Question: Q17. For the question, assumptions are: (legitimate means :valid, normal, innocent) average constant legitimate request packets towards company A server is 5Mbps average constant reply
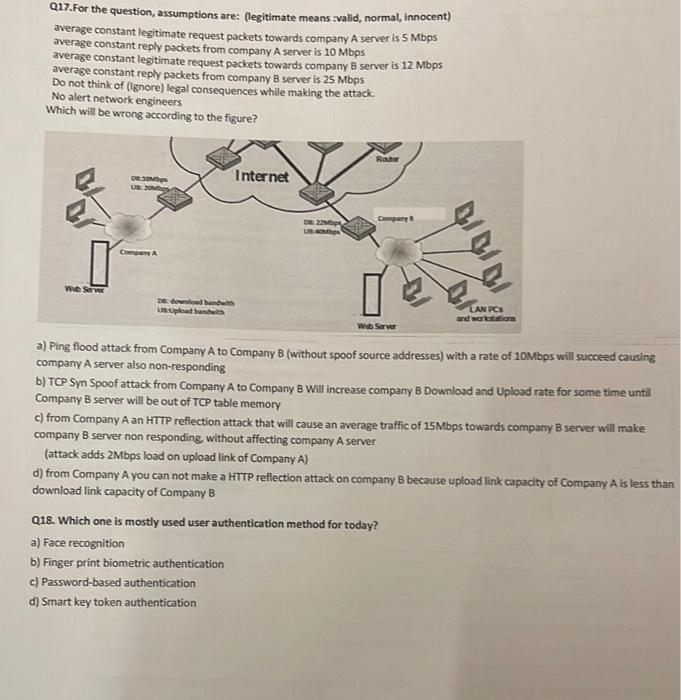
Q17. For the question, assumptions are: (legitimate means :valid, normal, innocent) average constant legitimate request packets towards company A server is 5Mbps average constant reply packets from company A server is 10 Mbps average constant legitimate request packets towards company B server is 12Mbps average constant reply packets from company B server is 25Mbps Do not think of (lgnore) legal consequences while making the attack. No alert network engineers Which will be wrong according to the figure? a) Ping flood attack from Company A to Company B (without spoof source addresses) with a rate of 10 Mbps will succeed causing company A server also non-responding b) TCP Syn Spoof attack from Company A to Company B Will increase company B Download and Upload rate for some time until Company B server will be out of TCP table memory c) from Company A an HTTP reflection attack that will cause an average traffic of 15Mbps towards company 8 server will make company 8 server non responding, without affecting company A server (attack adds 2Mbps load on upload link of Company A) d) from Company A you can not make a HTTP reflection attack on company B because upload link capacity of Company A is less than download link capacity of Company B Q18. Which one is mostly used user authentication method for today? a) Face recognition b) Finger print biometric authentication c) Password-based authentication d) Smart key token authentication
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


