Question: Problem --> We will write a message in encrypted form message.txt --> 01011011010100001101011001110101010111010101101101000110110101000011010010011101 decode_message.py --> local_file=open('message.txt' , 'r', encoding = 'utf-8') #1st checkpoint open and
Problem --> We will write a message in encrypted form message.txt --> 01011011010100001101011001110101010111010101101101000110110101000011010010011101
decode_message.py --> local_file=open('message.txt' , 'r', encoding = 'utf-8') #1st checkpoint open and read the file a=local_file.read() n=10 i=0 msg=list() #create a blank list for lsb first rmsg=list() #create a blank list for msb first asciimsg=list() #create a blank list for decoded ASCII character def reverse_string(x): # 2nd checkpoint: reverses the binary code (lsb first -> msb first) return x[::-1] while (n
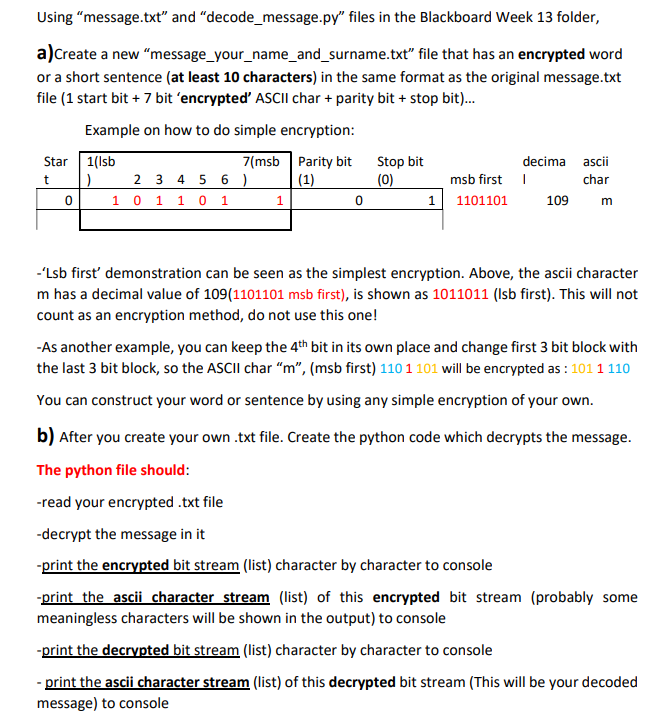
Using message.txt" and "decode_message.py" files in the Blackboard Week 13 folder, a)Create a new message_your_name_and_surname.txt file that has an encrypted word or a short sentence (at least 10 characters) in the same format as the original message.txt file (1 start bit + 7 bit 'encrypted' ASCII char + parity bit + stop bit... Example on how to do simple encryption: Star 1(Isb 7(msb Parity bit Stop bit decima ascii 2 3 4 5 6 ) (1) (0) msb first char 1 1 0 1 0 1 1101101 109 t 0 1 0 1 m -'Lsb first demonstration can be seen as the simplest encryption. Above, the ascii character m has a decimal value of 109(1101101 msb first), is shown as 1011011 (Isb first). This will not count as an encryption method, do not use this one! -As another example, you can keep the 4th bit in its own place and change first 3 bit block with the last 3 bit block, so the ASCII char m, (msb first) 110 1 101 will be encrypted as : 1011110 You can construct your word or sentence by using any simple encryption of your own. b) After you create your own .txt file. Create the python code which decrypts the message. The python file should: -read your encrypted .txt file -decrypt the message in it -print the encrypted bit stream (list) character by character to console -print the ascii character stream (list) of this encrypted bit stream (probably some meaningless characters will be shown in the output) to console -print the decrypted bit stream (list) character by character to console - print the ascii character stream (list) of this decrypted bit stream (This will be your decoded message) to console Using message.txt" and "decode_message.py" files in the Blackboard Week 13 folder, a)Create a new message_your_name_and_surname.txt file that has an encrypted word or a short sentence (at least 10 characters) in the same format as the original message.txt file (1 start bit + 7 bit 'encrypted' ASCII char + parity bit + stop bit... Example on how to do simple encryption: Star 1(Isb 7(msb Parity bit Stop bit decima ascii 2 3 4 5 6 ) (1) (0) msb first char 1 1 0 1 0 1 1101101 109 t 0 1 0 1 m -'Lsb first demonstration can be seen as the simplest encryption. Above, the ascii character m has a decimal value of 109(1101101 msb first), is shown as 1011011 (Isb first). This will not count as an encryption method, do not use this one! -As another example, you can keep the 4th bit in its own place and change first 3 bit block with the last 3 bit block, so the ASCII char m, (msb first) 110 1 101 will be encrypted as : 1011110 You can construct your word or sentence by using any simple encryption of your own. b) After you create your own .txt file. Create the python code which decrypts the message. The python file should: -read your encrypted .txt file -decrypt the message in it -print the encrypted bit stream (list) character by character to console -print the ascii character stream (list) of this encrypted bit stream (probably some meaningless characters will be shown in the output) to console -print the decrypted bit stream (list) character by character to console - print the ascii character stream (list) of this decrypted bit stream (This will be your decoded message) to console
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


