Question: Purdu Model Level 0 Actual physical process I/O Field Devices Level 1 Intelligence Sensing Unit - Control: PLCs and RTUs Level 2 Process: Hardware/capability to
 Purdu Model
Purdu Model
- Level 0 Actual physical process I/O Field Devices
- Level 1 Intelligence Sensing Unit - Control: PLCs and RTUs
- Level 2 Process: Hardware/capability to monitor and control that process (PLC, RTU)
- Level 3 Control Systems Operation: Historians, network services and Adv Control Level 3.5 DMZ
- Level 4 Business Side (separate from Control Center Applications)
- Level 5 Enterprise IT Assignment Breakdown
Each week your readings and research assignment is to design a layer in a mock companys Secure Architecture Design. Will you be able to build your own SCADA system, no. But hopefully youll be able to understand where it fits into the bigger picture of IT and OT and what is required to design and secure it.
You can work alone or connect with other students in the class to make 2 to 3 member teams. Each week youll study materials, research, design, select brands or types of equipment, diagram and write up a summary. In the best case youd divide up the work but Ill leave that up to you. Thats why the group part is optional but for those that feel like ducks out of water you can group together and work through those areas together you dont understand.
Deliverable for Grading
2. Decide the process or industry you are going to work with
Written proposal which includes:
Team members
Industry and process your SCADA will monitor.
Purdu Model Level 0, 1
Diagram of proposed Levels 0 and 1
Equipment Lists with $$
Software if appropriate
Purdu Model Level 2
Diagram of proposed Level 2
Equipment Lists with $$
Software if appropriate
Purdu Model Level 3
Diagram of proposed Level 3
Equipment Lists with $$
Software if appropriate
Purdu Model Level 4
Diagram of proposed Level 4
Equipment Lists with $$
Software if appropriate
Purdu Model Level 5
Diagram of proposed Level 5
Equipment Lists with $$
Software if appropriate
Final Report that includes the final diagram, software, total cost of equipment, etc.
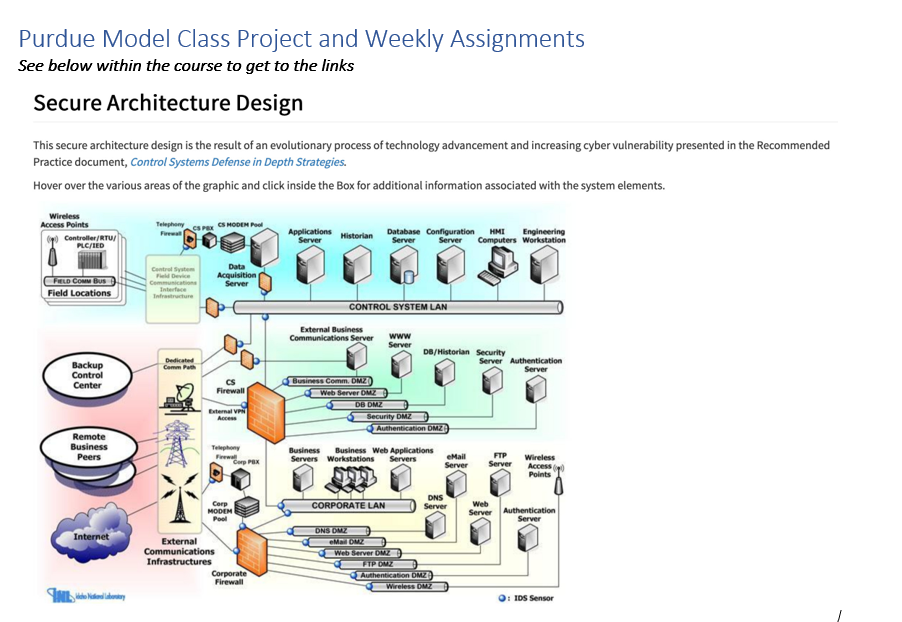
Purdue Model Class Project and Weekly Assignments See below within the course to get to the links Secure Architecture Design This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document, Control Systems Defense in Depth Strategies. Hover over the various areas of the graphic and click inside the Box for additional information associated with the system elements. Wireless Access Points Controller/RTU/ PLCIED Telephony CSP CS MODEM Applications Server Historian Database Configuration HMI Engineering Server Server Computers Workstation Data Acquisition Server FELD Cow Bus Field Locations Communication Infrastructure Dedicated Comm Puth Backup Control Center CONTROL SYSTEM LAN External Business Communications Server www Server DB/Historian Security Server Authentication Server Business Comm. OMZ Web Server OMZ DB DMZ Security OMZ Authentication DMZ Firewall External VPN Access Remote Business Peers wut Telephony Corp PBX Business Business Web Applications Servers Workstations Servers eMail Server FTP Server Wireless Access Points Corp CORPORATE LAN DNS Server MODEM Pool Web Server Authentication Server Internet External Communications Infrastructures Corporate Firewall ONS OME GMOWE Web Server OME FTP OMZ Authentication DMZ Wireless OUZ O: IDS Sensor Purdue Model Class Project and Weekly Assignments See below within the course to get to the links Secure Architecture Design This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document, Control Systems Defense in Depth Strategies. Hover over the various areas of the graphic and click inside the Box for additional information associated with the system elements. Wireless Access Points Controller/RTU/ PLCIED Telephony CSP CS MODEM Applications Server Historian Database Configuration HMI Engineering Server Server Computers Workstation Data Acquisition Server FELD Cow Bus Field Locations Communication Infrastructure Dedicated Comm Puth Backup Control Center CONTROL SYSTEM LAN External Business Communications Server www Server DB/Historian Security Server Authentication Server Business Comm. OMZ Web Server OMZ DB DMZ Security OMZ Authentication DMZ Firewall External VPN Access Remote Business Peers wut Telephony Corp PBX Business Business Web Applications Servers Workstations Servers eMail Server FTP Server Wireless Access Points Corp CORPORATE LAN DNS Server MODEM Pool Web Server Authentication Server Internet External Communications Infrastructures Corporate Firewall ONS OME GMOWE Web Server OME FTP OMZ Authentication DMZ Wireless OUZ O: IDS Sensor
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


