Question: Please help me in solving the assignment today. Hash Functions: Hash function, H(x) generates a representative compact fingerprint (a hash value) of a given piece
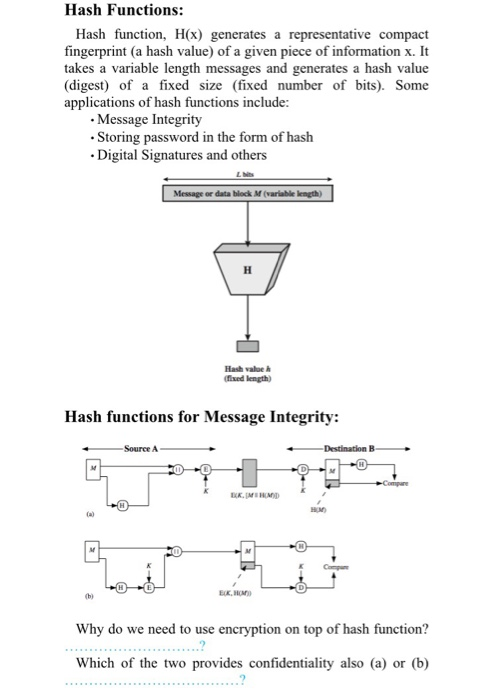

Hash Functions: Hash function, H(x) generates a representative compact fingerprint (a hash value) of a given piece of information x. It takes a variable length messages and generates a hash value (digest) of a fixed size (fixed number of bits). Some applications of hash functions include: Message Integrity Storing password in the form of hash Digital Signatures and others Message or data block M (variable length Hash valoe (fixed length Hash functions for Message Integrity: Source A b) Why do we need to use encryption on top of hash function? Which of the two provides confidentiality also (a) or (b) 2. On the popup window, you can select the hashing function to be used and see the hash value of the message. Also you can modify the original message and see the difference between the hash of the original message and the modified message. You will see that the hash value greatly differs even for a small change in the original message. Can you find another message with the same haslh value? What are three properties that make hash function secure
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


