Question: please help with this question AGE MINDTAP Use it stions re06pi14h.M2 You're helping to on board a new employee who will be spending some time
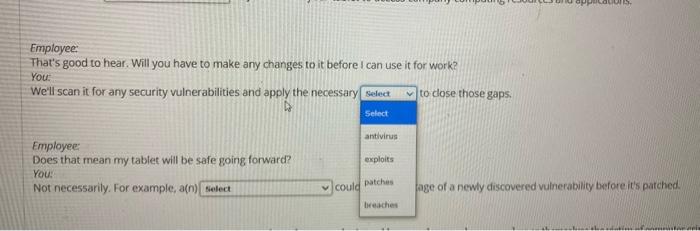
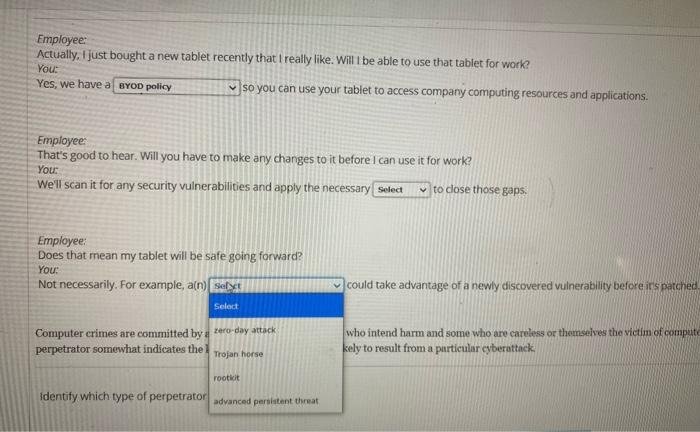
please help with this question 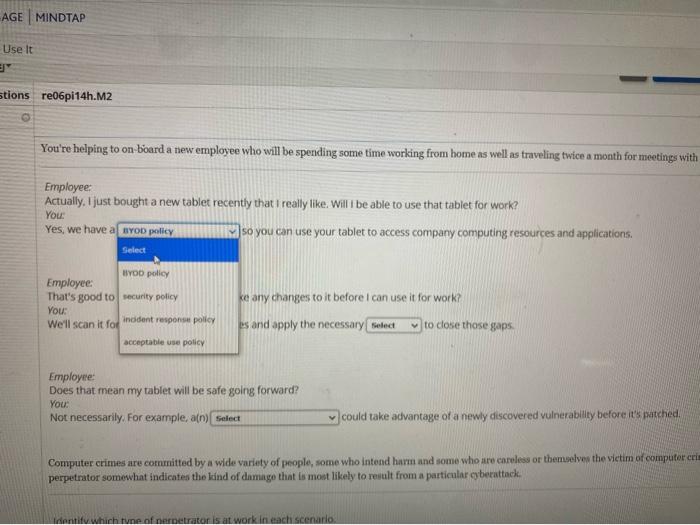

Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


