Question: Problem 4 (10 pts) Message Authentication Code (MAC) a (3 pts) When we say that an MAC needs to resist Existential Forgery under Chosen Plaintext
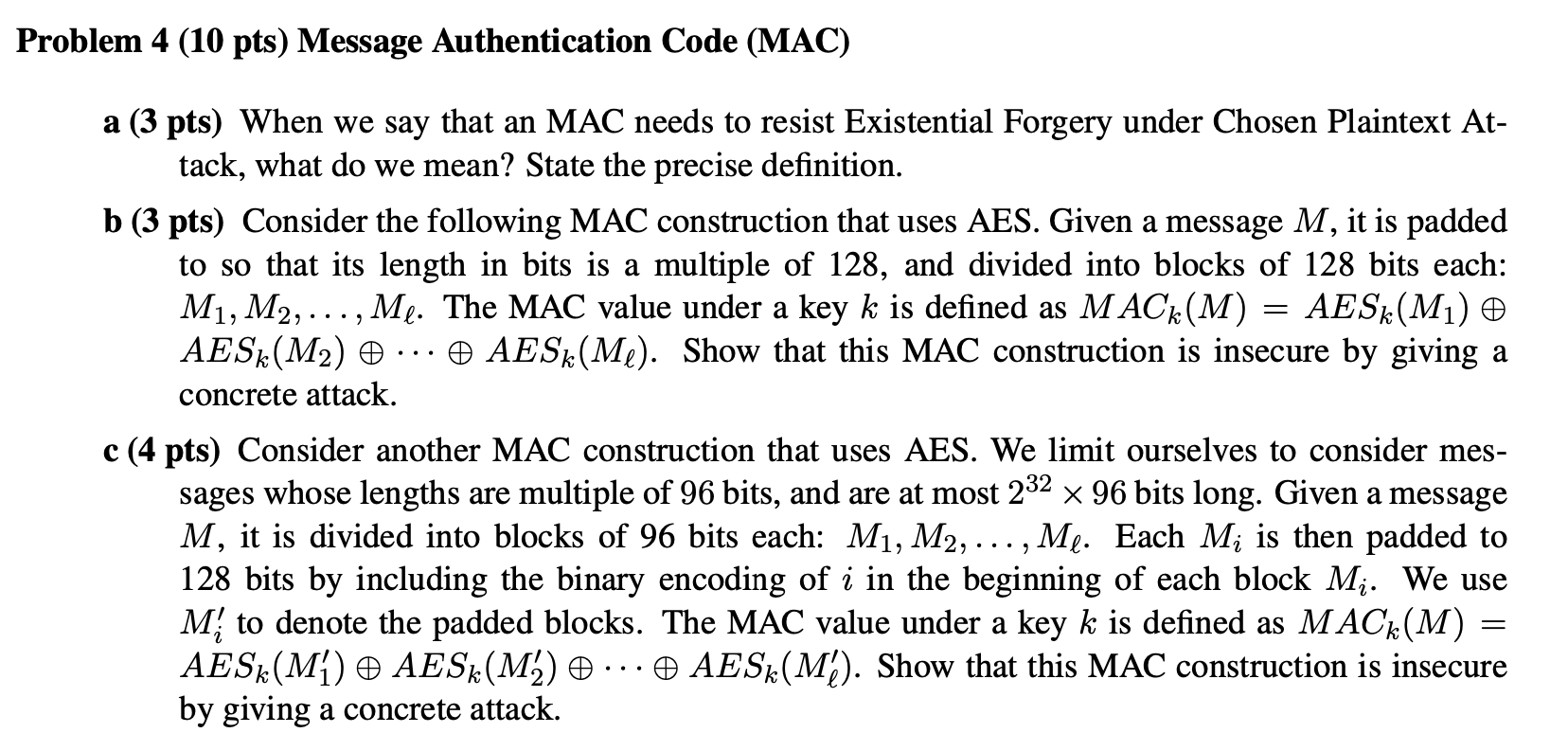
Problem 4 (10 pts) Message Authentication Code (MAC) a (3 pts) When we say that an MAC needs to resist Existential Forgery under Chosen Plaintext At- tack, what do we mean? State the precise definition. b (3 pts) Consider the following MAC construction that uses AES. Given a message M, it is padded to so that its length in bits is a multiple of 128, and divided into blocks of 128 bits each: M1, M2, ..., Me. The MAC value under a key k is defined as M ACk(M) = AESk(Mi) 0 AESk(M2) 0 AESk(Me). Show that this MAC construction is insecure by giving a concrete attack. c(4 pts) Consider another MAC construction that uses AES. We limit ourselves to consider mes- sages whose lengths are multiple of 96 bits, and are at most 232 x 96 bits long. Given a message M, it is divided into blocks of 96 bits each: M1, M2, ..., Me. Each Mi is then padded to 128 bits by including the binary encoding of i in the beginning of each block M;. We use M to denote the padded blocks. The MAC value under a key k is defined as MACk(M) AES (M) AES (M) ... AES (M). Show that this MAC construction is insecure by giving a concrete attack. =
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


