Question: Please Help, And here is the starter code mentioned: 2. (10 points) A very simple way to encrypt text is to rotate each alphabetic character

Please Help, And here is the starter code mentioned: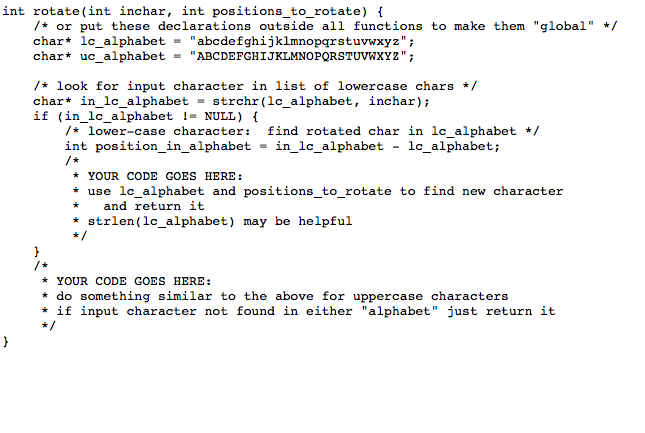
2. (10 points) A very simple way to encrypt text is to rotate each alphabetic character N positions. For example, if N is 1, " abc XYZ 1234" becomes bcd YZA 1234". (This is obviously not industrial- strength encryption but is good enough to somewhat obscure the plaintext.) Write a C program that implements this scheme. The program should take three command-line arguments: the number of positions to rotate (which for simplicity should be a positive integer), the name of the input file, and the name of the output file. It should print error messages as appropriate (not enough command-line arguments, non-numeric N, input or output file cannot be opened). For valid arguments, it should encrypt the input file and write the result to the output file. To get full credit, your program must encrypt characters as discussed in the hint below Hints o You don't need to try to read input a line at a time; you can just read and process it a character at a time using fgetc, Epute, and a function that encrypts a single character. Sample program copy You can use library unction strtol to convert a command-line argument string into an integer (You could also use atol which is simpler, but it doesn't provide a nice way to check for errors. There are probably several ways you could approach encoding each character. The one I want you to use here partly or practice working with strings, but also because it doesnt rely on file.c illustrates how to process a file one character at a time There's an example of using strtol in sample program echo-args.c characters being encoded in ASCII (which on most systems these days they are, but C doesn't require it) begins by looking up the character in a string representing the alphabet. Starter code for such a scheme, to encode int variable inchar, is available here, and to get full credit for this problem you must use this approach (rather than other ways you may have seen for doing this sort of thing)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


