Question: Q2 : Depending on the photo 1- Scope statement. (Define the project boundaries by listing all items that are included in the scope of this

Q2 : Depending on the photo
1- Scope statement. (Define the project boundaries by listing all items that are included in the scope of this project)
2- Make the task list as Work breakdown structure (WBS) in MS. Project.
Note: try to use Project Management Process Groups and Knowledge Areas
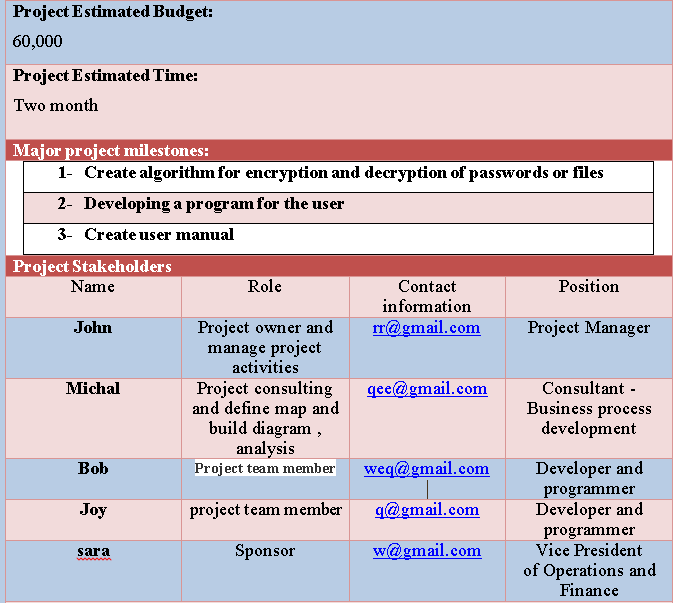
Project Charter: Project title: Encryption and Decryption of passwords or files. Project Start Date: 2021/03/23 Project Finish Date: 2021/05/23 Problem Statement: In the current world everything is centralized and due to that centralized system the privacy is detroyed. When we go to a website and we auto save any password and username, suppose if hacker trackyour password and take all the account details of you then what? or into your computer you have keep all your password in any database then what if any attackencountered by any hacker and all your password would taken by him then there will be huge problem. Description: Here we are going to change the problem of privacyless environment. We are going to make a project on encryption and decryption of passwords and files. Through which one can trustworthy to a person to whom he is giving his private details. And this can be done through methods of encryptions. Objectives: There are following objectives: 1-To make privacy of peoples really private. Actually the privacy is virtual. 2-To make Peoples aware about data stealing. 3-Save peoples from frauds. And only objective to make this project is to make peoples completely tensionless. Project Scope, Constraints, Assumptions: As blockchain technology is growing more fasterin present time and future will be of block chain technology. Andit only concern about security and privacy hence encyption and decrytion has a tremendous scope. Billions of dollors are used to maintain privacy but still privacy isn't safe. Assumption: This project will be easier as it seen, we just have to write code for the methods going to use for encryption and decryption. like : vighenere cipher, caesor cipher, Monoalphabetic substitution method etc. for encyption and decryption. Constraints: This can be made in c.c++, java and any you may prefer. Maybe you can make a web application or a application or a webpage where encryption or decryption happens through any method. Project Estimated Budget: 60,000 Project Estimated Time: Two month Major project milestones: 1- Create algorithm for encryption and decryption of passwords or files 2- Developing a program for the user 3- Create user manual Project Stakeholders Name Role Contact Position information John Project owner and rr@gmail.com Project Manager manage project activities Michal Project consulting qee@gmail.com Consultant - and define map and Business process build diagram, development analysis Bob Project team member weq@gmail.com Developer and programmer Joy project team member q@gmail.com Developer and programmer Sponsor w@gmail.com Vice President of Operations and Finance sara Project Charter: Project title: Encryption and Decryption of passwords or files. Project Start Date: 2021/03/23 Project Finish Date: 2021/05/23 Problem Statement: In the current world everything is centralized and due to that centralized system the privacy is detroyed. When we go to a website and we auto save any password and username, suppose if hacker trackyour password and take all the account details of you then what? or into your computer you have keep all your password in any database then what if any attackencountered by any hacker and all your password would taken by him then there will be huge problem. Description: Here we are going to change the problem of privacyless environment. We are going to make a project on encryption and decryption of passwords and files. Through which one can trustworthy to a person to whom he is giving his private details. And this can be done through methods of encryptions. Objectives: There are following objectives: 1-To make privacy of peoples really private. Actually the privacy is virtual. 2-To make Peoples aware about data stealing. 3-Save peoples from frauds. And only objective to make this project is to make peoples completely tensionless. Project Scope, Constraints, Assumptions: As blockchain technology is growing more fasterin present time and future will be of block chain technology. Andit only concern about security and privacy hence encyption and decrytion has a tremendous scope. Billions of dollors are used to maintain privacy but still privacy isn't safe. Assumption: This project will be easier as it seen, we just have to write code for the methods going to use for encryption and decryption. like : vighenere cipher, caesor cipher, Monoalphabetic substitution method etc. for encyption and decryption. Constraints: This can be made in c.c++, java and any you may prefer. Maybe you can make a web application or a application or a webpage where encryption or decryption happens through any method. Project Estimated Budget: 60,000 Project Estimated Time: Two month Major project milestones: 1- Create algorithm for encryption and decryption of passwords or files 2- Developing a program for the user 3- Create user manual Project Stakeholders Name Role Contact Position information John Project owner and rr@gmail.com Project Manager manage project activities Michal Project consulting qee@gmail.com Consultant - and define map and Business process build diagram, development analysis Bob Project team member weq@gmail.com Developer and programmer Joy project team member q@gmail.com Developer and programmer Sponsor w@gmail.com Vice President of Operations and Finance saraStep by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


