Question: please read the question A server program takes an input from a remote user, saves the input in a buffer allocated on the stack (Region
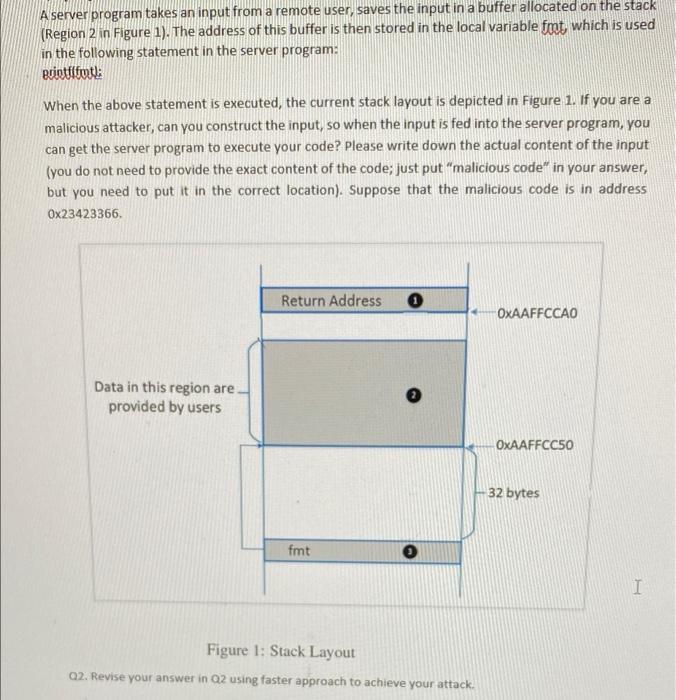
A server program takes an input from a remote user, saves the input in a buffer allocated on the stack (Region 2 in Figure 1). The address of this buffer is then stored in the local variable fmt which is used in the following statement in the server program: printfiuti: When the above statement is executed, the current stack layout is depicted in Figure 1. If you are a malicious attacker, can you construct the input, so when the input is fed into the server program, you can get the server program to execute your code? Please write down the actual content of the input (you do not need to provide the exact content of the code; just put "malicious code" in your answer, but you need to put it in the correct location). Suppose that the malicious code is in address Ox23423366 Return Address 0 OxAAFFCCAO Data in this region are provided by users OxAAFFCC50 32 bytes fmt I Figure 1: Stack Layout 02. Revise your answer in Q2 using faster approach to achieve your attack
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


