Once your code is complete, you may proceed to the Submit Lab 7B link in which you will attach your coding project. Please note that because this project consists of a Windows Form GUI you must provide a zip of the entire project directory.
Also note that you will not be turning in this lab during this lab week, rather you will spend two weeks working on it.
The objectives of this lab assignment are as follows:
Develop a Windows Forms Graphical User Interface (GUI).
Work with 2D arrays.
Work with strings, treating them arrays.
Create an application that demonstrates the use of methods.
Assignment User Story: As a user I want a new Windows application that is capable of performing encryption and decryption using a modified Playfair Cipher.
Acceptance Criteria:
A Windows Forms GUI will be developed.
Required controls are text boxes: one for the cipher key, one for the string that is to be either encrypted or dencrypted, and one for the result of that operation.
Technical Requirements:
The principle logic of this application will be handled via methods and 2D arrays. Specifically, you will construct a 2D array that is comprised of the text key (key word for the cipher) and then the remaining letters of the alphabet with no duplicated letters. This array will be a 5x5 array (5 rows and 5 columns).
This application should be broken down into methods to perform most of the operations needed (this is to say that the majority of the code should not be present in the button's event handler.
Background:
"For two thousand years,codemakershave fought to preserve secrets whilecodebreakershave tried their best to reveal them." - taken from The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography by Simon Singh.
The idea for this problem comes from this book.You will encrypt and decrypt some messages using a simplified version of a code in the book. The convention in cryptography is to write the plain text in lower case letters and the encrypted text in upper case letters. We will follow this convention for this problem. We will only encrypt/decrypt letters. Any other characters including numbers and punctuation will be left as is (i.e. 1 2 3 . , - etc).
Technical Thoughts and Tips:
This is a modified Playfair Cipher. You can read more about this cipher at Wikipedia.
The method of encryption used here is a simple substitution cipher that depends on the sender and receiver of the message agreeing on a keyword, which is usually just one word that will be easy to remember. Thus the key for decrypting the message will not have to be written down and is less likely to fall into enemy hands!
First, the program must accept a keyword, which will be all capital letters. The letters of the keyword must be inserted in the order in which they occur into a 5x5 two dimensional array by rows, but if a letter is repeated in the keyword it that letter is only used once in the two-dimensional array. Then the array is filled up with the remaining letters of the alphabet in order (excluding the 'Z').e.g. if the keyword was FERRET the array would contain the following:
F E R T A
B C D G H
I/J K L M N
O P Q S U
V W X Y Z
Notice that all 26 letters of the alphabet are represented in this matrix (2D array). But, because this is a 5x5 array we must combine two letters together, and we do this with I and J.
Next, the program will read take the text entered into the Windows form and determine whether that text message will be encrypted or decrypted.
When the text needs to be encrypted you will follow these steps:
Each letter in the message will be found in the table, and the row and column will be noted. Example, 'm' (when converted to upper case) occurs at row 2, column 3 (keep in mind both rows and columns begin at zero).
It will then be encrypted by reversing the row and column values, so that 'm' will become the character at row 3, column 2 i.e. 'Q' in the encrypted message. Thus if the message was "good luck" it will be encrypted as "PTTK LYCD" Spaces between words will be maintained exactly as they appear in the message.
Keep in mind, that if you are dealing with the letters 'I' or 'J' then they are treated as the same letter.
A message that is already encrypted can be decrypted using exactly the same algorithm the only difference is that the incoming message will be in upper case and the decrypted message will be in lower case.
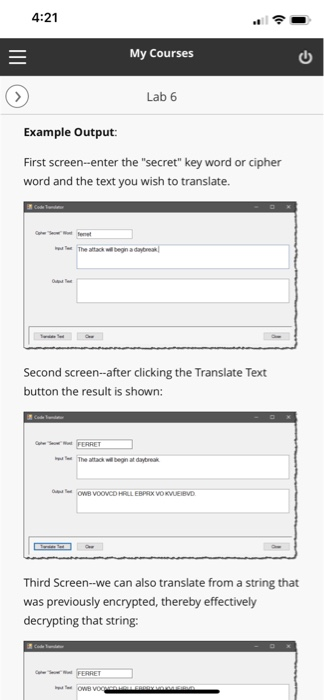
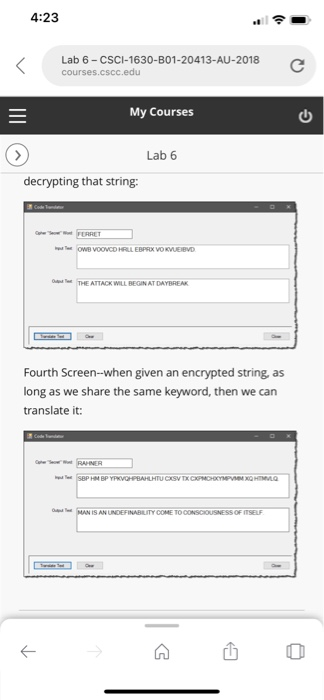
4:21 My Courses Lab 6 Example Output: First screen-enter the "secret" key word or cipher word and the text you wish to translate. Second screen--after clicking the Translate Text button the result is shown: The afack wil begin at daybreak Third Screen-we can also translate from a string that was previously encrypted, thereby effectively decrypting that string