Question: Please reply as soon as possible No Space Section 1: (20 points, 2 points each) For each of the following scenarios, state which primary security
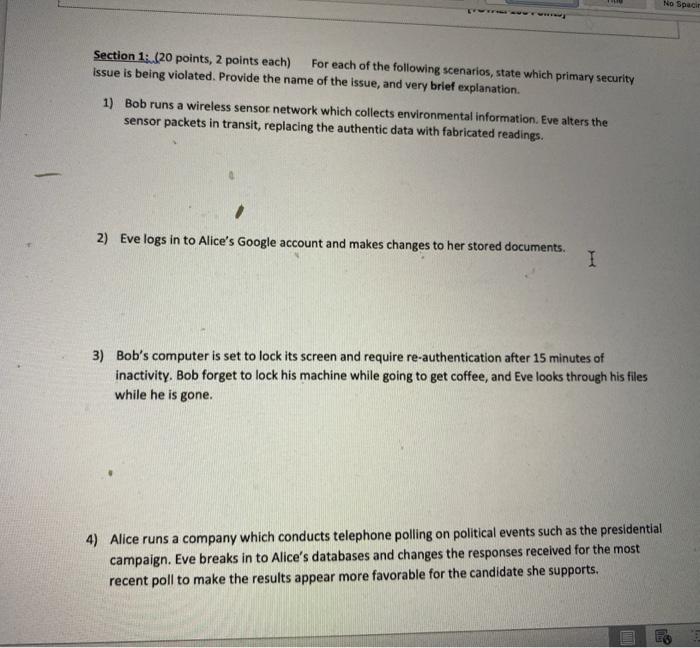
No Space Section 1: (20 points, 2 points each) For each of the following scenarios, state which primary security issue is being violated. Provide the name of the issue, and very brief explanation. 1) Bob runs a wireless sensor network which collects environmental information. Eve alters the sensor packets in transit, replacing the authentic data with fabricated readings. 2) Eve logs in to Alice's Google account and makes changes to her stored documents. I 3) Bob's computer is set to lock its screen and require re-authentication after 15 minutes of inactivity. Bob forget to lock his machine while going to get coffee, and Eve looks through his files while he is gone. 4) Alice runs a company which conducts telephone polling on political events such as the presidential campaign. Eve breaks in to Alice's databases and changes the responses received for the most recent poll to make the results appear more favorable for the candidate she supports
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


