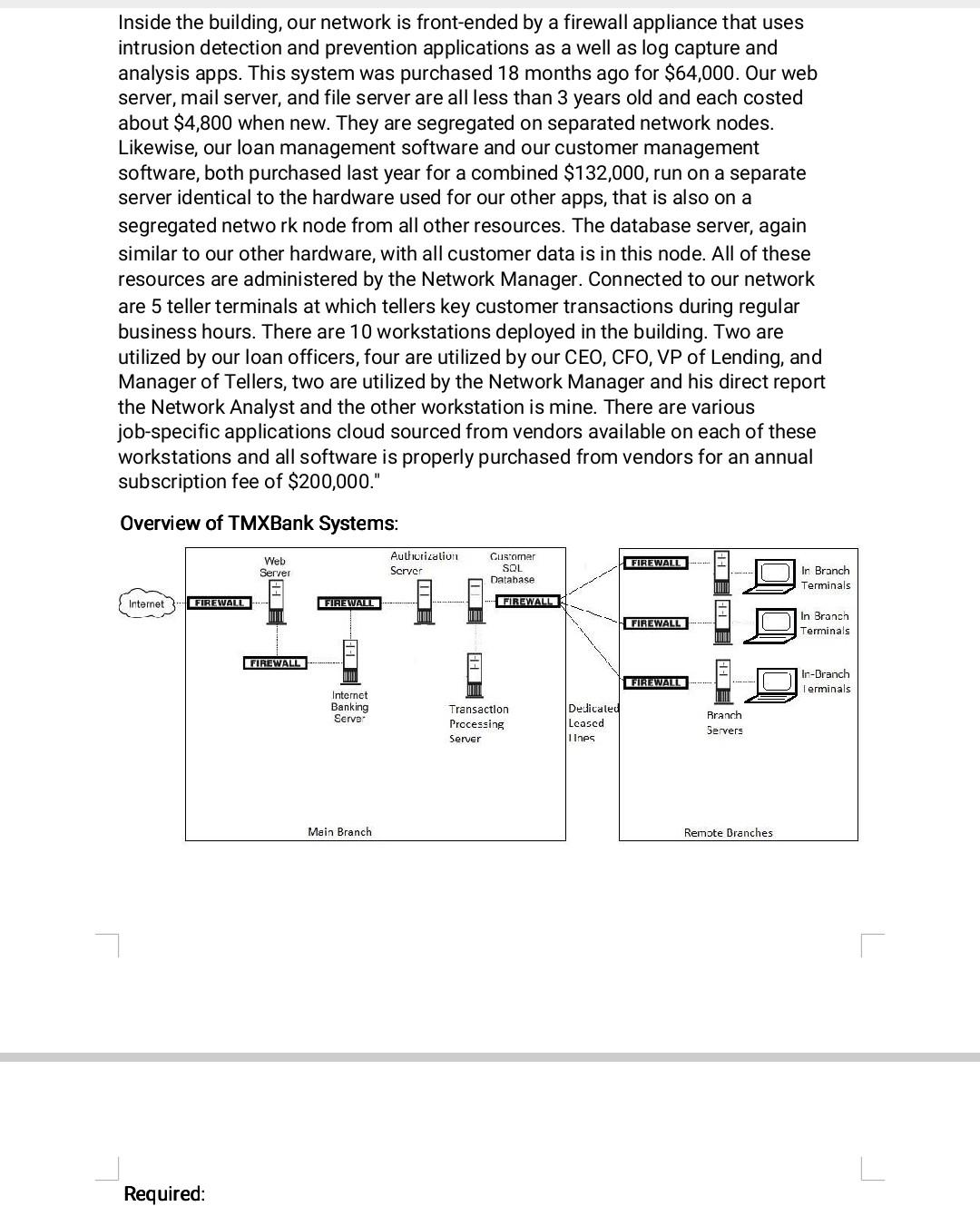
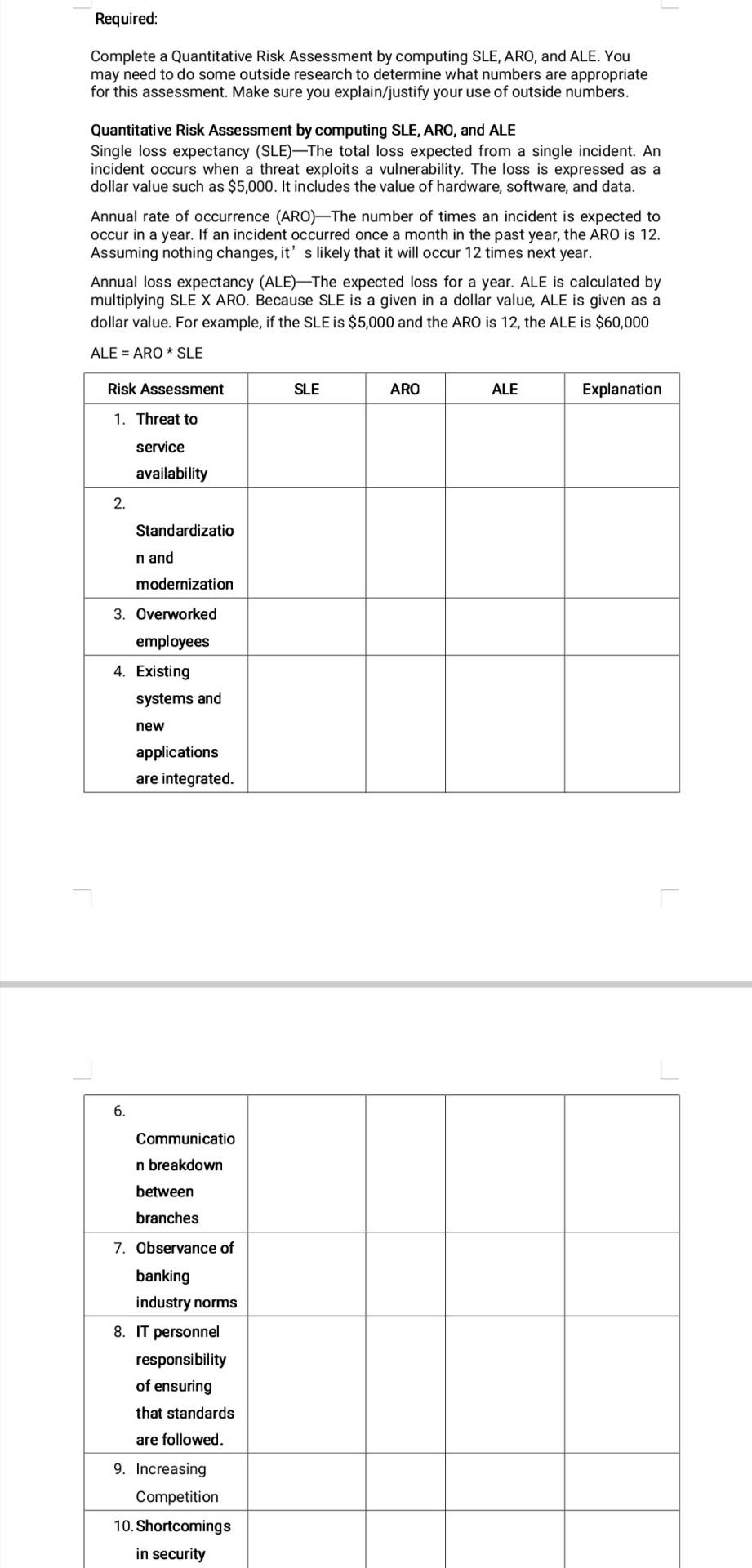
TRM Bank Executive Summary: The scope of this project includes an overview of the bank's assets, threats and vulnerabilities, and the prioritization of risks. The asset register of the TMX Bank details the various assets and risks that the institution is exposed to. The asset register also identifies the type and source of the threats that the bank is facing. Vulnerabilities register is a list of critical weaknesses that could allow an attacker to take over or disrupt the operations of a bank. During the course of the project, the team identified various risk types that the bank is exposed to. Some of these included the compliance requirements due to the bank's growth, supporting the functionality of the acquired smaller banks, and the staffing issues. The following pages detail the various risks that are associated with certain issues that are listed and ranked in order to help the TMX Bank assess their potential. One of the most significant risks that the TMX Bank has is compliance. As a result, it is very likely that it will be subjected to the scrutiny of the authorities, which could result in fines and the complete shutdown of its operations. It is very important that the TMX Bank takes the necessary steps to ensure that it is meeting the standards of its industry. Due to the complexity of the TMX Bank's core banking systems, the staff members are stretched to the limit in their efforts to support them. The skilled staff members tasked with overseeing the legacy systems are also harder to find. The TMX Bank's core banking systems need to be continuously updated and modernized in order to meet the requirements of the industry. This includes addressing the availability of systems and the integration of the various applications. The increasing workload and responsibilities of IT staff members for compliance could result in a rush of 2-week notices and a lower performance of the bank. A full-time compliance professional is needed to ensure that the due diligence process is carried out properly and that all documentation is in place. Required: Complete a Quantitative Risk Assessment by computing SLE, ARO, and ALE. You may need to do some outside research to determine what numbers are appropriate for this assessment. Make sure you explain/justify your use of outside numbers. Quantitative Risk Assessment by computing SLE, ARO, and ALE AID-ADO * SID Required: Complete a Quantitative Risk Assessment by computing SLE, ARO, and ALE. You may need to do some outside research to determine what numbers are appropriate for this assessment. Make sure you explain/justify your use of outside numbers. Quantitative Risk Assessment by computing SLE, ARO, and ALE ALE = ARO * SLE Risk Assessment SLE ARO ALE Explanation 1. Threat to service availability 2. Standardization and modernization 3. Overworked employees 4. Existing systems and new applications are integrated. 3. Overworked employees 4. Existing systems and new applications are integrated. 5. Communication breakdown between branches 6. Observance of banking industry norms 7. IT personnel responsibility of ensuring that standards are followed. 8. Increasing Competition 9. Shortcomings in security standards 10. Reputational Damage TMR Bank Executive Summary TMXBank, Inc. is a profitable regional financial institution with more than $1.2 billion of controlled assets that serves a three-state area in the Southeastern USA. In the last several years, the bank has facilitated growth through the acquisition of small local banks to create a broader geographic presence. In recent strategy mapping sessions, the leadership of TMXBank identified several strategic initiatives it seeks to pursue - 1) continue growth, 2) reduce cost, and 3) improve efficiency of operations. Business Challenges Core banking systems require modernization. a. TMXBank cannot adequately support the functionality of banks it acquired. Staff are stretched to the limit in their efforts to support the disparate systems. b. From a technology viewpoint, integrating the core banking systems with new applications is complex, and the skill set that is needed to maintain the legacy core systems is becoming harder to find. c. See the attached Overview of TMXBank's systems There are concerns regarding compliance. d. There are concerns about TMXBank' s ability to comply with industry regulations. As the bank has grown it has become subject to additional banking regulations. e. With the continued growth of the bank, the IT staff has become responsible for regulation compliance for which the bank is now accountable. Narrative below is from your discussion with the bank VP of IT. "For all of our core banking account transactions, we run our new $4 million banking app suite on a multi-core transaction processing server that we paid $64,000 on our network that is segregated from all other network nodes and is backed up transaction-by-transaction instantly to two off-site mirror servers. These servers are supported by our 3rd party disaster recovery vendor at an annual cost of $125,000 per year. These connections are facilitated by two dedicated leased lines that are provided by the vendor. The first server is our redundancy server. If our primary server on site is unavailable the redundant mirror can instantly function as a replacement for the primary server for as long as required. The second off-site mirror is a disaster recovery server. Its primary use is to restore data in the event that the primary transaction process server has a data loss. In the event of multiple failures of the primary and redundant servers, this server could be employed for transaction processing as well. Inside the building, our network is front-ended by a firewall appliance that uses intrusion detection and prevention applications as a well as log capture and analysis apps. This system was purchased 18 months ago for $64,000. Our web server, mail server, and file server are all less than 3 years old and each costed about $4,800 when new. They are segregated on separated network nodes. Likewise, our loan management software and our customer management software, both purchased last year for a combined $132,000, run on a separate server identical to the hardware used for our other apps, that is also on a segregated network node from all other resources. The database server, again similar to our other hardware, with all customer data is in this node. All of these resources are administered by the Network Manager. Connected to our network are 5 teller terminals at which tellers key customer transactions during regular business hours. There are 10 workstations deployed in the building. Two are utilized by our loan officers, four are utilized by our CEO, CFO, VP of Lending, and Manager of Tellers, two are utilized by the Network Manager and his direct report the Network Analyst and the other workstation is mine There are various Inside the building, our network is front-ended by a firewall appliance that uses intrusion detection and prevention applications as a well as log capture and analysis apps. This system was purchased 18 months ago for $64,000. Our web server, mail server, and file server are all less than 3 years old and each costed about $4,800 when new. They are segregated on separated network nodes. Likewise, our loan management software and our customer management software, both purchased last year for a combined $132,000, run on a separate server identical to the hardware used for our other apps, that is also on a segregated network node from all other resources. The database server, again similar to our other hardware, with all customer data is in this node. All of these resources are administered by the Network Manager. Connected to our network are 5 teller terminals at which tellers key customer transactions during regular business hours. There are 10 workstations deployed in the building. Two are utilized by our loan officers, four are utilized by our CEO, CFO, VP of Lending, and Manager of Tellers, two are utilized by the Network Manager and his direct report the Network Analyst and the other workstation is mine. There are various job-specific applications cloud sourced from vendors available on each of these workstations and all software is properly purchased from vendors for an annual subscription fee of $200,000." Overview of TMXBank Systems: Web Server Authorization Server Customer SOL Database FIREWALL In Branch Terminals Internet FIREWALL FIREWAT FIREWALL FIREWALL In Branch Terminals FIREWALL FIREWALL In-Branch Terminals Internet Banking Serve Transaction Processing Server Dedicated Leased 1 Ines Branch Servers Main Branch Remote Branches Required: Required: Complete a Quantitative Risk Assessment by computing SLE, ARO, and ALE. You may need to do some outside research to determine what numbers are appropriate for this assessment. Make sure you explain/justify your use of outside numbers. Quantitative Risk Assessment by computing SLE, ARO, and ALE Single loss expectancy (SLE)-The total loss expected from a single incident. An incident occurs when a threat exploits a vulnerability. The loss is expressed as a dollar value such as $5,000. It includes the value of hardware, software, and data. Annual rate of occurrence (ARO)-The number of times an incident is expected to occur in a year. If an incident occurred once a month in the past year, the ARO is 12. Assuming nothing changes, it's likely that it will occur 12 times next year. Annual loss expectancy (ALE)-The expected loss for a year. ALE is calculated by multiplying SLE X ARO. Because SLE is a given in a dollar value, ALE is given as a dollar value. For example, if the SLE is $5,000 and the ARO is 12, the ALE is $60,000 ALE = ARO* SLE Risk Assessment SLE ARO ALE Explanation 1. Threat to service availability 2. Standardizatio n and modernization 3. Overworked employees 4. Existing systems and new applications are integrated. 6. Communicatio n breakdown between branches 7. Observance of banking industry norms 8. IT personnel responsibility of ensuring that standards are followed. 9. Increasing Competition 10. Shortcomings in security TRM Bank Executive Summary: The scope of this project includes an overview of the bank's assets, threats and vulnerabilities, and the prioritization of risks. The asset register of the TMX Bank details the various assets and risks that the institution is exposed to. The asset register also identifies the type and source of the threats that the bank is facing. Vulnerabilities register is a list of critical weaknesses that could allow an attacker to take over or disrupt the operations of a bank. During the course of the project, the team identified various risk types that the bank is exposed to. Some of these included the compliance requirements due to the bank's growth, supporting the functionality of the acquired smaller banks, and the staffing issues. The following pages detail the various risks that are associated with certain issues that are listed and ranked in order to help the TMX Bank assess their potential. One of the most significant risks that the TMX Bank has is compliance. As a result, it is very likely that it will be subjected to the scrutiny of the authorities, which could result in fines and the complete shutdown of its operations. It is very important that the TMX Bank takes the necessary steps to ensure that it is meeting the standards of its industry. Due to the complexity of the TMX Bank's core banking systems, the staff members are stretched to the limit in their efforts to support them. The skilled staff members tasked with overseeing the legacy systems are also harder to find. The TMX Bank's core banking systems need to be continuously updated and modernized in order to meet the requirements of the industry. This includes addressing the availability of systems and the integration of the various applications. The increasing workload and responsibilities of IT staff members for compliance could result in a rush of 2-week notices and a lower performance of the bank. A full-time compliance professional is needed to ensure that the due diligence process is carried out properly and that all documentation is in place. Required: Complete a Quantitative Risk Assessment by computing SLE, ARO, and ALE. You may need to do some outside research to determine what numbers are appropriate for this assessment. Make sure you explain/justify your use of outside numbers. Quantitative Risk Assessment by computing SLE, ARO, and ALE AID-ADO * SID Required: Complete a Quantitative Risk Assessment by computing SLE, ARO, and ALE. You may need to do some outside research to determine what numbers are appropriate for this assessment. Make sure you explain/justify your use of outside numbers. Quantitative Risk Assessment by computing SLE, ARO, and ALE ALE = ARO * SLE Risk Assessment SLE ARO ALE Explanation 1. Threat to service availability 2. Standardization and modernization 3. Overworked employees 4. Existing systems and new applications are integrated. 3. Overworked employees 4. Existing systems and new applications are integrated. 5. Communication breakdown between branches 6. Observance of banking industry norms 7. IT personnel responsibility of ensuring that standards are followed. 8. Increasing Competition 9. Shortcomings in security standards 10. Reputational Damage TMR Bank Executive Summary TMXBank, Inc. is a profitable regional financial institution with more than $1.2 billion of controlled assets that serves a three-state area in the Southeastern USA. In the last several years, the bank has facilitated growth through the acquisition of small local banks to create a broader geographic presence. In recent strategy mapping sessions, the leadership of TMXBank identified several strategic initiatives it seeks to pursue - 1) continue growth, 2) reduce cost, and 3) improve efficiency of operations. Business Challenges Core banking systems require modernization. a. TMXBank cannot adequately support the functionality of banks it acquired. Staff are stretched to the limit in their efforts to support the disparate systems. b. From a technology viewpoint, integrating the core banking systems with new applications is complex, and the skill set that is needed to maintain the legacy core systems is becoming harder to find. c. See the attached Overview of TMXBank's systems There are concerns regarding compliance. d. There are concerns about TMXBank' s ability to comply with industry regulations. As the bank has grown it has become subject to additional banking regulations. e. With the continued growth of the bank, the IT staff has become responsible for regulation compliance for which the bank is now accountable. Narrative below is from your discussion with the bank VP of IT. "For all of our core banking account transactions, we run our new $4 million banking app suite on a multi-core transaction processing server that we paid $64,000 on our network that is segregated from all other network nodes and is backed up transaction-by-transaction instantly to two off-site mirror servers. These servers are supported by our 3rd party disaster recovery vendor at an annual cost of $125,000 per year. These connections are facilitated by two dedicated leased lines that are provided by the vendor. The first server is our redundancy server. If our primary server on site is unavailable the redundant mirror can instantly function as a replacement for the primary server for as long as required. The second off-site mirror is a disaster recovery server. Its primary use is to restore data in the event that the primary transaction process server has a data loss. In the event of multiple failures of the primary and redundant servers, this server could be employed for transaction processing as well. Inside the building, our network is front-ended by a firewall appliance that uses intrusion detection and prevention applications as a well as log capture and analysis apps. This system was purchased 18 months ago for $64,000. Our web server, mail server, and file server are all less than 3 years old and each costed about $4,800 when new. They are segregated on separated network nodes. Likewise, our loan management software and our customer management software, both purchased last year for a combined $132,000, run on a separate server identical to the hardware used for our other apps, that is also on a segregated network node from all other resources. The database server, again similar to our other hardware, with all customer data is in this node. All of these resources are administered by the Network Manager. Connected to our network are 5 teller terminals at which tellers key customer transactions during regular business hours. There are 10 workstations deployed in the building. Two are utilized by our loan officers, four are utilized by our CEO, CFO, VP of Lending, and Manager of Tellers, two are utilized by the Network Manager and his direct report the Network Analyst and the other workstation is mine There are various Inside the building, our network is front-ended by a firewall appliance that uses intrusion detection and prevention applications as a well as log capture and analysis apps. This system was purchased 18 months ago for $64,000. Our web server, mail server, and file server are all less than 3 years old and each costed about $4,800 when new. They are segregated on separated network nodes. Likewise, our loan management software and our customer management software, both purchased last year for a combined $132,000, run on a separate server identical to the hardware used for our other apps, that is also on a segregated network node from all other resources. The database server, again similar to our other hardware, with all customer data is in this node. All of these resources are administered by the Network Manager. Connected to our network are 5 teller terminals at which tellers key customer transactions during regular business hours. There are 10 workstations deployed in the building. Two are utilized by our loan officers, four are utilized by our CEO, CFO, VP of Lending, and Manager of Tellers, two are utilized by the Network Manager and his direct report the Network Analyst and the other workstation is mine. There are various job-specific applications cloud sourced from vendors available on each of these workstations and all software is properly purchased from vendors for an annual subscription fee of $200,000." Overview of TMXBank Systems: Web Server Authorization Server Customer SOL Database FIREWALL In Branch Terminals Internet FIREWALL FIREWAT FIREWALL FIREWALL In Branch Terminals FIREWALL FIREWALL In-Branch Terminals Internet Banking Serve Transaction Processing Server Dedicated Leased 1 Ines Branch Servers Main Branch Remote Branches Required: Required: Complete a Quantitative Risk Assessment by computing SLE, ARO, and ALE. You may need to do some outside research to determine what numbers are appropriate for this assessment. Make sure you explain/justify your use of outside numbers. Quantitative Risk Assessment by computing SLE, ARO, and ALE Single loss expectancy (SLE)-The total loss expected from a single incident. An incident occurs when a threat exploits a vulnerability. The loss is expressed as a dollar value such as $5,000. It includes the value of hardware, software, and data. Annual rate of occurrence (ARO)-The number of times an incident is expected to occur in a year. If an incident occurred once a month in the past year, the ARO is 12. Assuming nothing changes, it's likely that it will occur 12 times next year. Annual loss expectancy (ALE)-The expected loss for a year. ALE is calculated by multiplying SLE X ARO. Because SLE is a given in a dollar value, ALE is given as a dollar value. For example, if the SLE is $5,000 and the ARO is 12, the ALE is $60,000 ALE = ARO* SLE Risk Assessment SLE ARO ALE Explanation 1. Threat to service availability 2. Standardizatio n and modernization 3. Overworked employees 4. Existing systems and new applications are integrated. 6. Communicatio n breakdown between branches 7. Observance of banking industry norms 8. IT personnel responsibility of ensuring that standards are followed. 9. Increasing Competition 10. Shortcomings in securityStep by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


