Question: Please answer the following multiple-choice. Please please answer the correct answer. The choice are wrong as choose before. Please read carefully and answer correctly. QUESTION
Please answer the following multiple-choice. Please please answer the correct answer. The choice are wrong as choose before. Please read carefully and answer correctly.
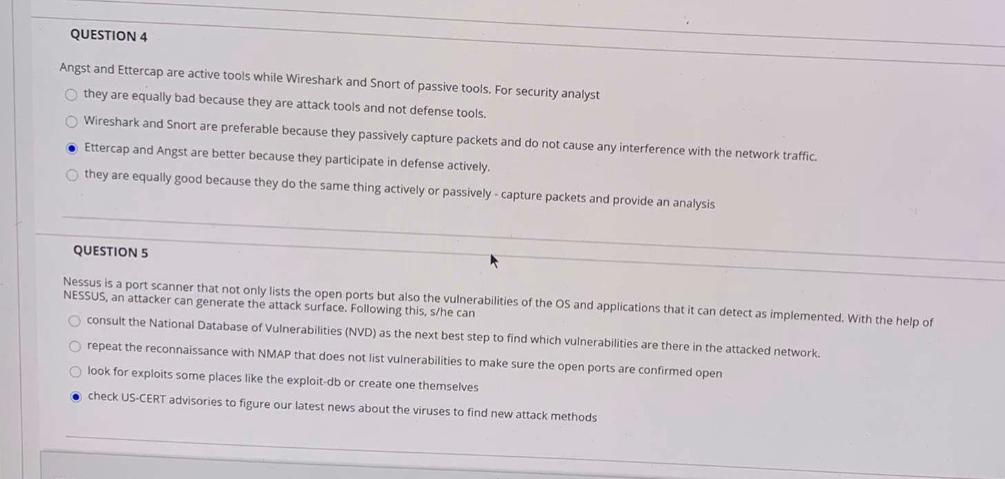
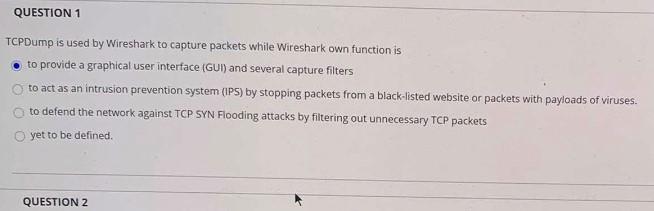
QUESTION 4 Angst and Ettercap are active tools while Wireshark and Snort of passive tools. For security analyst they are equally bad because they are attack tools and not defense tools, Wireshark and Snort are preferable because they passively capture packets and do not cause any interference with the network traffic. Ettercap and Angst are better because they participate in defense actively, they are equally good because they do the same thing actively or passively capture packets and provide an analysis QUESTION 5 Nessus is a port scanner that not only lists the open ports but also the vulnerabilities of the OS and applications that it can detect as implemented. With the help of NESSUS, an attacker can generate the attack surface. Following this, s/he can consult the National Database of Vulnerabilities (NVD) as the next best step to find which vulnerabilities are there in the attacked network. repeat the reconnaissance with NMAP that does not list vulnerabilities to make sure the open ports are confirmed open look for exploits some places like the exploit-db or create one themselves .check US-CERT advisories to figure our latest news about the viruses to find new attack methods QUESTION 1 TCPDump is used by Wireshark to capture packets while Wireshark own function is to provide a graphical user interface (GUI) and several capture filters to act as an intrusion prevention system (IPS) by stopping packets from a black-listed website or packets with payloads of viruses. to defend the network against TCP SYN Flooding attacks by filtering out unnecessary TCP packets yet to be defined QUESTION 2
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


