Question: Please Urgent help neede for exam question. please help. Incident response teams (IRTs) have various roles. The role is the team lead, whereas the role
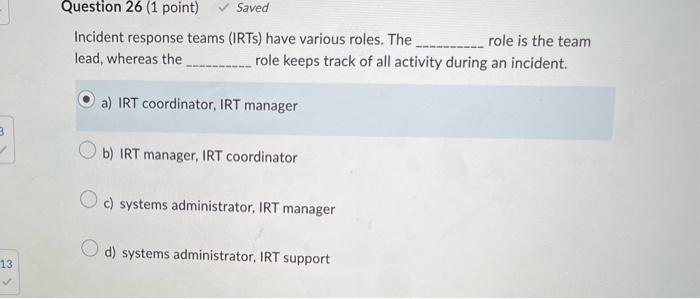
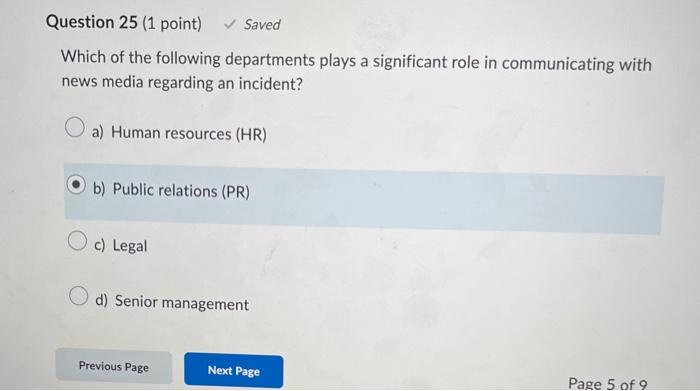
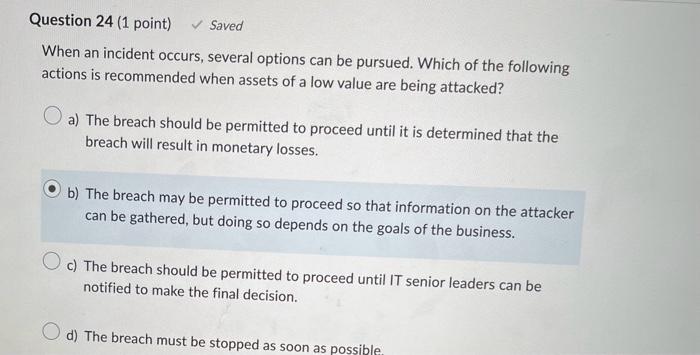
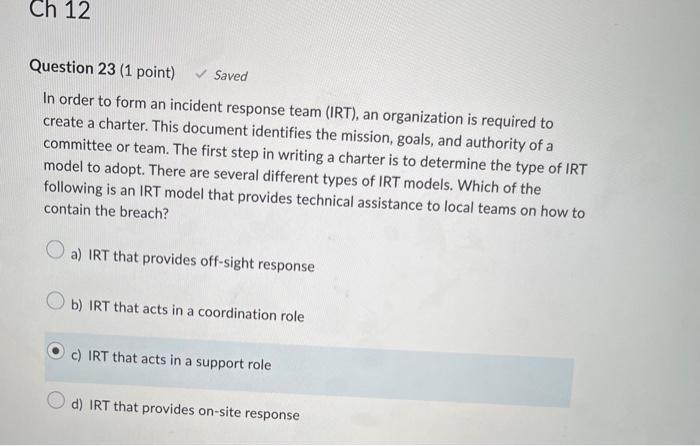
Incident response teams (IRTs) have various roles. The role is the team lead, whereas the role keeps track of all activity during an incident. a) IRT coordinator, IRT manager b) IRT manager, IRT coordinator c) systems administrator, IRT manager d) systems administrator, IRT support Which of the following departments plays a significant role in communicating with news media regarding an incident? a) Human resources (HR) b) Public relations (PR) c) Legal d) Senior management When an incident occurs, several options can be pursued. Which of the following actions is recommended when assets of a low value are being attacked? a) The breach should be permitted to proceed until it is determined that the breach will result in monetary losses. b) The breach may be permitted to proceed so that information on the attacker can be gathered, but doing so depends on the goals of the business. c) The breach should be permitted to proceed until IT senior leaders can be notified to make the final decision. d) The breach must be stopped as soon as possible In order to form an incident response team (IRT), an organization is required to create a charter. This document identifies the mission, goals, and authority of a committee or team. The first step in writing a charter is to determine the type of IRT model to adopt. There are several different types of IRT models. Which of the following is an IRT model that provides technical assistance to local teams on how to contain the breach? a) IRT that provides off-sight response b) IRT that acts in a coordination role c) IRT that acts in a support role d) IRT that provides on-site response Which of the following scenarios illustrates an ideal time to implement security policies to gain the maximum level of organizational commitment? a) The policies should be implemented following a new product launch. b) The policies should be implemented to coincide with audit findings in order to minimize security risks. c) The policies should be implemented at the same time new customer service policies are introduced. d) The policies should be implemented at the same time of a new product launch
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


