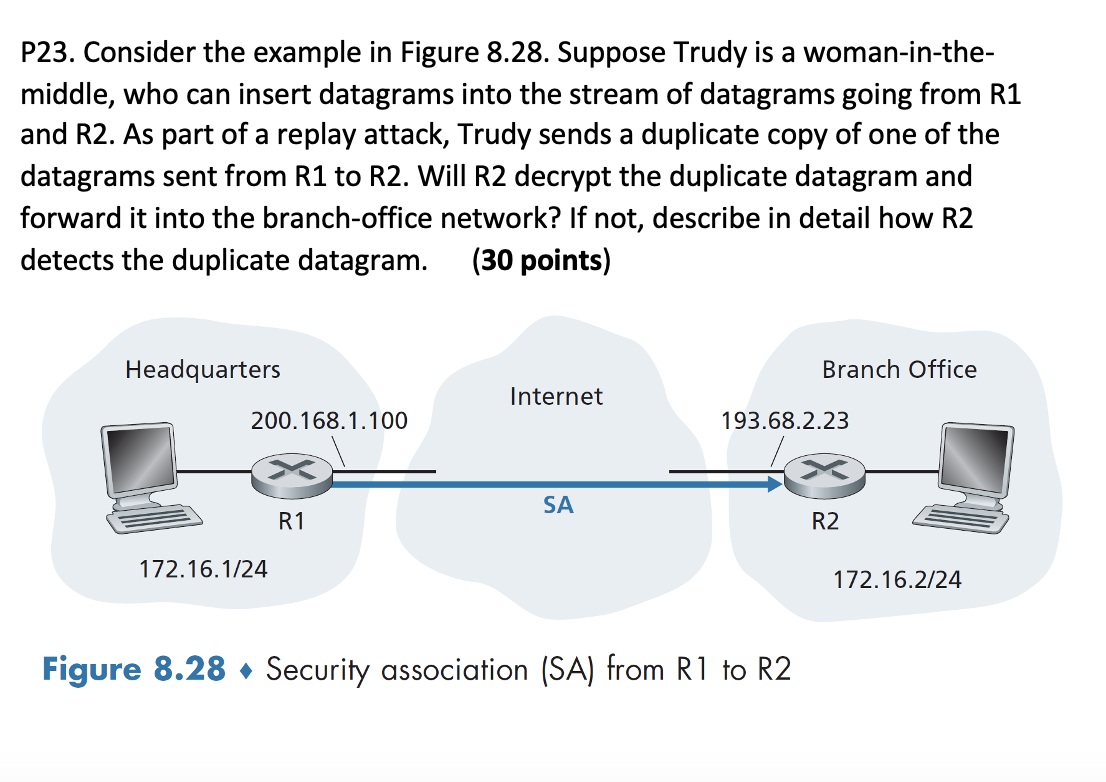
Question: P 2 3 . Consider the example in Figure 8 . 2 8 . Suppose Trudy is a woman - in - themiddle, who can
P Consider the example in Figure Suppose Trudy is a womaninthemiddle, who can insert datagrams into the stream of datagrams going from R and R As part of a replay attack, Trudy sends a duplicate copy of one of the datagrams sent from R to R Will R decrypt the duplicate datagram and forward it into the branchoffice network? If not, describe in detail how R detects the duplicate datagram.
points
Figure Security association from to
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


