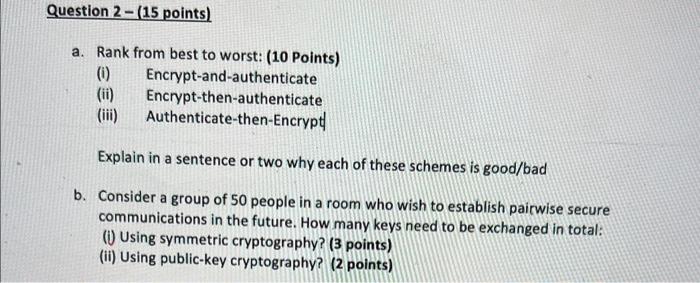
Question: please answer correctly a. Rank from best to worst: (10 Points) (i) Encrypt-and-authenticate (ii) Encrypt-then-authenticate (iii) Authenticate-then-Encrypt Explain in a sentence or two why each
 please answer correctly
please answer correctlya. Rank from best to worst: (10 Points) (i) Encrypt-and-authenticate (ii) Encrypt-then-authenticate (iii) Authenticate-then-Encrypt Explain in a sentence or two why each of these schemes is good/bad b. Consider a group of 50 people in a room who wish to establish pairwise secure communications in the future. How many keys need to be exchanged in total: (i) Using symmetric cryptography? ( 3 points) (ii) Using public-key cryptography? (2 points)
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


