Question: Please if you are not sure from your answer 100% do not answer the question. Thanks in advance. A security incident responder discovers an attacker
Please if you are not sure from your answer 100% do not answer the question. Thanks in advance.
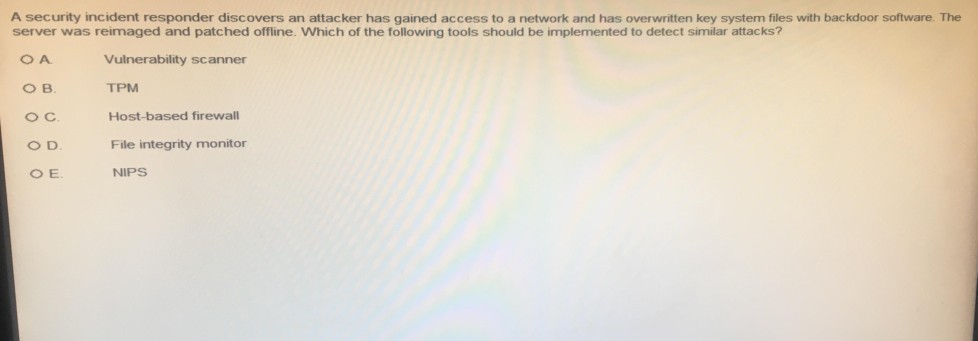
A security incident responder discovers an attacker has gained access to a network and has overwritten key system files with backdoor software. The server was reimaged and patched offline. Which of the following tools should be implemented to detect similar attacks? Vulnerability scanner TPM Host-based firewall File integrity monitor NIPS O D
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


