Question: Please match the following threats with its description. Programming routine built into a system by its designer or programmer, enabling the ability to bypass systems
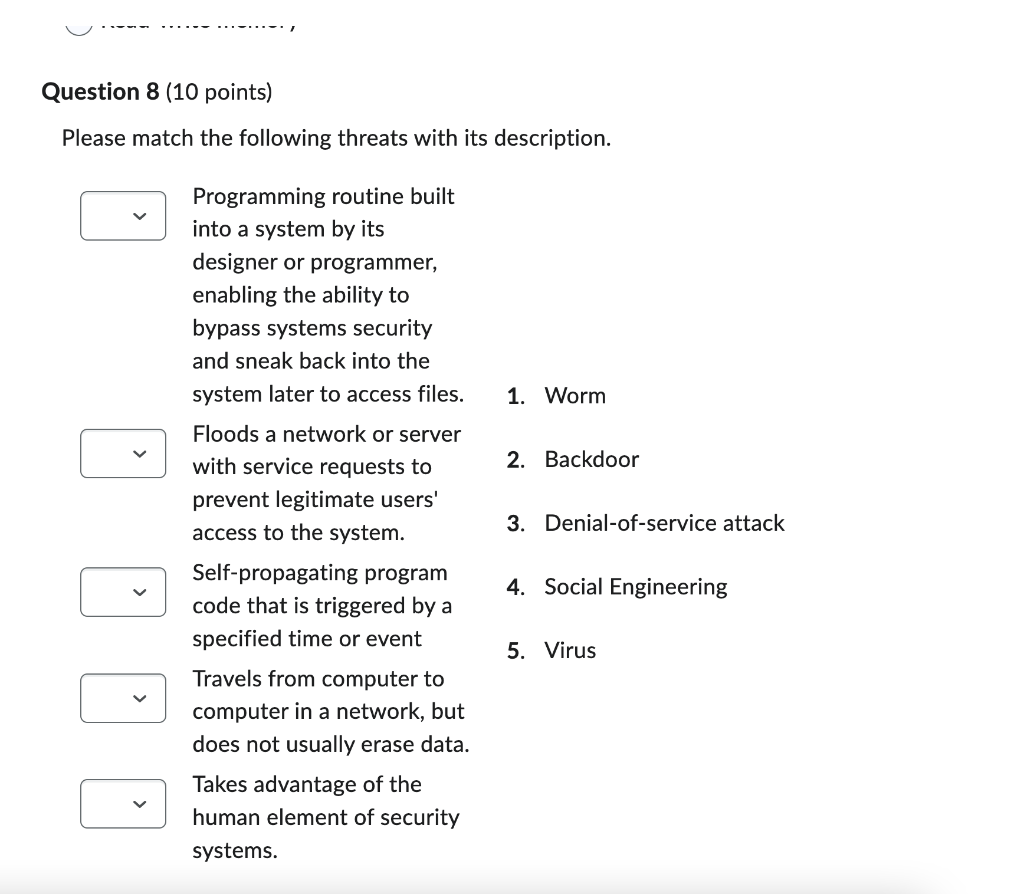
Please match the following threats with its description. Programming routine built into a system by its designer or programmer, enabling the ability to bypass systems security and sneak back into the system later to access files. 1. Worm Floods a network or server with service requests to 2. Backdoo prevent legitimate users' access to the system. 3. Denial-o Self-propagating program 4. Social E code that is triggered by a specified time or event 5. Virus Travels from computer to computer in a network, but does not usually erase data. Takes advantage of the human element of security systems
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


