Question: ******PLEASE ANSWER THE 3 MULTIPLE CHOICE QUESTIONS. JUST GIVE ME THE CORRECT OPTION FOR EACH , NO EXPLANATION NEEDED****** Question 10 In log-based the attack
******PLEASE ANSWER THE 3 MULTIPLE CHOICE QUESTIONS. JUST GIVE ME THE CORRECT OPTION FOR EACH , NO EXPLANATION NEEDED******
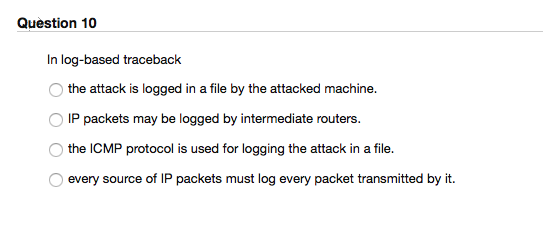
Question 10 In log-based the attack is logged in a file by the attacked machine. IP packets may be logged by intermediate routers Othe ICMP protocol is used for logging the attack in a file ? . every source of IP packets must log every packet transmitted by it
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


