Question: Q4. Network Traffic Analysis (20 points) Use Network Miner program to load and study the PCAP file uploaded with the assignment on D2L. PCAP=> DoS-15m-12h_1
Q4. Network Traffic Analysis (20 points) Use Network Miner program to load and study the PCAP file uploaded with the assignment on D2L. PCAP=> DoS-15m-12h_1
a. List 3 observations about the network, in terms of number of hosts, IP addresses, type of traffic/protocol. (6 points)
b. Extract and list 4 sets of credentials (user name / passwords) that communicated over the network. (4 points)
c. Examine host 172.27.224.99
1. What OS is running on that host? (2 points)
2. What can you tell about traffic from and to that host? (4 points)
3. This is host is carrying a DoS attack, can you identify the victim hosts in the network? (4 points)
Pic for question:
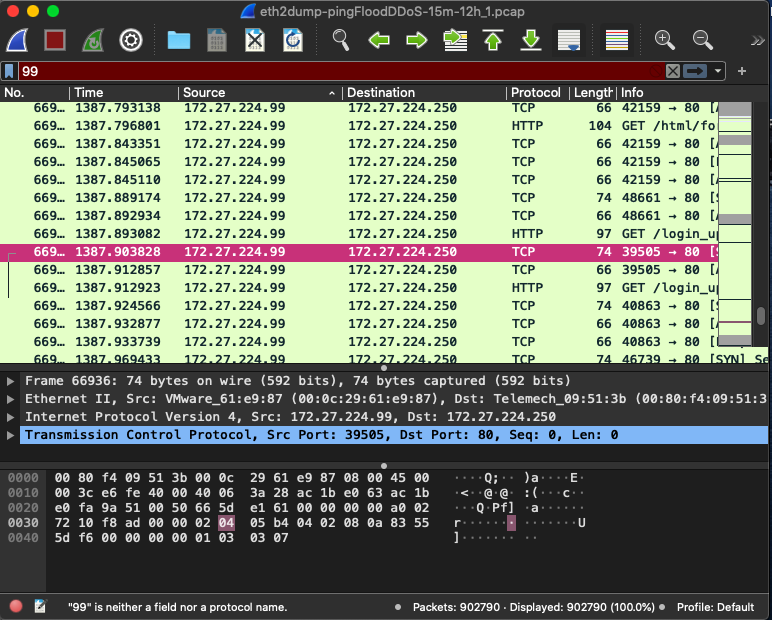
eth2dump-pingFloodDDoS-15m-12h_1.pcap X TCP 1.99 + No. Time Source Destination | Protocol Length Info 669... 1387.793138 172.27.224.99 172.27.224.250 66 42159 80 669... 1387.796801 172.27.224.99 172.27.224.250 HTTP 104 GET /html/fo 669... 1387.843351 172.27.224.99 172.27.224.250 TCP 66 42159 + 80 [ 669... 1387.845065 172.27.224.99 172.27.224.250 TCP 66 42159 80 [ 669... 1387.845110 172.27.224.99 172.27.224.250 TCP 66 42159 80 L 669... 1387.889174 172.27.224.99 172.27.224.250 TCP 74 48661 80 669... 1387.892934 172.27.224.99 172.27.224.250 TCP 66 48661 + 80 [ 669... 1387.893082 172.27.224.99 172.27.224.250 HTTP 97 GET /login_u 669... 1387.903828 172.27.224.99 172.27.224.250 TCP 74 39505 80 : 669... 1387.912857 172.27.224.99 172.27.224.250 TCP 66 39505 80 L 669... 1387.912923 172.27.224.99 172.27.224.250 HTTP 97 GET /login_u 669... 1387.924566 172.27.224.99 172.27.224.250 TCP 74 40863 + 80 669... 1387.932877 172.27.224.99 172.27.224.250 TCP 0 66 40863 80 ch 669... 1387.933739 172.27.224.99 172.27.224.250 TCP 66 40863 + 80 il 669. 1387.969433 172.27.224.99 172.27.224.250 TCP 74_46739 89 LSYNLS Frame 66936: 74 bytes on wire (592 bits), 74 bytes captured (592 bits) Ethernet II, Src: VMware_61:e9:87 (00:0c:29:61:49:87), Dst: Telemech_09:51:36 (00:80:f4:09:51:3 Internet Protocol Version 4, Src: 172.27.224.99, Dst: 172.27.224.250 Transmission Control Protocol, Src Port: 39505, Dst Port: 80, Seq: 0, Len: 0 0000 0010 0020 0030 0040 00 80 f4 09 51 3b 00 Oc 00 3c e6 fe 40 00 40 06 e fa 9a 51 00 50 66 5d 72 10 f8 ad 00 00 02 04 5d f6 00 00 00 00 01 03 29 61 e9 87 08 00 45 00 3a 28 ac 1b eo 63 ac 1b el 61 00 00 00 00 ao 02 05 b4 04 02 08 a 83 55 03 07 Q; .. <.. q.pf da ...e : ..c.. a.. u is neither a field nor protocol name. packets: displayed: profile: default eth2dump-pingfloodddos-15m-12h_1.pcap x tcp no. time source destination length info http get l ch il lsynls frame bytes on wire bits captured ethernet ii src: vmware_61:e9:87 dst: telemech_09:51:36 internet version transmission control src port: dst seq: len: f4 oc e6 fe e fa f8 ad f6 e9 ac eo el ao b4 q ..>
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


