Question: please fast 2 5 Authorization controls are implemented by creating an access control matrix, which specifies what part of the IT System a user can
please fast
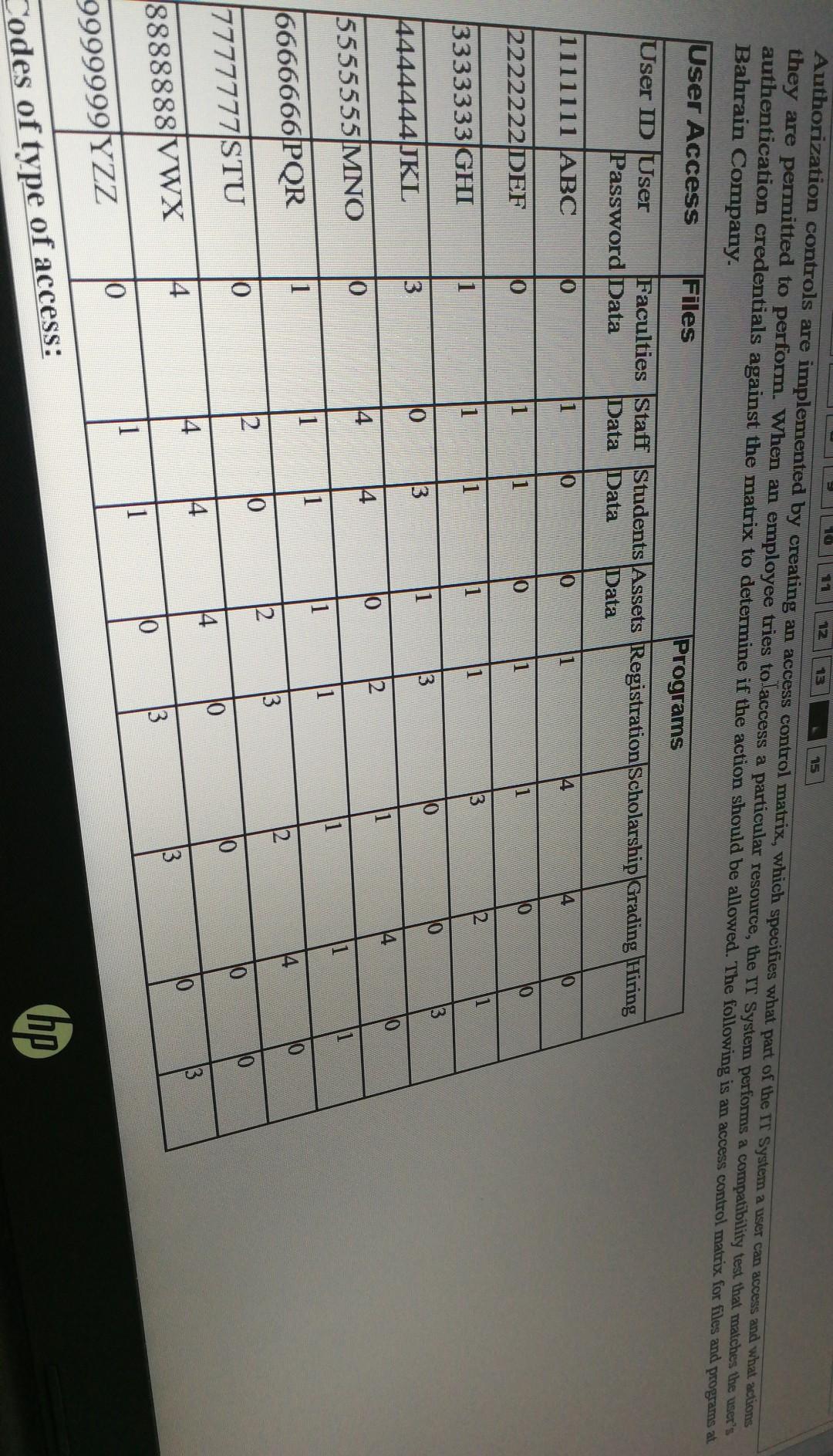
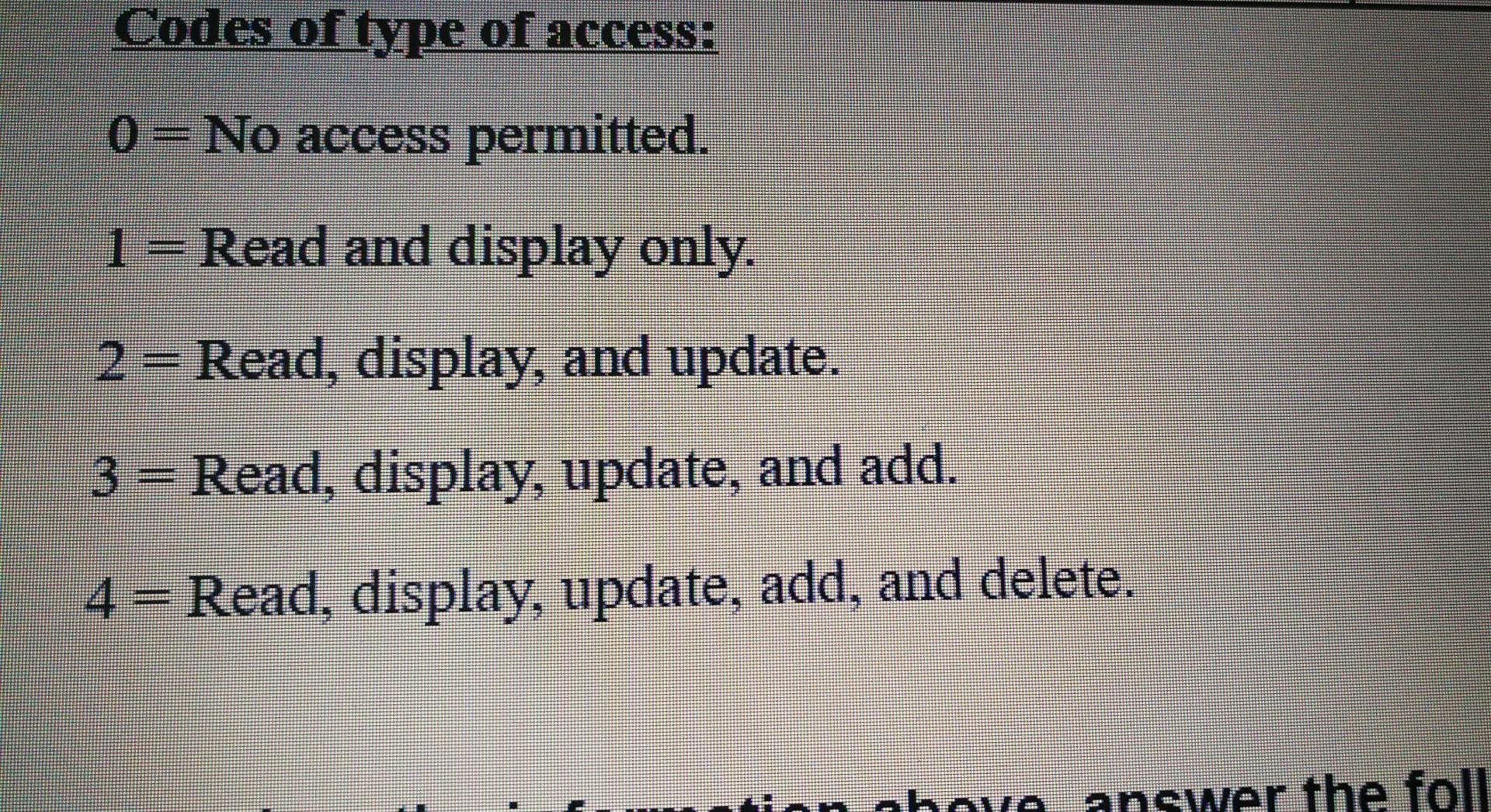
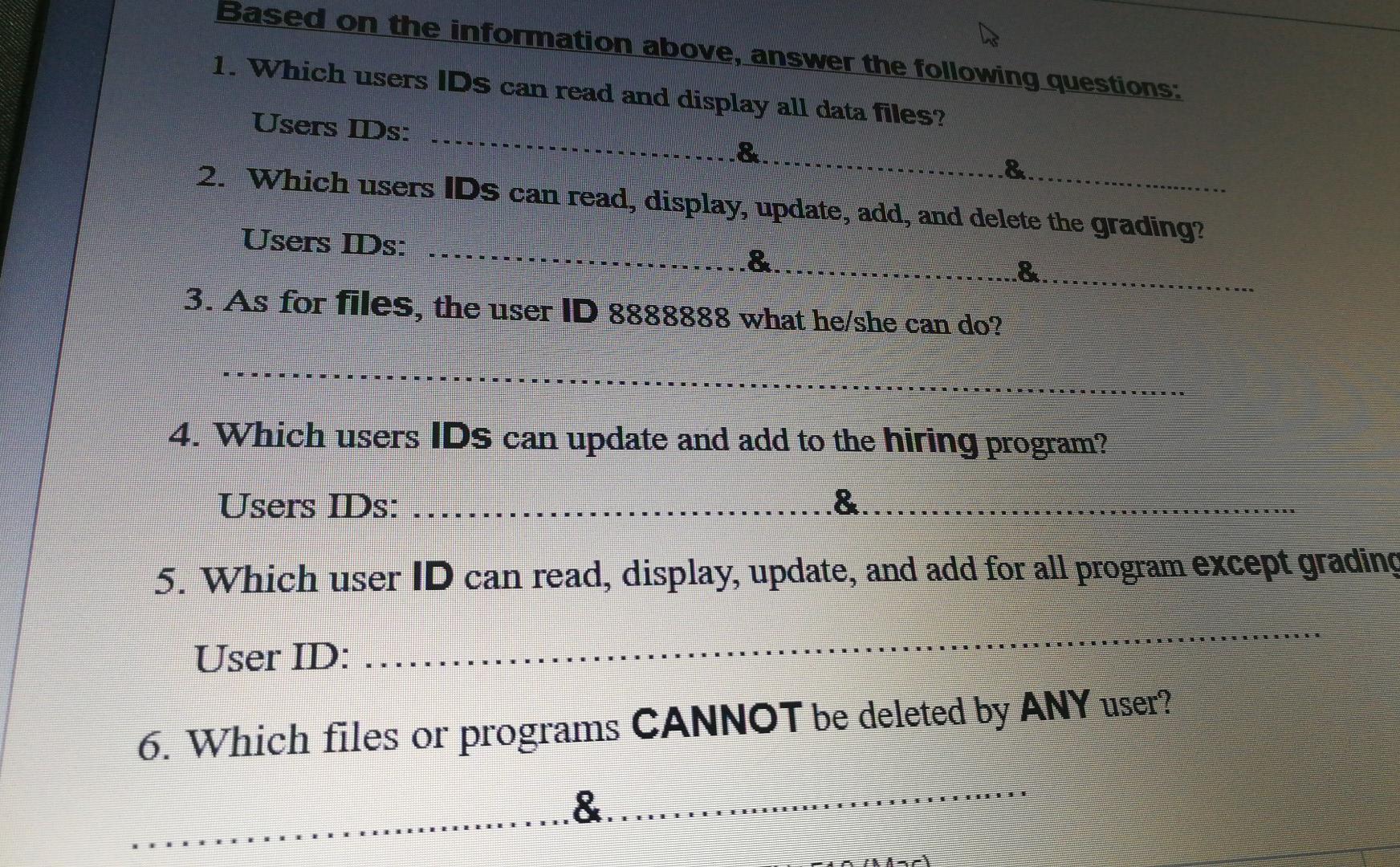
2 5 Authorization controls are implemented by creating an access control matrix, which specifies what part of the IT System a user can access and what actions they are permitted to perform. When an employee tries to access a particular resource, the IT System performs a compatibility test that matches the user's authentication credentials against the matrix to determine if the action should be allowed. The following is an access control matrix for files and programs at Bahrain Company. User Access Files Programs User ID User Faculties Staff Students Assets Registration Scholarship Grading Hiring Password Data Data Data Data 111111 ABC 0 1 0 1 4 4 10 0 1 2222222DEF 10 1 1 10 1 1 1 2 3 3333333GHI 10 3 1 3 13 3 |4444444JJKL 4 10 0 4 5555555MNO 1 1 10 6666666PQR 13 O 2 10 0 10 17777777|STU O 14 4 3 14 3 8888888VWX lo 3 1 10 9999999|YZZ hp Codes of type of access: Codes of type of access: 0 = No access permitted. 1 = Read and display only. 2= Read, display, and update. 3= Read, display, update, and add. 4 = Read, display, update, add, and delete. ion above answer the foll hoye Based on the information above, answer the following questions: 1. Which users IDs can read and display all data files? Users Ds: &. 2. Which users IDs can read, display, update, add, and delete the grading? Users Ds: &. 8. 3. As for files, the user ID 8888888 what he/she can do? 4. Which users IDs can update and add to the hiring program? Users IDs: .&. 5. Which user ID can read, display, update, and add for all program except grading User ID: . 6. Which files or programs CANNOT be deleted by ANY user &. GA
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


