Question: Please if you are not sure from your answer 100% do not answer this s question. Thanks in advance A cybersecurity analyst is working on
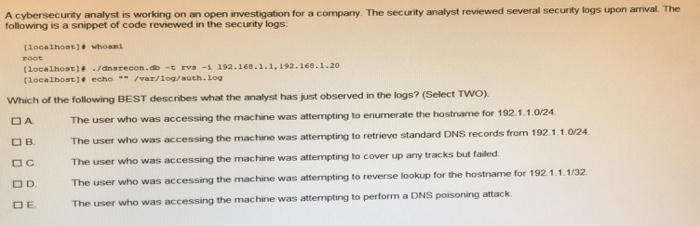
A cybersecurity analyst is working on an open investigation for a company. The security analyst reviewed several security logs upon arriva. The following is a snippet of code reviewed in the security logs: tlocalhost] /dnsrecon.db -t rvs -i 192.168.1.1, 192.168.1.20 [localhost] echovar/log/auth.log Which of the following BEST describes what the analyst has just observed in the logs? (Select TWo) the hostname for 192.1.1.0/24 DA B. Dc O D E. The user who was accessing the machine was attempting to enumerate t The user who was accessing The user who was accessing the machine was attempting to cover up any tracks The user who was accessing the machine was attempting to reverse lookup for the hostname The user who was accessing the machine was attempting to retrieve standard DNS records but failed the machine was attempting to perform a DNS poisoning attack
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


