Question: Please help me for question 2 , i need use it at 16:30 QUESTION 1 : Table 1 : Class and methods Class Name Purpose
Please help me for question 2 , i need use it at 16:30
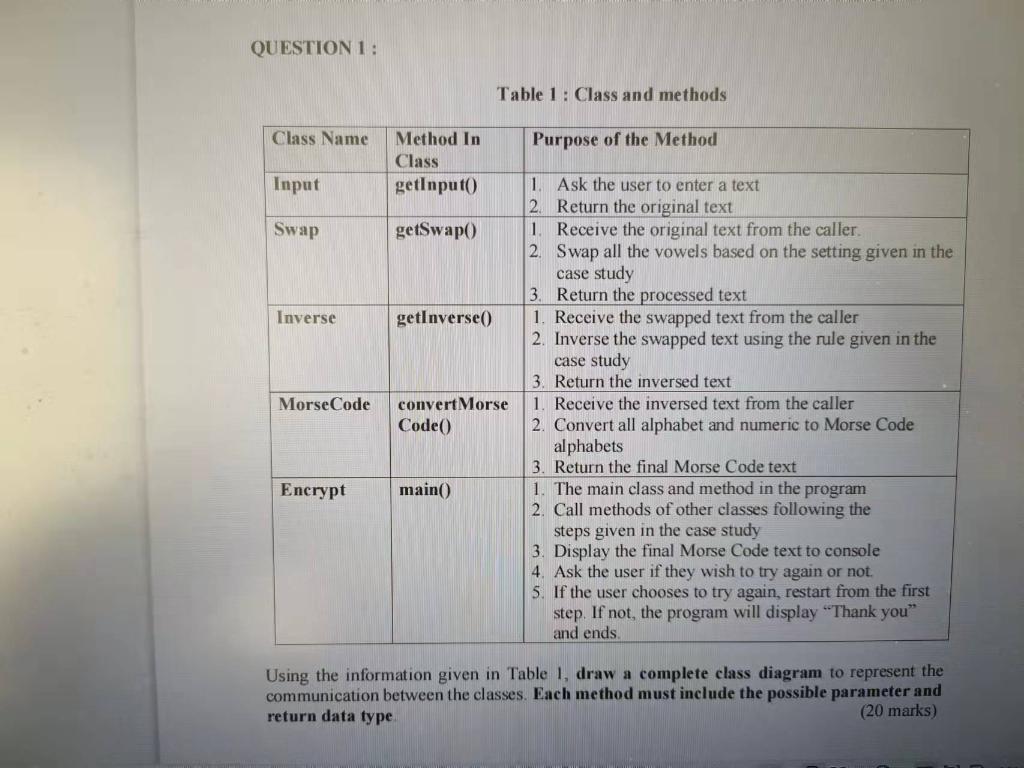
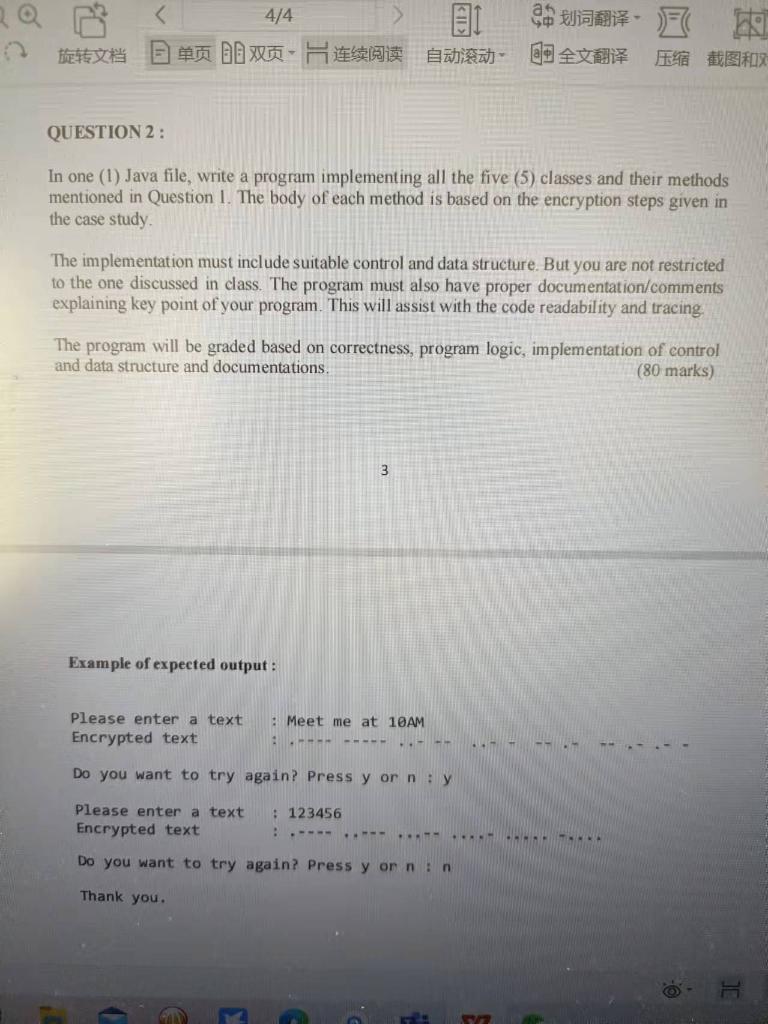
QUESTION 1 : Table 1 : Class and methods Class Name Purpose of the Method Method In Class getInput Input Swap getSwapo Inverse getInverse() MorseCode convert Morse Code 1. Ask the user to enter a text 2. Return the original text 1. Receive the original text from the caller 2. Swap all the vowels based on the setting given in the case study 3. Return the processed text 1. Receive the swapped text from the caller 2. Inverse the swapped text using the rule given in the case study 3. Return the inversed text 1. Receive the inversed text from the caller 2. Convert all alphabet and numeric to Morse Code alphabets 3. Return the final Morse Code text 1. The main class and method in the program 2. Call methods of other classes following the steps given in the case study 3. Display the final Morse Code text to console 4. Ask the user if they wish to try again or not. 5. If the user chooses to try again, restart from the first step. If not, the program will display "Thank you" and ends Encrypt main() Using the information given in Table 1, draw a complete class diagram to represent the communication between the classes. Each method must include the possible parameter and return data type (20 marks) Q 4/4 EI , QUESTION 2: In one (1) Java file, write a program implementing all the five (5) classes and their methods mentioned in Question 1. The body of each method is based on the encryption steps given in the case study The implementation must include suitable control and data structure. But you are not restricted to the one discussed in class. The program must also have proper documentation/comments explaining key point of your program. This will assist with the code readability and tracing. The program will be graded based on correctness, program logic, implementation of control and data structure and documentations, (80 marks) 3 Example of expected output: : Meet me at 10AM Please enter a text Encrypted text ..-- -- Do you want to try again? Press y or ny Please enter a text Encrypted text : 123456 ---- .. . TEK Do you want to try again? Press y or nin Thank you. 7
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


