Question: Problems: 1 . A desktop publishing system 1 s utilized for creating documents across different organizations. 1 . Identify a publication type where the utmost
Problems:
A desktop publishing system s utilized for creating documents across different organizations.
Identify a publication type where the utmost priority is the confidentiality of data maintained within the system.
Mention a publication type where ensuring the integrity of data is the primary concern.
m Highlight a scenario in which the most crucial aspect is the system's availability for document production.
You are a senior IT executive at your department responsible for the DES encryption key management. From the random key generator, you are given the secret key EEEEFlFlFlFlhex to encrypt a critical message.
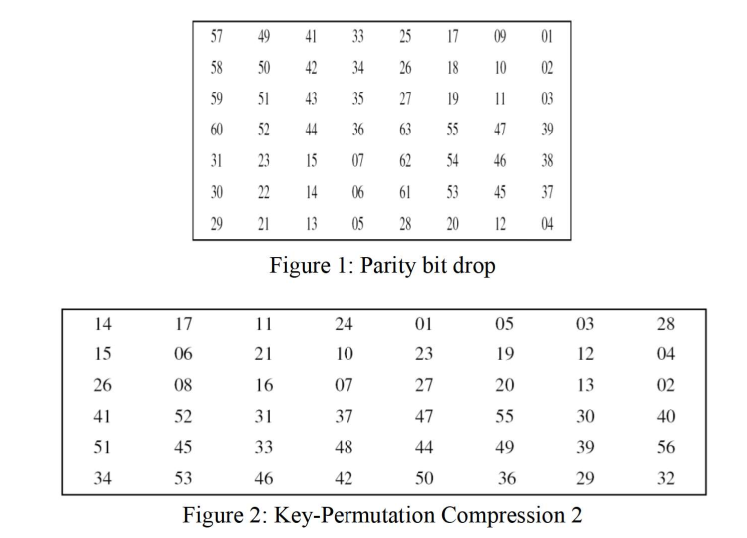
What is is the output of the key after it is applied with the parity bit drop process shown in Figure At this point, determine if it is a strong, weak, or semiweak key. Provide a detailed explanation for your assessment.
Using the keypermutation compression from Figure reevaluate whether this is a strong, weak or semiweak key. Justify your answer thoroughly and explain the implications of using this key for encrypting the critical message. Figure : Parity bit drop
Figure : KeyPermutation Compression
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


