Question: Please do #3. As is done in DES, use the.first S-Box to encrypt the first block, the second S-Box to encrypt the second block, and
Please do #3.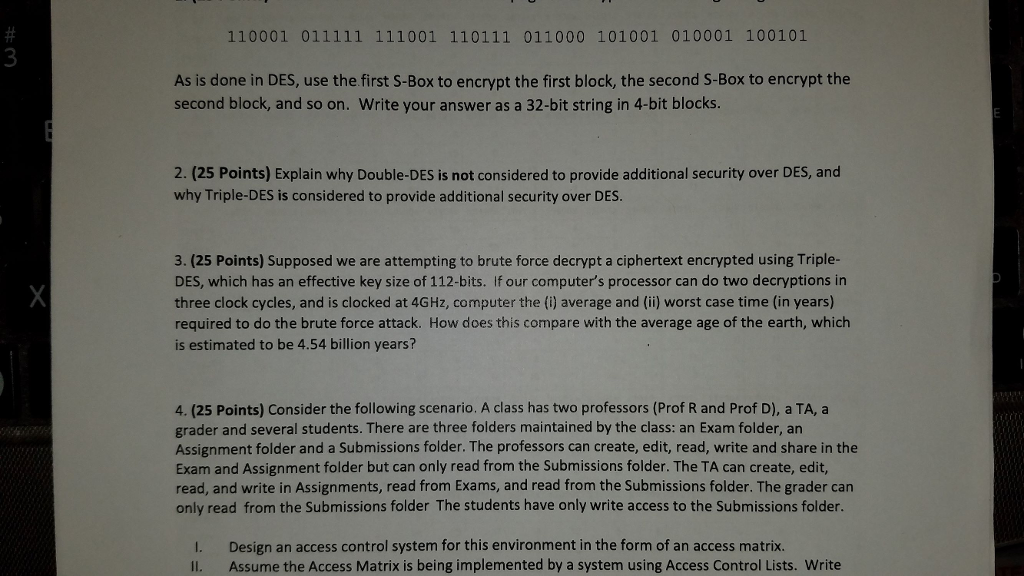
As is done in DES, use the.first S-Box to encrypt the first block, the second S-Box to encrypt the second block, and so on. Write your answer as a 32-bit string in 4-bit blocks. 2. (25 Points) Explain why Double-DES is not considered to provide additional security over DES, and why Triple-DES is considered to provide additional security over DES. 3. (25 Points) Supposed we are attempting to brute force decrypt a ciphertext encrypted using Triple- DES, which has an effective key size of 112-bits. If our computer's processor can do two decryptions in three clock cycles, and is clocked at 4GHz, computer the (i) average and (ii) worst case time (in years) required to do the brute force attack. How does this compare with the average age of the earth, which is estimated to be 4.54 billion years? 4. (25 Points) Consider the following scenario. A class has two professors (Prof R and Prof D), a TA, a grader and several students. There are three folders maintained by the class: an Exam folder, an Assignment folder and a Submissions folder. The professors can create, edit, read, write and share in the Exam and Assignment folder but can only read from the Submissions folder. The TA can create, edit, read, and write in Assignments, read from Exams, and read from the Submissions folder. The grader can only read from the Submissions folder The students have only write access to the Submissions folder. I. II. Design an access control system for this environment in the form of an access matrix Assume the Access Matrix is being implemented by a system using Access Control Lists. Write As is done in DES, use the.first S-Box to encrypt the first block, the second S-Box to encrypt the second block, and so on. Write your answer as a 32-bit string in 4-bit blocks. 2. (25 Points) Explain why Double-DES is not considered to provide additional security over DES, and why Triple-DES is considered to provide additional security over DES. 3. (25 Points) Supposed we are attempting to brute force decrypt a ciphertext encrypted using Triple- DES, which has an effective key size of 112-bits. If our computer's processor can do two decryptions in three clock cycles, and is clocked at 4GHz, computer the (i) average and (ii) worst case time (in years) required to do the brute force attack. How does this compare with the average age of the earth, which is estimated to be 4.54 billion years? 4. (25 Points) Consider the following scenario. A class has two professors (Prof R and Prof D), a TA, a grader and several students. There are three folders maintained by the class: an Exam folder, an Assignment folder and a Submissions folder. The professors can create, edit, read, write and share in the Exam and Assignment folder but can only read from the Submissions folder. The TA can create, edit, read, and write in Assignments, read from Exams, and read from the Submissions folder. The grader can only read from the Submissions folder The students have only write access to the Submissions folder. I. II. Design an access control system for this environment in the form of an access matrix Assume the Access Matrix is being implemented by a system using Access Control Lists. Write
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


