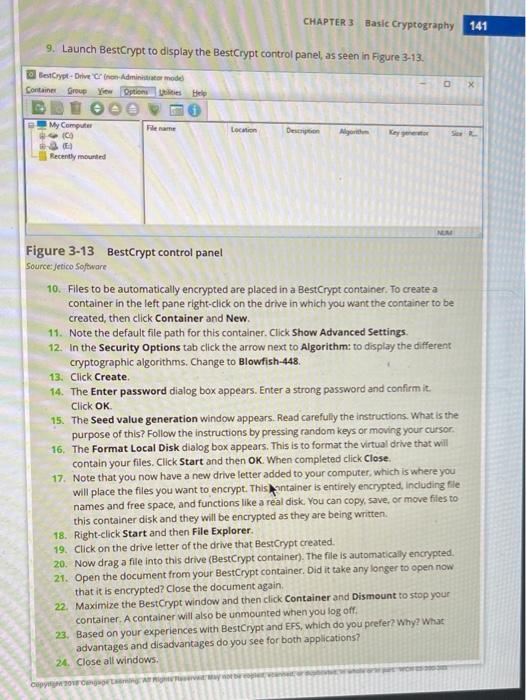
Question: Project 3-5: Using BestCrypt Third-party software applications can be downloaded to protect files with cryptography. In this project, you download and install Jetico BestCrypt. 1.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


