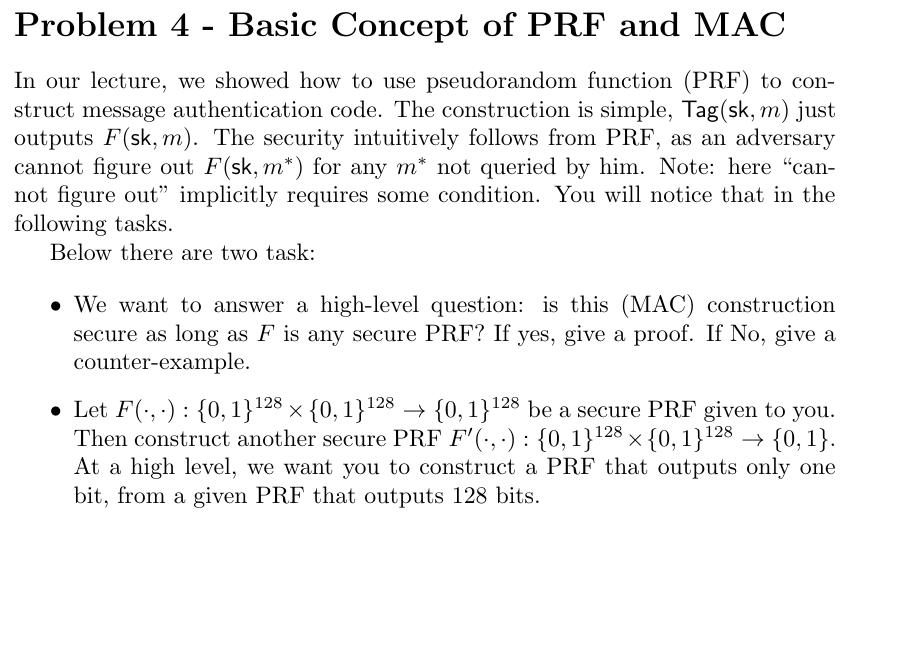
Question: Problem 4 - Basic Concept of PRF and MAC In our lecture, we showed how to use pseudorandom function ( PRF ) to con -
Problem Basic Concept of PRF and MAC
In our lecture, we showed how to use pseudorandom function PRF to con
struct message authentication code. The construction is simple, Tag just
outputs sk The security intuitively follows from PRF as an adversary
cannot figure out for any not queried by him. Note: here "can
not figure out" implicitly requires some condition. You will notice that in the
following tasks.
Below there are two task:
We want to answer a highlevel question: is this MAC construction
secure as long as is any secure PRF If yes, give a proof. If No give a
counterexample.
Let : be a secure PRF given to you.
Then construct another secure :
At a high level, we want you to construct a PRF that outputs only one
bit, from a given PRF that outputs bits.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


