Question: Q1 Q2 Consider the following security protocol, established between agents A and B and the server S, with the adversary E. The list of attacker
Q1

Q2

![A: [S, KAS, A, B], B:[ KBS, A, B ], S:[A,B,E, KA.S,](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66ef51bf525bf_06266ef51bec17fb.jpg)
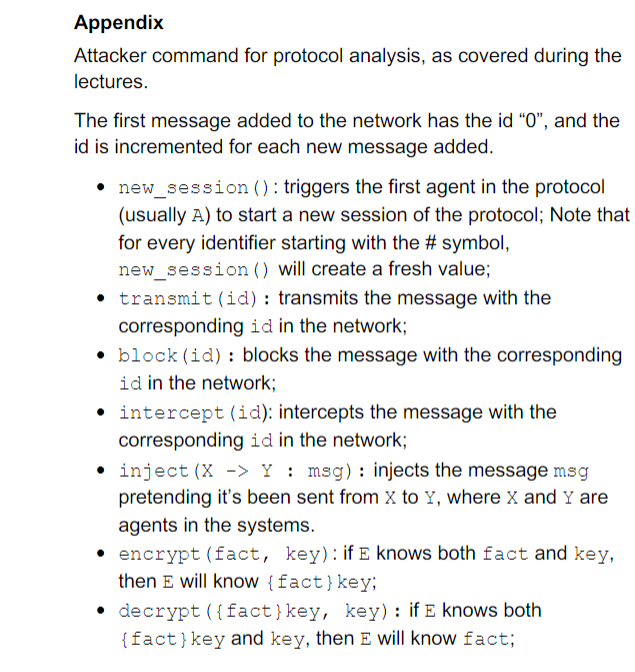
Consider the following security protocol, established between agents A and B and the server S, with the adversary E. The list of attacker commands covered during the lectures is provided in the appendix. Knowledge: A: [S, KAS, A, B], B:[ KBS, A, B ], S:[A,B,E, KA.S, KBS, KES, K] E:[A,B, KES, fake ] Steps: AS:A,B SA:{#K,{#K}KBS}KAS AB:{#K}KBS,{#S}K a) Design a sequence of exactly three attacker commands such that E knows {K0,{K0} KBS } KAS after executing these commands [2 Marks] b) If E knows [A,B, KES, fake, {K0,{K0} KBS } KA.S ], can E also know K o? Justify your answer [3 Marks] c) Design a sequence of commands such that E knows the current session secret. [5 Marks] d) Design a sequence of commands such that B knows fake. [5 Marks] Appendix Attacker command for protocol analysis, as covered during the lectures. The first message added to the network has the id "0", and the id is incremented for each new message added. - new_session ( ) : triggers the first agent in the protocol (usually A) to start a new session of the protocol; Note that for every identifier starting with the \# symbol, new_session () will create a fresh value; - transmit(id) : transmits the message with the corresponding id in the network; - block (id) : blocks the message with the corresponding id in the network; - intercept (id): intercepts the message with the corresponding id in the network; - inject (XY : msg) : injects the message msg pretending it's been sent from X to Y, where X and Y are agents in the systems. - encrypt (fact, key): if E knows both fact and key, then E will know { fact } key; - decrypt(\{fact } key, key) : if E knows both \{fact } key and key, then E will know fact; Consider the following security protocol, established between agents A and B and the server S, with the adversary E. The list of attacker commands covered during the lectures is provided in the appendix. The interactive material for this lecture can be found at https://protocols.morisset.eu/docs/ An online version of the protocol below can be found at https://morisset.gitlab.io/assessment/protocols/slksdgoiunbfdsy/ index.html Knowledge: A: [secret, KAS, A, B], B: [KBS, A, B], S:[A,B,E, KAS, KBS, KES, K] E: [A, B, KES, fake] Steps: (1) A S:A,B (2) SN:{#K,A,{K}KAS}KBS (3) BA:{K}KAS (4) A B:{ \#secret }K a) Design a sequence of commands such that B knows secret_1 [3 Marks] b) Design a sequence of commands such that E knows the secret_1. [6 Marks] c) Design a sequence of commands such that B knows fake. [6 Marks] d) Explain what should be done in the steps (2) and (3) to prevent the attacks found in b) and c). [5 Marks] Appendix Attacker command for protocol analysis, as covered during the lectures. The first message added to the network has the id "0", and the id is incremented for each new message added. - new_session ( ) : triggers the first agent in the protocol (usually A) to start a new session of the protocol; Note that for every identifier starting with the \# symbol, new_session () will create a fresh value; - transmit(id) : transmits the message with the corresponding id in the network; - block (id): blocks the message with the corresponding id in the network; - intercept (id): intercepts the message with the corresponding id in the network; - inject ( XY : msg) : injects the message msg pretending it's been sent from X to Y, where X and Y are agents in the systems. - encrypt (fact, key): if E knows both fact and key, then E will know { fact } key; - decrypt (\{fact } key, key) : if E knows both \{fact\} key and key, then E will know fact
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


