Question: Q 3 : Consider the three - node network below, that uses flow - based generalized forwarding ( e . g . , as in
Q:
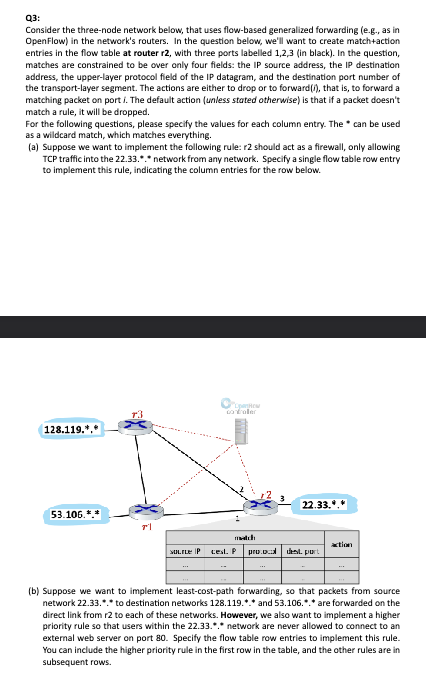
Consider the threenode network below, that uses flowbased generalized forwarding eg as in OpenFlow in the network's routers. In the question below, we'll want to create matchaction entries in the flow table at router mathbfr with three ports labelled in black In the question, matches are constrained to be over only four fields: the IP source address, the IP destination address, the upperlayer protocol field of the IP datagram, and the destination port number of the transportlayer segment. The actions are either to drop or to forward i that is to forward a matching packet on port i The default action unless stated otherwise is that if a packet doesn't match a rule, it will be dropped.
For the following questions, please specify the values for each column entry. The can be used as a wildcard match, which matches everything.
a Suppose we want to implement the following rule: mathbfr should act as a firewall, only allowing TCP traffic into the network from any network. Specify a single flow table row entry to implement this rule, indicating the column entries for the row below.
b Suppose we want to implement leastcostpath forwarding, so that packets from source network to destination networks and are forwarded on the direct link from r to each of these networks. However, we also want to implement a higher priority rule so that users within the network are never allowed to connect to an external web server on port Specify the flow table row entries to implement this rule. You can include the higher priority rule in the first row in the table, and the other rules are in subsequent rows.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


