Question: Provide assistance completing the following assignment: Here are some tips to complete the matrix. Include the code citation for each of the listed laws. Describe
Provide assistance completing the following assignment:
Here are some tips to complete the matrix.
- Include the code citation for each of the listed laws.
- Describe specific legal requirements and penalties for each law.
- Compliance assessment. Indicate the level of compliance. Give solid reasons to support your compliance rating.
- Compliance risk assessment. Indicate the level of risk from the issue. Give solid reasons to support your risk assessment.
- Priority Rank. Rank the ten items from one to ten in order of priority. Justify your priorities with reasons.
- State the next managerial action you would take to comply with the law. Justify why you selected the action you did with solid reasons.
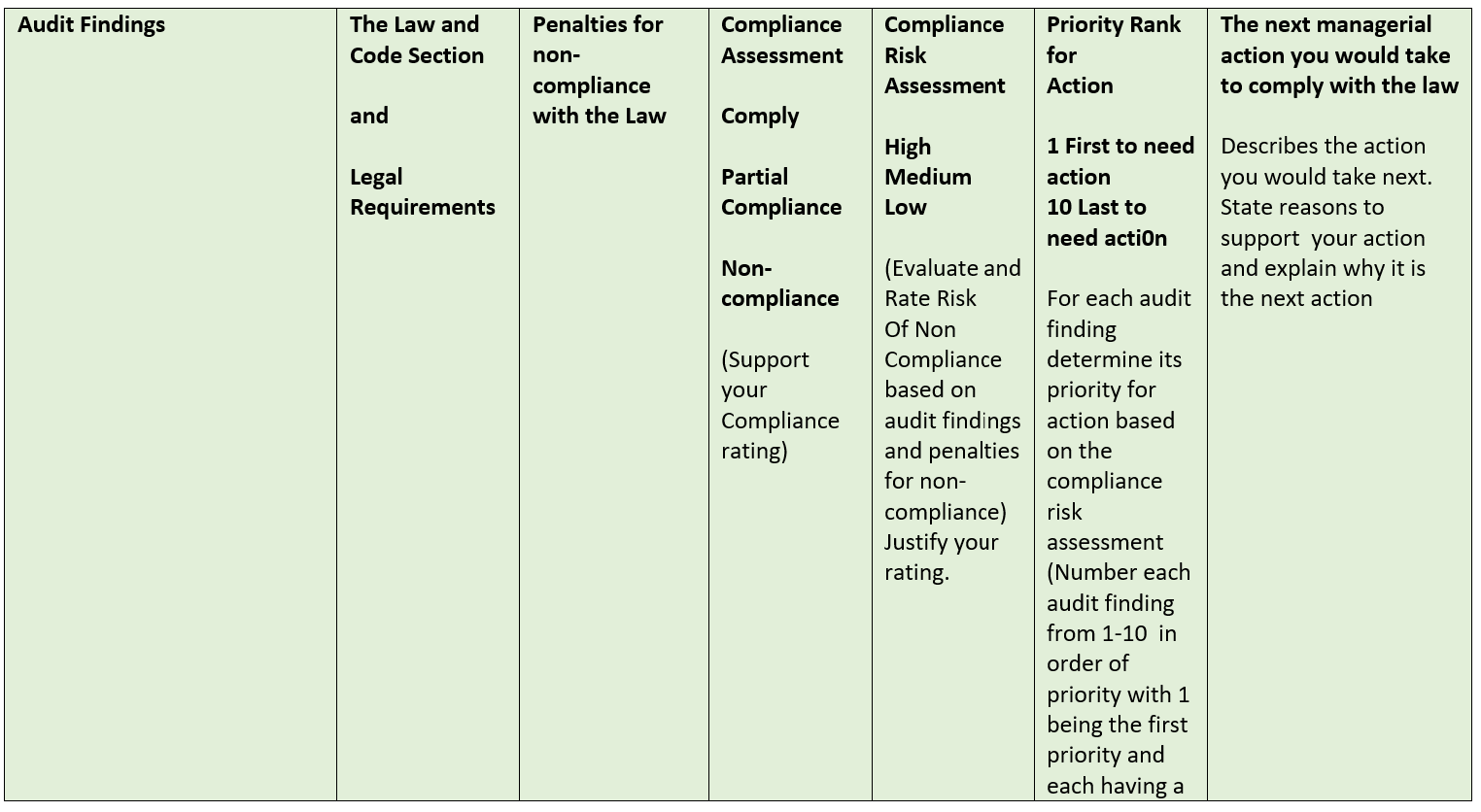
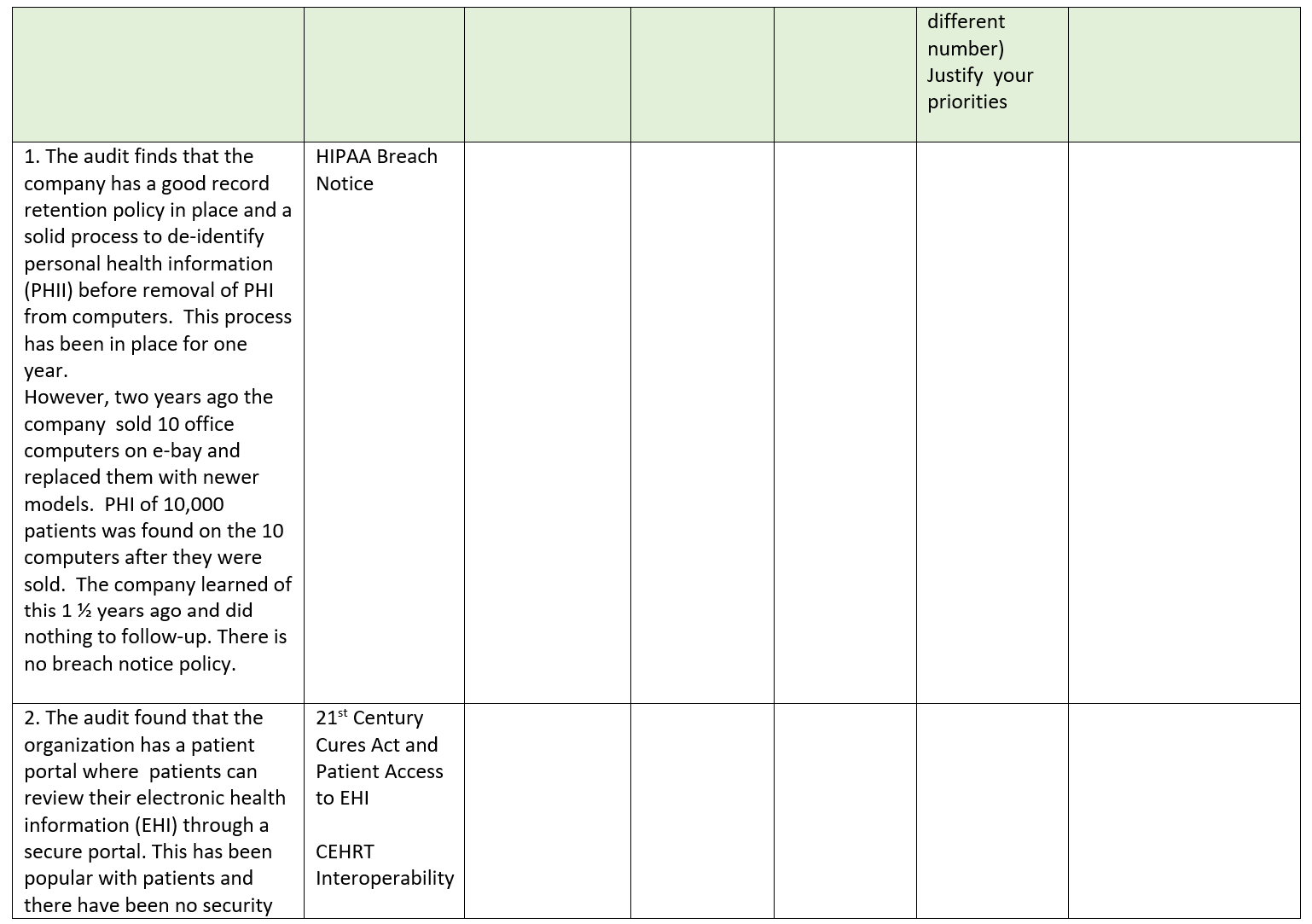
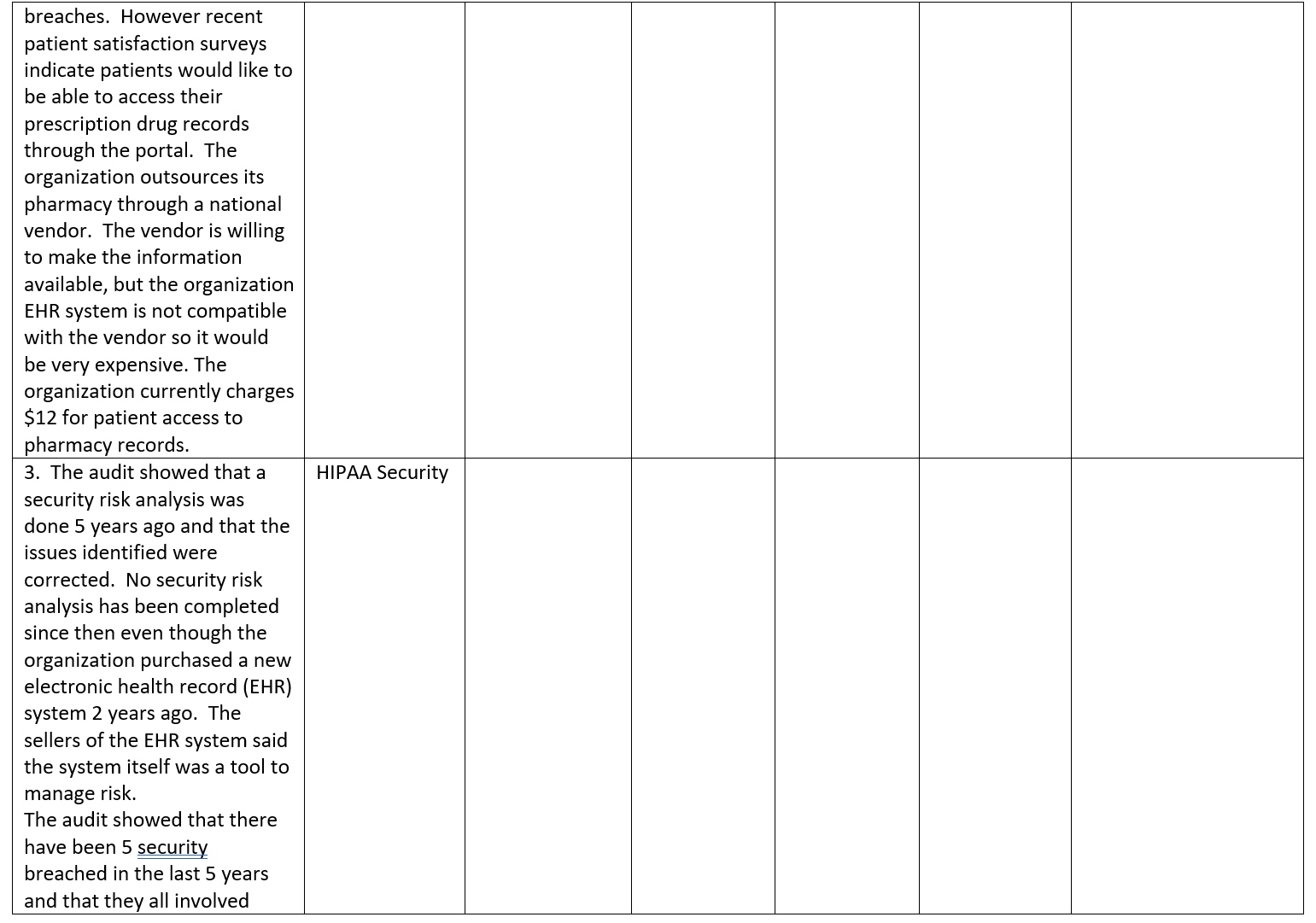
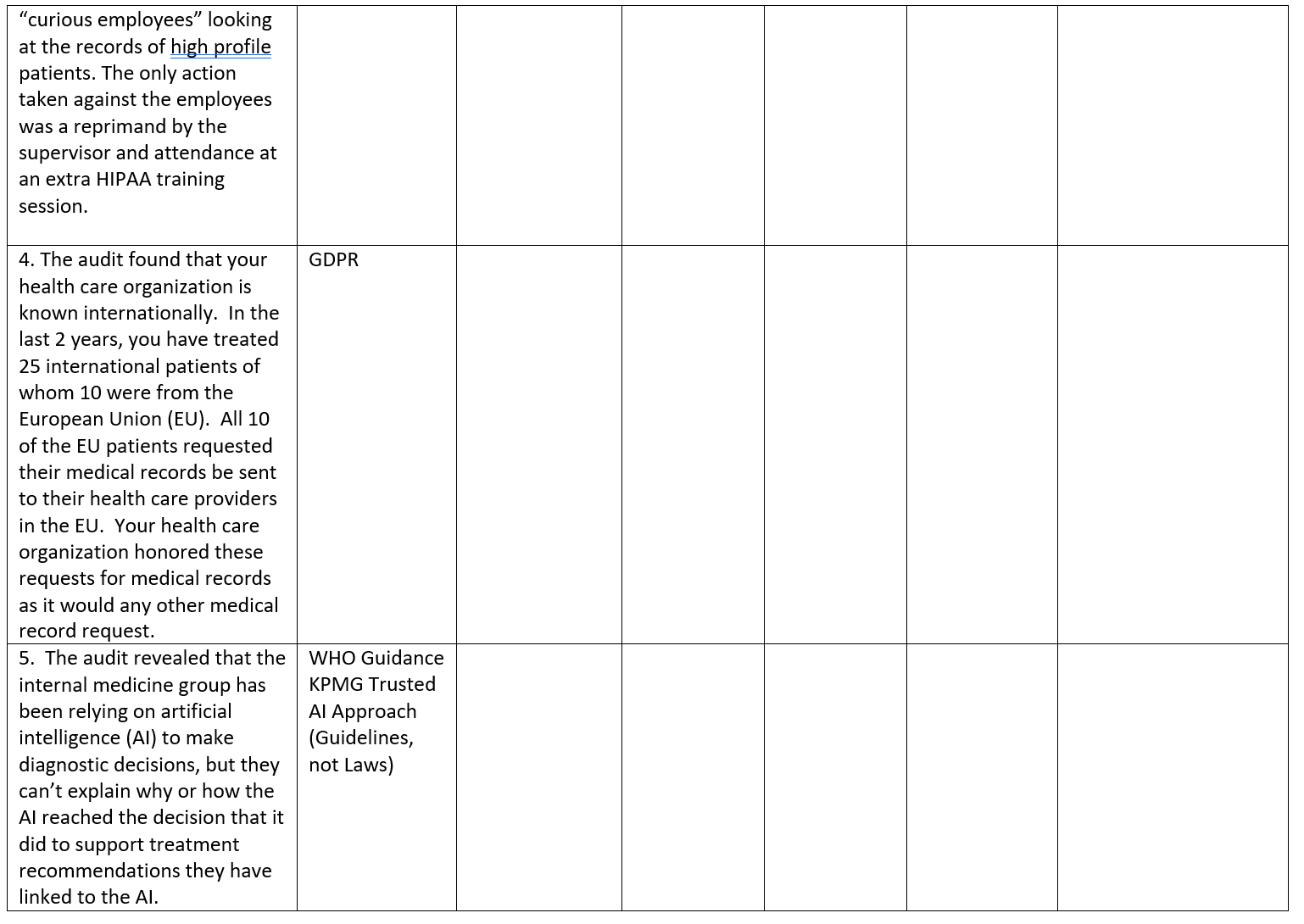
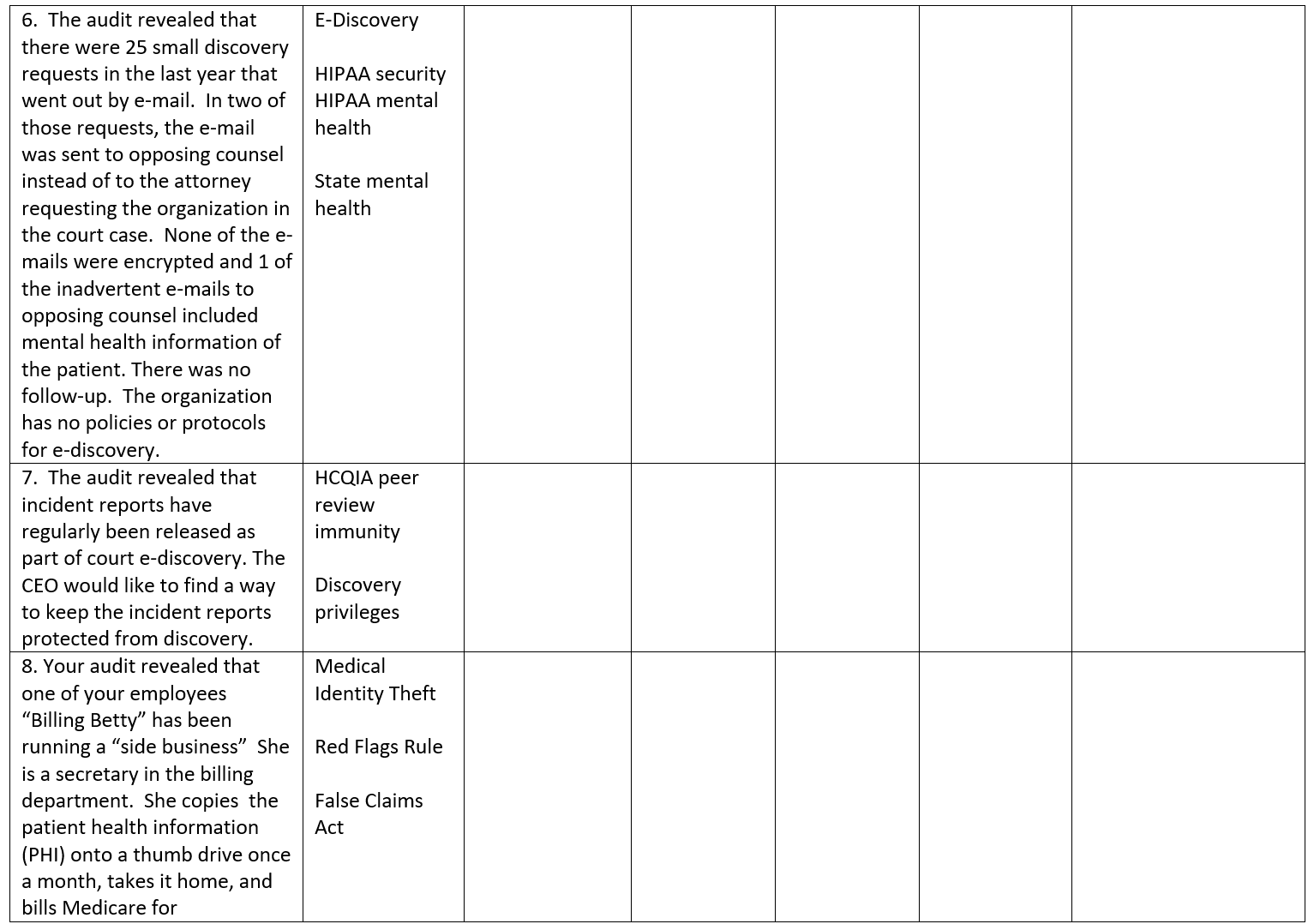
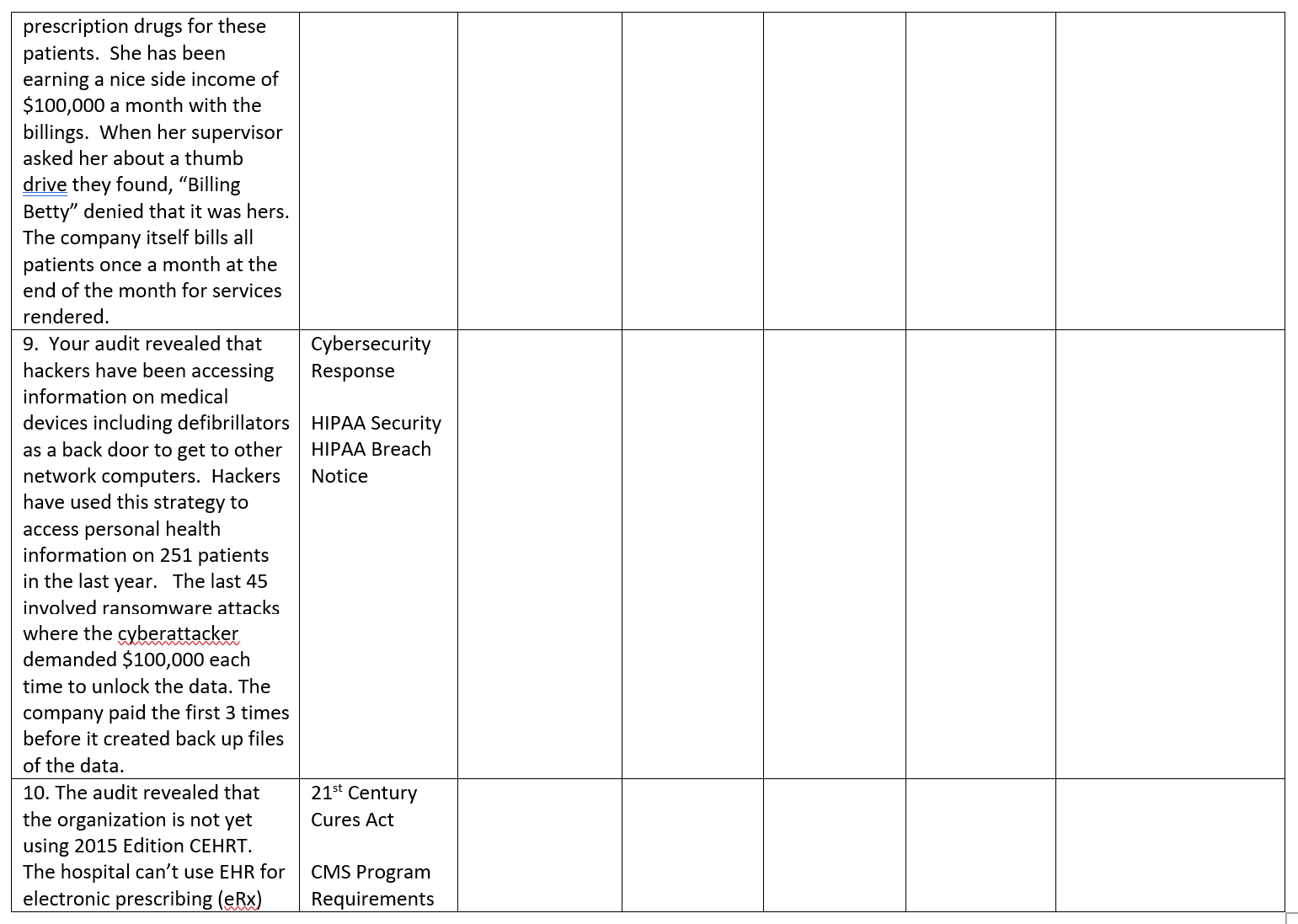
 Audit Findings The Law and Code Section and Legal Requirements Penalties for non- compliance with the Law Compliance Assessment Comply Partial Compliance Non- compliance (Support your Compliance rating) Compliance Risk Assessment High Medium Low (Evaluate and Rate Risk Of Non Compliance based on audit findings and penalties for non- compliance) Justify your rating. Priority Rank for Action 1 First to need action 10 Last to need actiOn For each audit finding determine its priority for action based on the compliance risk assessment (Number each audit finding from 1-10 in order of priority with 1 being the first priority and each having a The next managerial action you would take to comply with the law Describes the action you would take next. State reasons to support your action and explain why it is the next action different number) Justify your priorities 1. The audit finds that the company has a good record retention policy in place and a solid process to de-identify personal health information (PHII) before removal of PHI from computers. This process has been in place for one year. However, two years ago the company sold 10 office computers on e-bay and replaced them with newer models. PHI of 10,000 patients was found on the 10 computers after they were sold. The company learned of this 1 % years ago and did nothing to follow-up. There is no breach notice policy. HIPAA Breach Notice 2. The audit found that the organization has a patient portal where patients can review their electronic health information (EHI) through a secure portal. This has been popular with patients and there have been no security 21* Century Cures Act and Patient Access to EHI CEHRT Interoperability breaches. However recent patient satisfaction surveys indicate patients would like to be able to access their prescription drug records through the portal. The organization outsources its pharmacy through a national vendor. The vendor is willing to make the information available, but the organization EHR system is not compatible with the vendor so it would be very expensive. The organization currently charges $12 for patient access to pharmacy records. 3. The audit showed that a security risk analysis was done 5 years ago and that the issues identified were corrected. No security risk analysis has been completed since then even though the organization purchased a new electronic health record (EHR) system 2 years ago. The sellers of the EHR system said the system itself was a tool to manage risk. The audit showed that there have been 5 security breached in the last 5 years and that they all involved HIPAA Security \"curious employees\" looking at the records of high profile patients. The only action taken against the employees was a reprimand by the supervisor and attendance at an extra HIPAA training session. 4, The audit found that your health care organization is known internationally. In the last 2 years, you have treated 25 international patients of whom 10 were from the European Union (EU). All 10 of the EU patients requested their medical records be sent to their health care providers in the EU. Your health care organization honored these requests for medical records as it would any other medical record request. GDPR 5. The audit revealed that the internal medicine group has been relying on artificial intelligence (Al) to make diagnostic decisions, but they can't explain why or how the Al reached the decision that it did to support treatment recommendations they have linked to the Al. WHO Guidance KPMG Trusted Al Approach (Guidelines, not Laws) 6. The audit revealed that there were 25 small discovery requests in the last year that went out by e-mail. In two of those requests, the e-mail was sent to opposing counsel instead of to the attorney requesting the organization in the court case. None of the e- mails were encrypted and 1 of the inadvertent e-mails to opposing counsel included mental health information of the patient. There was no follow-up. The organization has no policies or protocols for e-discovery. E-Discovery HIPAA security HIPAA mental health State mental health 7. The audit revealed that incident reports have regularly been released as part of court e-discovery. The CEO would like to find a way to keep the incident reports protected from discovery. HCQIA peer review immunity Discovery privileges 8. Your audit revealed that one of your employees \"Billing Betty\" has been running a \"side business\" She is a secretary in the billing department. She copies the patient health information (PHI) onto a thumb drive once a month, takes it home, and bills Medicare for Medical Identity Theft Red Flags Rule False Claims Act prescription drugs for these patients. She has been earning a nice side income of $100,000 a month with the billings. When her supervisor asked her about a thumb drive they found, \"Billing Betty\" denied that it was hers. The company itself bills all patients once a month at the end of the month for services rendered. 9. Your audit revealed that hackers have been accessing information on medical devices including defibrillators as a back door to get to other network computers. Hackers have used this strategy to access personal health information on 251 patients in the last year. The last 45 involved ransomware attacks where the cyberattacker demanded $100,000 each time to unlock the data. The company paid the first 3 times before it created back up files of the data. Cybersecurity Response HIPAA Security HIPAA Breach Notice 10. The audit revealed that the organization is not yet using 2015 Edition CEHRT. The hospital can't use EHR for electronic prescribing (Rx) 21* Century Cures Act CMS Program Requirements and is not able to provide public health clinical date for reporting. Interoperability Requirements
Audit Findings The Law and Code Section and Legal Requirements Penalties for non- compliance with the Law Compliance Assessment Comply Partial Compliance Non- compliance (Support your Compliance rating) Compliance Risk Assessment High Medium Low (Evaluate and Rate Risk Of Non Compliance based on audit findings and penalties for non- compliance) Justify your rating. Priority Rank for Action 1 First to need action 10 Last to need actiOn For each audit finding determine its priority for action based on the compliance risk assessment (Number each audit finding from 1-10 in order of priority with 1 being the first priority and each having a The next managerial action you would take to comply with the law Describes the action you would take next. State reasons to support your action and explain why it is the next action different number) Justify your priorities 1. The audit finds that the company has a good record retention policy in place and a solid process to de-identify personal health information (PHII) before removal of PHI from computers. This process has been in place for one year. However, two years ago the company sold 10 office computers on e-bay and replaced them with newer models. PHI of 10,000 patients was found on the 10 computers after they were sold. The company learned of this 1 % years ago and did nothing to follow-up. There is no breach notice policy. HIPAA Breach Notice 2. The audit found that the organization has a patient portal where patients can review their electronic health information (EHI) through a secure portal. This has been popular with patients and there have been no security 21* Century Cures Act and Patient Access to EHI CEHRT Interoperability breaches. However recent patient satisfaction surveys indicate patients would like to be able to access their prescription drug records through the portal. The organization outsources its pharmacy through a national vendor. The vendor is willing to make the information available, but the organization EHR system is not compatible with the vendor so it would be very expensive. The organization currently charges $12 for patient access to pharmacy records. 3. The audit showed that a security risk analysis was done 5 years ago and that the issues identified were corrected. No security risk analysis has been completed since then even though the organization purchased a new electronic health record (EHR) system 2 years ago. The sellers of the EHR system said the system itself was a tool to manage risk. The audit showed that there have been 5 security breached in the last 5 years and that they all involved HIPAA Security \"curious employees\" looking at the records of high profile patients. The only action taken against the employees was a reprimand by the supervisor and attendance at an extra HIPAA training session. 4, The audit found that your health care organization is known internationally. In the last 2 years, you have treated 25 international patients of whom 10 were from the European Union (EU). All 10 of the EU patients requested their medical records be sent to their health care providers in the EU. Your health care organization honored these requests for medical records as it would any other medical record request. GDPR 5. The audit revealed that the internal medicine group has been relying on artificial intelligence (Al) to make diagnostic decisions, but they can't explain why or how the Al reached the decision that it did to support treatment recommendations they have linked to the Al. WHO Guidance KPMG Trusted Al Approach (Guidelines, not Laws) 6. The audit revealed that there were 25 small discovery requests in the last year that went out by e-mail. In two of those requests, the e-mail was sent to opposing counsel instead of to the attorney requesting the organization in the court case. None of the e- mails were encrypted and 1 of the inadvertent e-mails to opposing counsel included mental health information of the patient. There was no follow-up. The organization has no policies or protocols for e-discovery. E-Discovery HIPAA security HIPAA mental health State mental health 7. The audit revealed that incident reports have regularly been released as part of court e-discovery. The CEO would like to find a way to keep the incident reports protected from discovery. HCQIA peer review immunity Discovery privileges 8. Your audit revealed that one of your employees \"Billing Betty\" has been running a \"side business\" She is a secretary in the billing department. She copies the patient health information (PHI) onto a thumb drive once a month, takes it home, and bills Medicare for Medical Identity Theft Red Flags Rule False Claims Act prescription drugs for these patients. She has been earning a nice side income of $100,000 a month with the billings. When her supervisor asked her about a thumb drive they found, \"Billing Betty\" denied that it was hers. The company itself bills all patients once a month at the end of the month for services rendered. 9. Your audit revealed that hackers have been accessing information on medical devices including defibrillators as a back door to get to other network computers. Hackers have used this strategy to access personal health information on 251 patients in the last year. The last 45 involved ransomware attacks where the cyberattacker demanded $100,000 each time to unlock the data. The company paid the first 3 times before it created back up files of the data. Cybersecurity Response HIPAA Security HIPAA Breach Notice 10. The audit revealed that the organization is not yet using 2015 Edition CEHRT. The hospital can't use EHR for electronic prescribing (Rx) 21* Century Cures Act CMS Program Requirements and is not able to provide public health clinical date for reporting. Interoperability RequirementsStep by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


