Question: please answer and explain each question, Asap thanks If Amy uses her private key to encrypt the original message to the cipher text and send
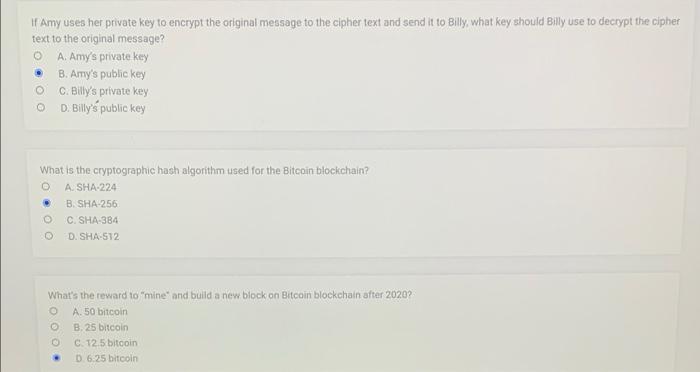
If Amy uses her private key to encrypt the original message to the cipher text and send it to Billy, what key should Billy use to decrypt the cipher text to the original message? o A. Amys private key B. Amy's public key C. Billy's private key D. Billy's public key What is the cryptographic hash algorithm used for the Bitcoin blockchain? A. SHA-224 . B. SHA-256 C. SHA-384 D. SHA-S12 What's the reward to "mine" and build a new block on Bitcoin blockchain after 2020? A. 50 bitcoin B. 25 bitcoin 0 C12.5 bitcoin 0.6.25 bitcoin
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


