Question: Please do in MATLAB. I have the code for the encrypt function but now i need the code for the decrypt and verifykey as described
Please do in MATLAB. I have the code for the encrypt function but now i need the code for the decrypt and verifykey as described below
Here are the other code files , please finish decrypt.m and validatekey.m
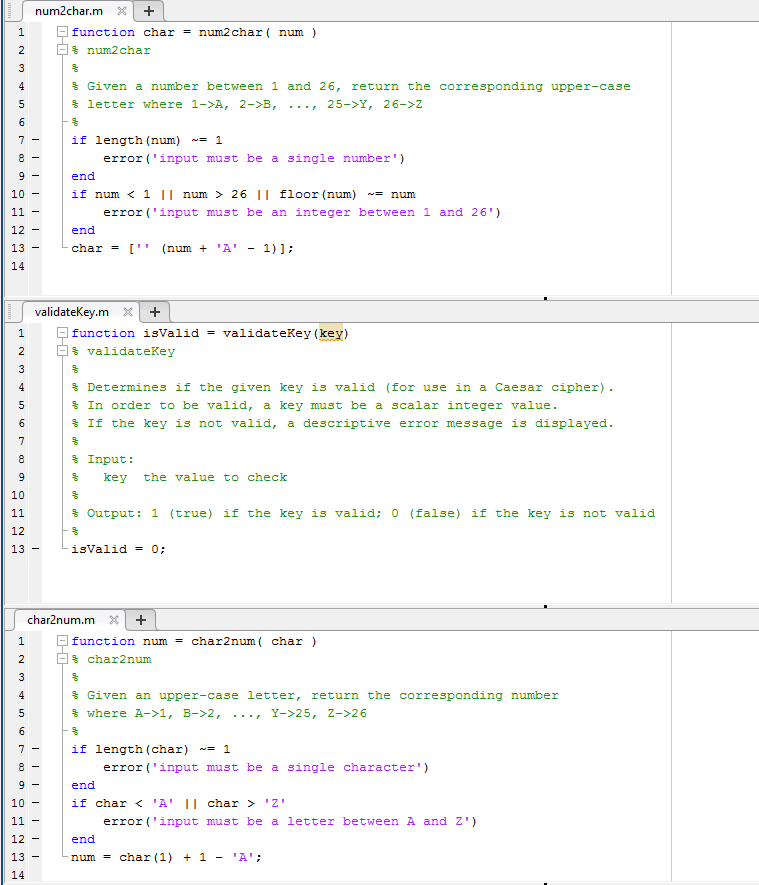
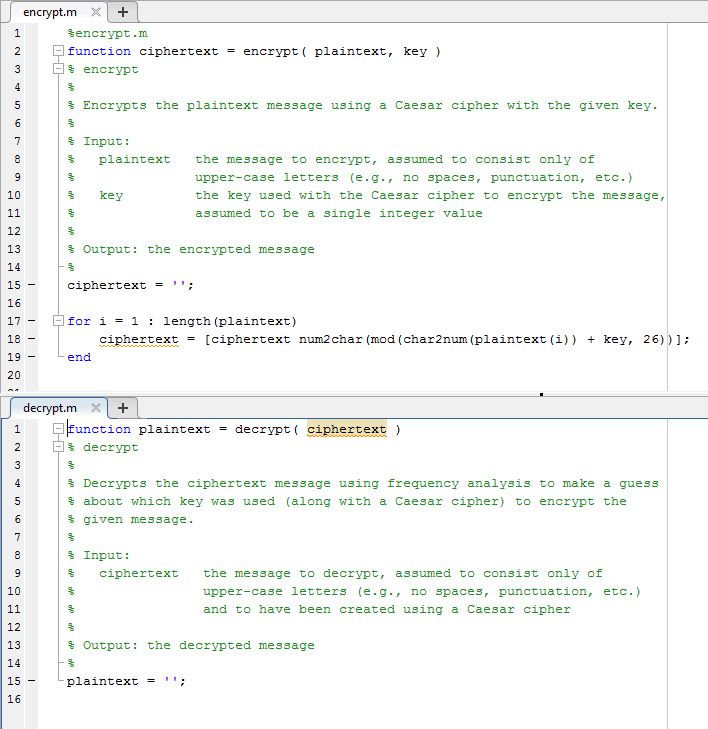
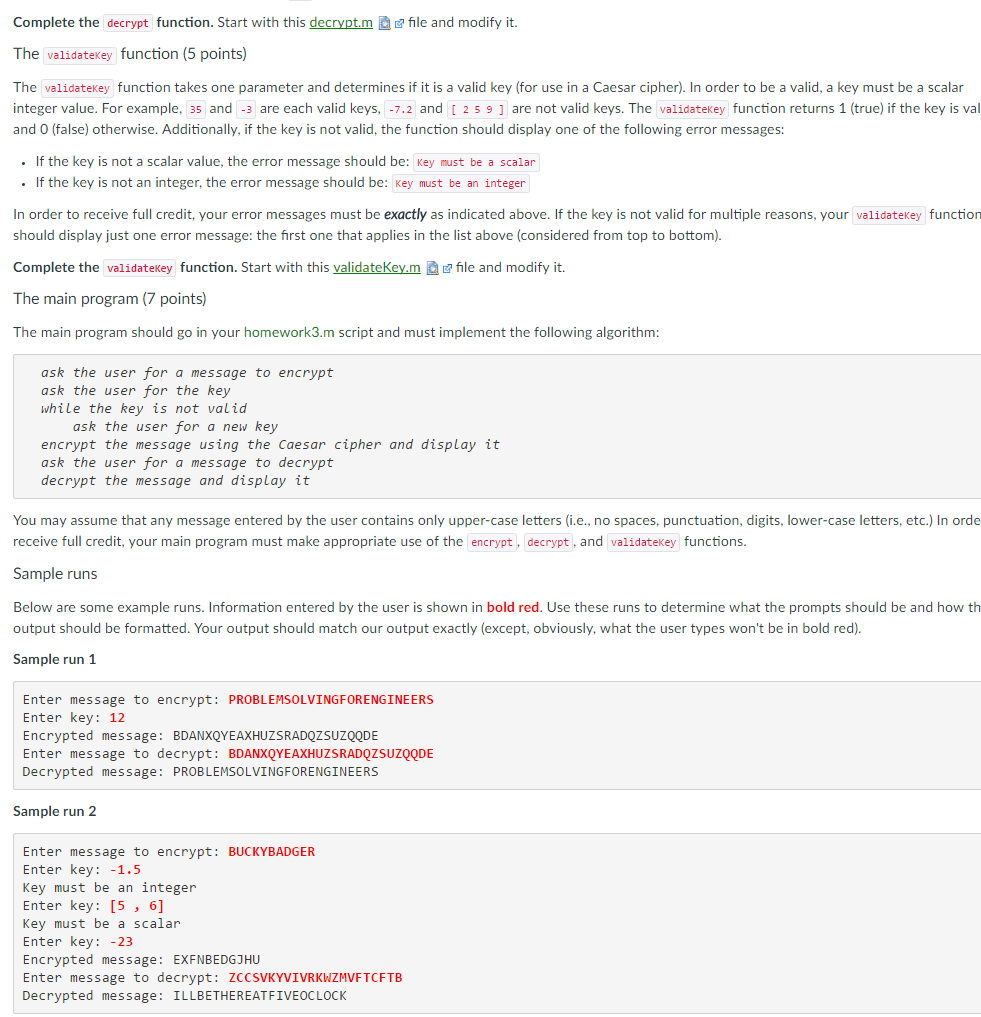
Complete the decrypt function. Start with this dec tam file and modify it The validatekey function (5 points The validatekey function takes one parameter and determines if it is a valid key (for use in a Caesar cipher). In order to be a valid, a key must be a scalar Integer value. For example 35 and -3 are each valid keys 7.2 and are not valid keys. The validatekey function returns 1 (true) if the key is va 2 59 and 0 (false) otherwise. Additionally, if the key is not valid, the function should display one of the following error messages: the key is not a scalar value, the error message should be Key must be a scalar the key is not an integer, the error message should be Key must be an integer In order to receive full credit, your e messages must be exactly as indicated above. If the rror key is not valid for multiple reasons, your validatekey function should display just one error message: the first one that applies in the st above (considered from top to bottom Complete the validatekey function. Start with this validateKe file and modify it The main program (7 points) The main program should go in your homework3.m script and must implement the following algorithm: ask the user for a message to encrypt ask the user for the key while the key is not valid ask the user for a new key encrypt the message using the Caesar cipher and display it ask the user for a message to decrypt decrypt the message and display it You may assume that any message entered by the user contains only upper-case letters (i.e., no spaces, punctuation, digits, lower-case letters, etc.) In orde decrypt, and validatekey functions credit, your main program must make appropriate use of the encrypt receive fu Sample runs nformation entered by the user is shown in bold red. Use these runs to determine what the prompts should be and how th Below are some example runs output should be formatted. Your output should match our output exactly (except obviously, what the user types won't be in bold red) Sample run 1 Enter message to encrypt PROBLEMSOLVINGFORENGINEERS Enter key 12 Encrypted message BDANXQYEAXHUZSRADQZSUZQQDE Enter message to decrypt BDANXQYEAXHUZSRADQZSUZQQDE Decrypted message PROBLEMSOLVINGFORRE NGINEERS Sample run 2 Enter message to encrypt BUCKYBADGER Enter key 1.5 Key must be an integer Enter key 5 6] Key must be a scalar Enter key 23 Encrypted message EXFNBEDGJHU Enter message to decrypt ZCCSVKYVIVRKWZMVFTCF TB Decrypted message ILLBETHEREATFIVEOCLOCK
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


