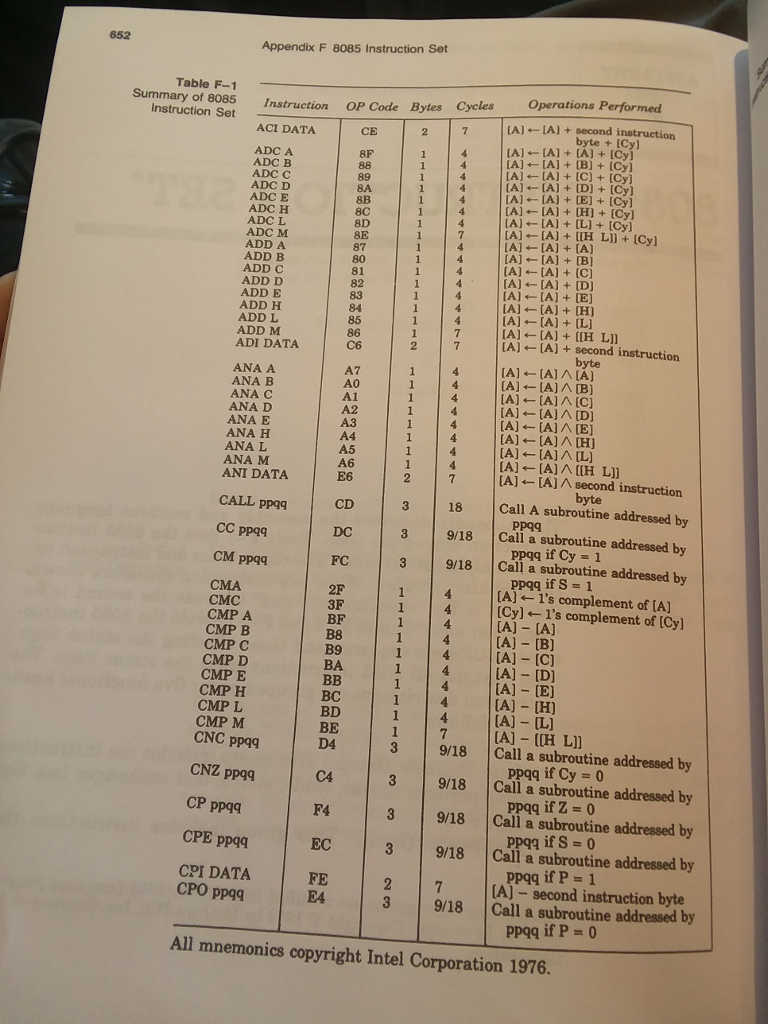
Question: please solve these question. Appendix F 8085 Instruction Set Table F-1 Summary of 8085 Instruction Set Instruction OP Code Bytes Cycles Operations Performed ACI DATA
![ACI DATA ADC A [A] [A] + second instruction byte + [Cy](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3ae5c0a7dd_91566f3ae5b51f4d.jpg)
![ADC E [A] [A] + [L1+ [Cy] ADD A ADD D ADD](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3ae5d23b33_91666f3ae5c58ecd.jpg)
![E ADD H ADD L A] [A]+ IL) [A] [A] + [[H](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3ae5e339d1_91766f3ae5d6d624.jpg)
![Lil A) A) + second instruction ADI DATA C6 [A] [A]A [A]](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3ae5f538bc_91866f3ae5e94b88.jpg)
![[A] A]A B] [A] [AJA [C] ANA A ANA B ANA C](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3ae607142d_91966f3ae5fa7c0d.jpg)
![ANA D ANA E ANA H A2 A3 A4 A5 [A] [AJA](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3ae612f0dd_92066f3ae60c1635.jpg)
please solve these question.
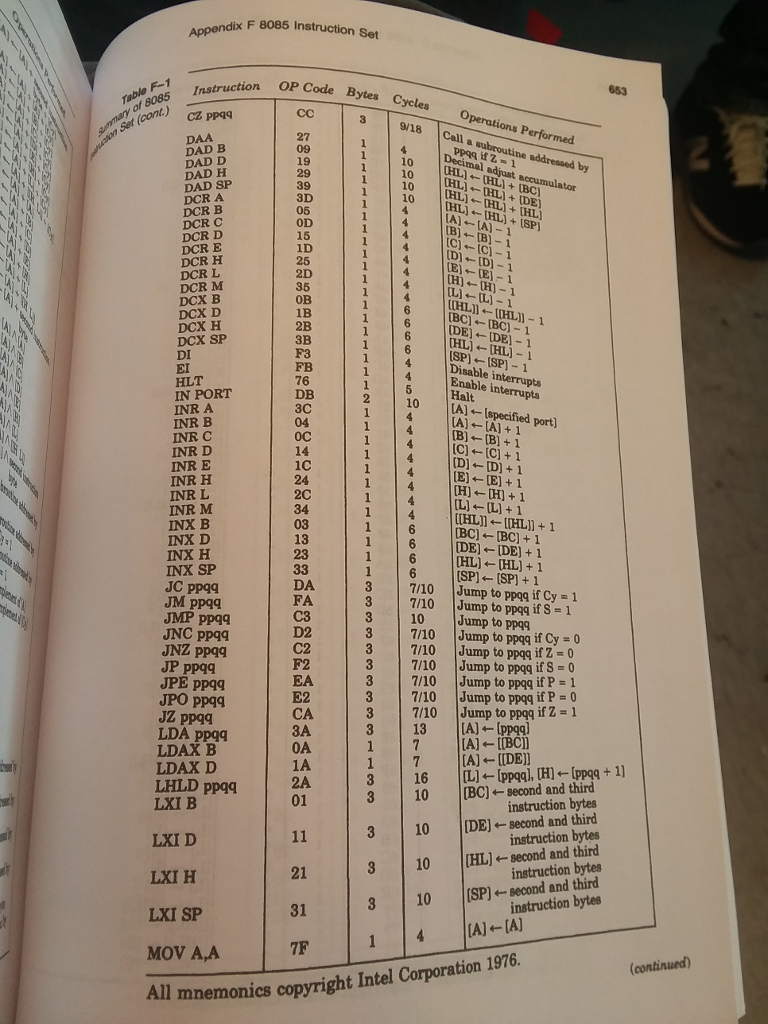
Appendix F 8085 Instruction Set Table F-1 Summary of 8085 Instruction Set Instruction OP Code Bytes Cycles Operations Performed ACI DATA ADC A [A] [A] + second instruction byte + [Cy ADC E [A] [A] + [L1+ [Cy] ADD A ADD D ADD E ADD H ADD L A] [A]+ IL) [A] [A] + [[H Lil A) A) + second instruction ADI DATA C6 [A] [A]A [A] [A] A]A B] [A] [AJA [C] ANA A ANA B ANA C ANA D ANA E ANA H A2 A3 A4 A5 [A] [AJA [E] [A] [AJA [H] ANA M ANI DATA [A] [AJA [[H L]] [A] [AIA second instruction CALL ppgq CD 3 18 Call A subroutine addressed by 3 9118 Call a subroutine adressed by 3 9/18 Call a subroutine addressed by CM ppqq FC ppqq if S-1 [A] 1's complement of [A] [Cy] 1's complement of [Cy] A] [A] 2F CMC CMP A | | 4 | B8 A] [E] CMP CMP M CNC ppqq CNZ ppqq CP ppqq 3 9/18 Call a subroutine addressed by 3 9/18Call a subroutine addressed by 3 9/18 Call a subroutine addressed by 3 9/18 Call a subroutine addressed by PE 27[A]- second instruction byte D4 C4 F4 ppqq if Cys 0 ppqq if Z = 0 ppqq ifs=0 ppqq ifP=1 ppqq if P = 0 CPI DATA CPO ppqq 54 3 9/18 Call a subroutine addressed by All mnemonics copyright Intel Corporation 1976 Appendix F 8085 Instruction Set Table F-1 Summary of 8085 Instruction Set Instruction OP Code Bytes Cycles Operations Performed ACI DATA ADC A [A] [A] + second instruction byte + [Cy ADC E [A] [A] + [L1+ [Cy] ADD A ADD D ADD E ADD H ADD L A] [A]+ IL) [A] [A] + [[H Lil A) A) + second instruction ADI DATA C6 [A] [A]A [A] [A] A]A B] [A] [AJA [C] ANA A ANA B ANA C ANA D ANA E ANA H A2 A3 A4 A5 [A] [AJA [E] [A] [AJA [H] ANA M ANI DATA [A] [AJA [[H L]] [A] [AIA second instruction CALL ppgq CD 3 18 Call A subroutine addressed by 3 9118 Call a subroutine adressed by 3 9/18 Call a subroutine addressed by CM ppqq FC ppqq if S-1 [A] 1's complement of [A] [Cy] 1's complement of [Cy] A] [A] 2F CMC CMP A | | 4 | B8 A] [E] CMP CMP M CNC ppqq CNZ ppqq CP ppqq 3 9/18 Call a subroutine addressed by 3 9/18Call a subroutine addressed by 3 9/18 Call a subroutine addressed by 3 9/18 Call a subroutine addressed by PE 27[A]- second instruction byte D4 C4 F4 ppqq if Cys 0 ppqq if Z = 0 ppqq ifs=0 ppqq ifP=1 ppqq if P = 0 CPI DATA CPO ppqq 54 3 9/18 Call a subroutine addressed by All mnemonics copyright Intel Corporation 1976
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


