Question: Please ANSWER all question for thumbs up. Please ANSWER all question for thumbs up. Which of the following protocols would be used to guarantee the
Please ANSWER all question for thumbs up.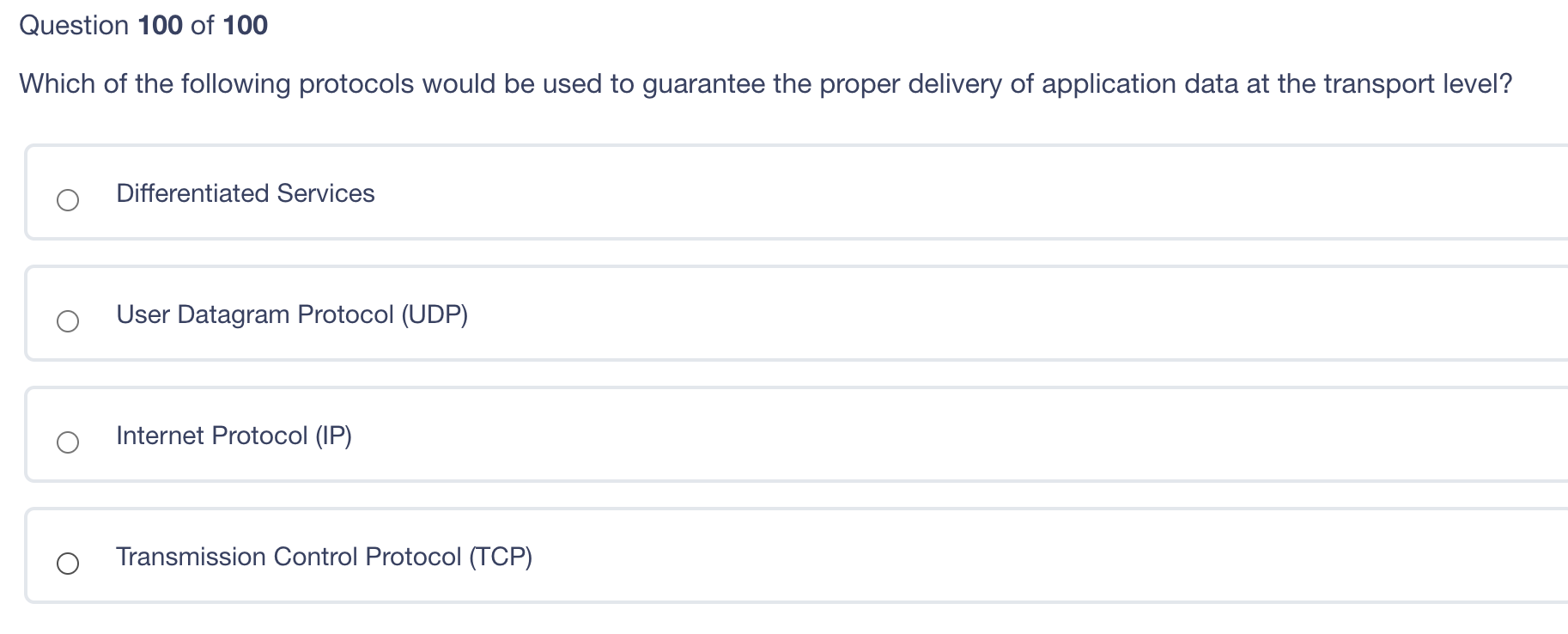
 Please ANSWER all question for thumbs up.
Please ANSWER all question for thumbs up.
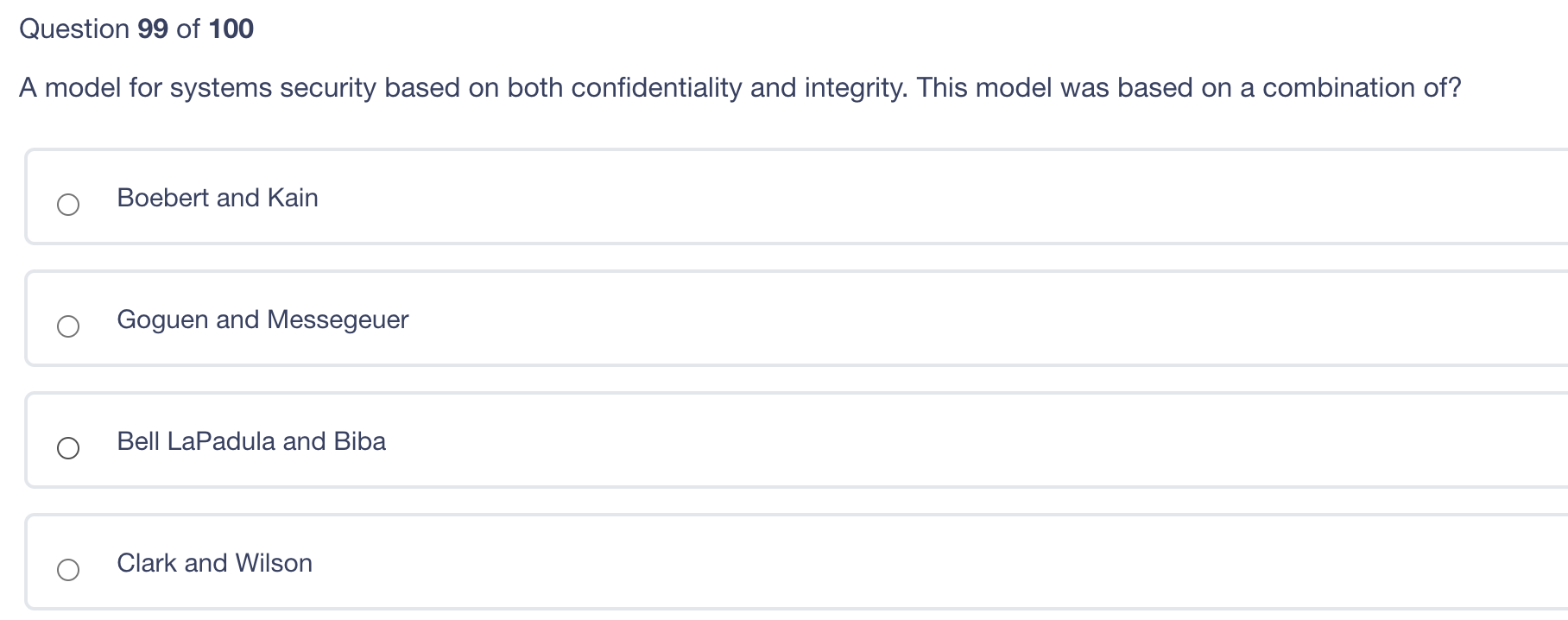
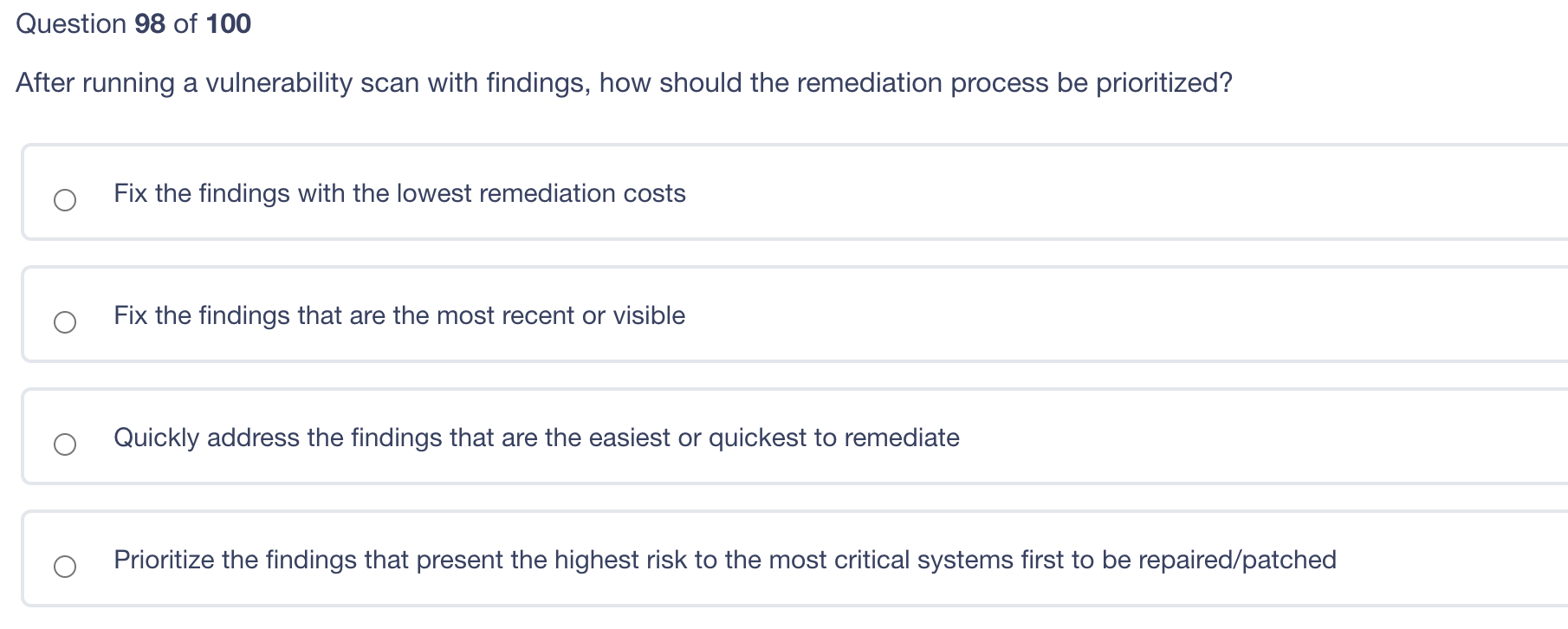
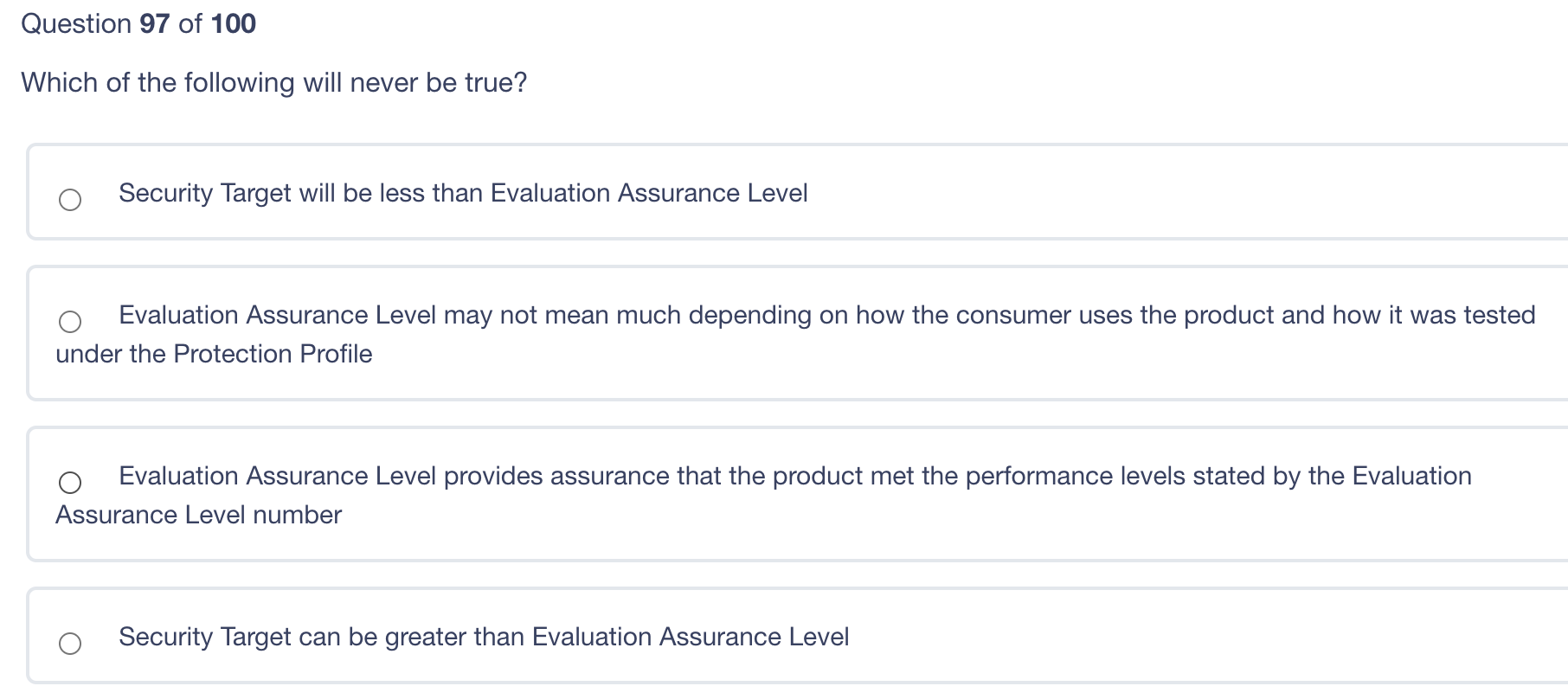
Which of the following protocols would be used to guarantee the proper delivery of application data at the transport level? Differentiated Services User Datagram Protocol (UDP) Internet Protocol (IP) Transmission Control Protocol (TCP) A model for systems security based on both confidentiality and integrity. This model was based on a combination of? Boebert and Kain Goguen and Messegeuer Bell LaPadula and Biba Clark and Wilson Question 98 of 100 After running a vulnerability scan with findings, how should the remediation process be prioritized? Fix the findings with the lowest remediation costs Fix the findings that are the most recent or visible Quickly address the findings that are the easiest or quickest to remediate Prioritize the findings that present the highest risk to the most critical systems first to be repaired/patched Which of the following will never be true? Security Target will be less than Evaluation Assurance Level Evaluation Assurance Level may not mean much depending on how the consumer uses the product and how it was tested under the Protection Profile Evaluation Assurance Level provides assurance that the product met the performance levels stated by the Evaluation Assurance Level number Security Target can be greater than Evaluation Assurance Level Question 96 of 100 A backbone network able to handle nearly full traffic flows when operating at a logical ring due to: It uses CSMA/CD for traffic management It deploys two countermanding rings to allow for failure Its traffic management is deterministic It is scalable and allows the connection of multiple devices to the same network
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


