Question: Question 1 0 / 1 point The FTC is also charged with enforcing data safeguards pursuant to which law? Sec. 11 of the FTC Act
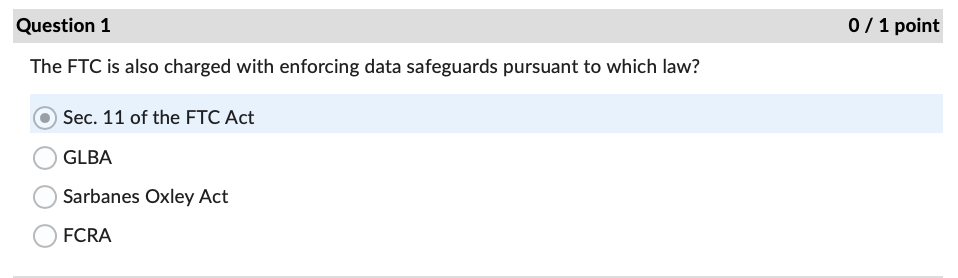
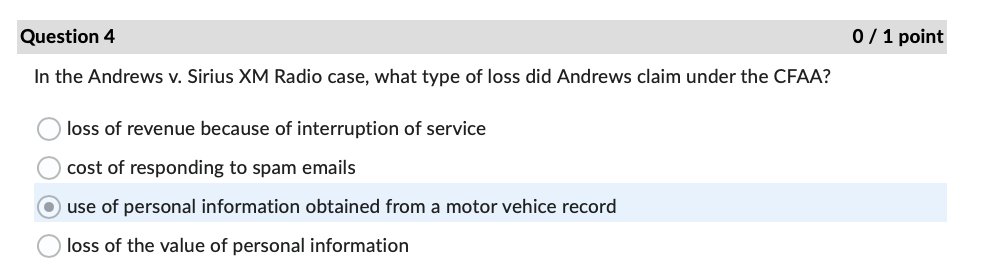

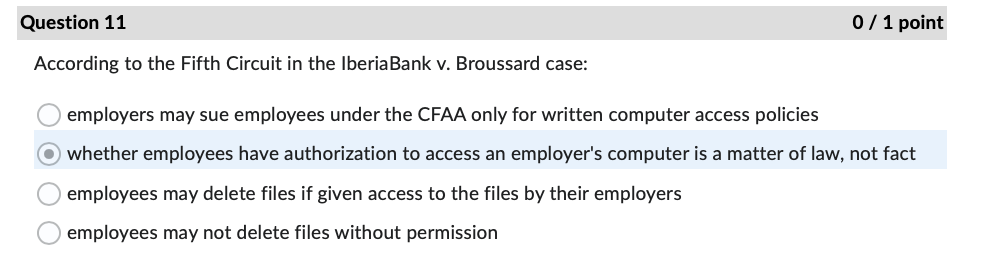
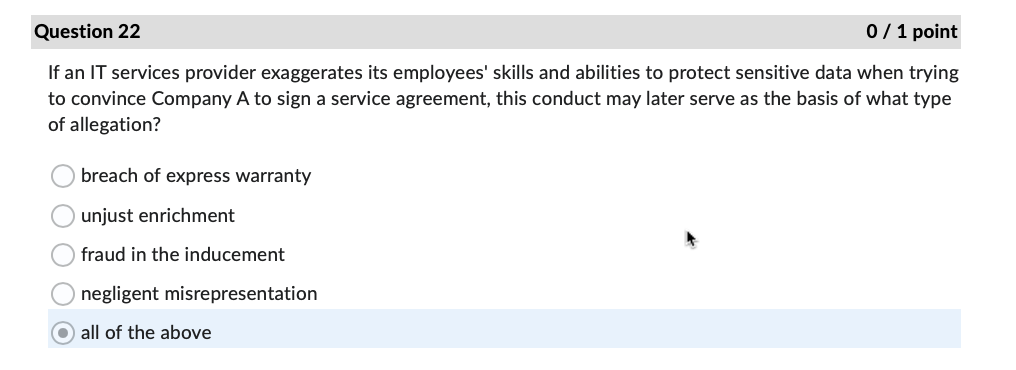
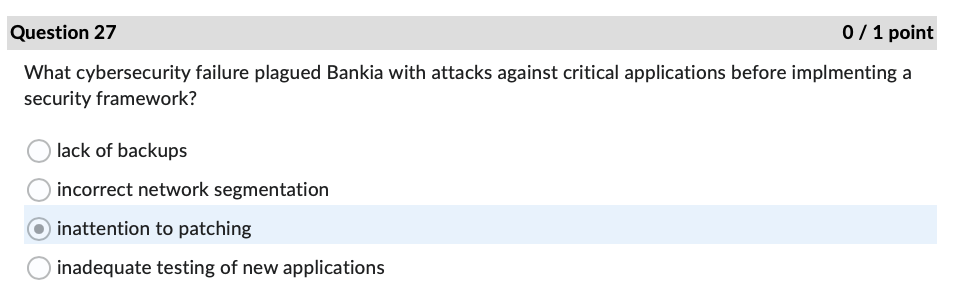
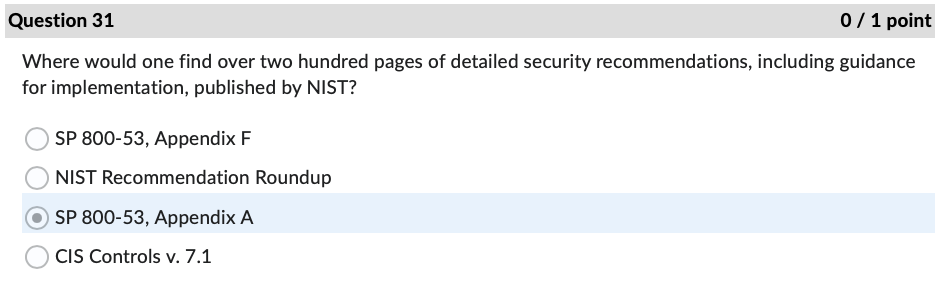
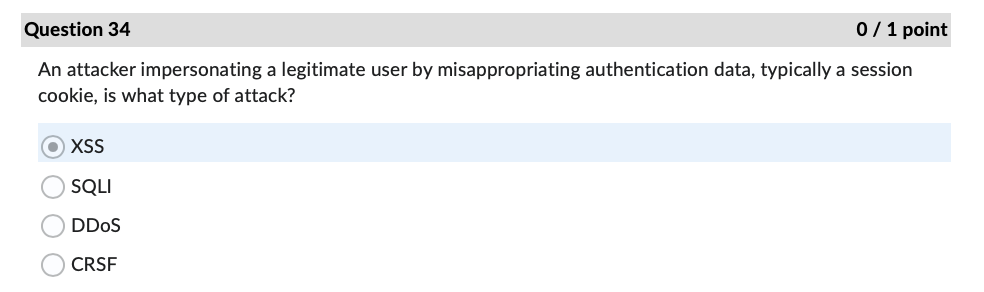
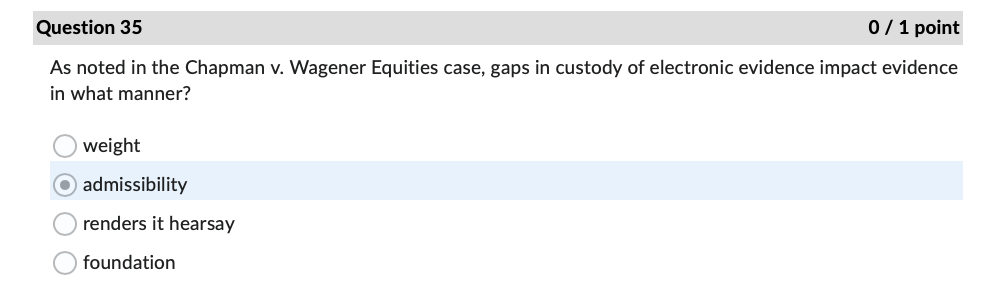
 Question 1 0 / 1 point The FTC is also charged with enforcing data safeguards pursuant to which law? Sec. 11 of the FTC Act GLBA Sarbanes Oxley Act OFCRAQuestion 4 0 / 1 point In the Andrews v. Sirius XM Radio case, what type of loss did Andrews claim under the CFAA? O loss of revenue because of interruption of service O cost of responding to spam emails use of personal information obtained from a motor vehiclecord O loss of the value of personal informationQuestion 7 0/1 point In the United States v. Goodyear case, what cost did the Court of Appeals hold was eligible under the CFAA for establishing the minimum amount of loss? security assessment by an external auditor ) credit monitoring for two years continuing cyber-attack protection for one year creation of information security program by a consultant Question 11 0/1 point According to the Fifth Circuit in the IberiaBank v. Broussard case: employers may sue employees under the CFAA only for written computer access policies ) whether employees have authorization to access an employer's computer is a matter of law, not fact employees may delete files if given access to the files by their employers employees may not delete files without permission Question 22 0/1 point If an IT services provider exaggerates its employees' skills and abilities to protect sensitive data when trying to convince Company A to sign a service agreement, this conduct may later serve as the basis of what type of allegation? breach of express warranty unjust enrichment fraud in the inducement negligent misrepresentation ) all of the above Question 27 0/1 point What cybersecurity failure plagued Bankia with attacks against critical applications before implmenting a security framework? lack of backups incorrect network segmentation ) inattention to patching inadequate testing of new applications Question 31 0 / 1 point Where would one find over two hundred pages of detailed security recommendations, including guidance for implementation, published by NIST? O SP 800-53, Appendix F ONIST Recommendation Roundup O SP 800-53, Appendix A OCIS Controls v. 7.1Question 34 0 / 1 point An attacker impersonating a legitimate user by misappropriating authentication data, typically a session cookie, is what type of attack? OXSS O SQLI O DDOS O CRSFQuestion 35 0/1 point As noted in the Chapman v. Wagener Equities case, gaps in custody of electronic evidence impact evidence in what manner? weight ) admissibility renders it hearsay foundation Question 36 0/1 point In the U.S. v. Fluker case, email evidence was not admitted because the government offered only circumstantial evidence to authenticate them. e) True False Question 40 0/1 point According to the Donaldson v. Central Illinois Public Service Co. case, Illinois courts must hold a hearing before admitting expert scientific testimony when: e) the expert's conclusions are not generally accepted in the field the witness offers an expert opinion the method of analysis is new to science the witness is not a recognized expert in the field
Question 1 0 / 1 point The FTC is also charged with enforcing data safeguards pursuant to which law? Sec. 11 of the FTC Act GLBA Sarbanes Oxley Act OFCRAQuestion 4 0 / 1 point In the Andrews v. Sirius XM Radio case, what type of loss did Andrews claim under the CFAA? O loss of revenue because of interruption of service O cost of responding to spam emails use of personal information obtained from a motor vehiclecord O loss of the value of personal informationQuestion 7 0/1 point In the United States v. Goodyear case, what cost did the Court of Appeals hold was eligible under the CFAA for establishing the minimum amount of loss? security assessment by an external auditor ) credit monitoring for two years continuing cyber-attack protection for one year creation of information security program by a consultant Question 11 0/1 point According to the Fifth Circuit in the IberiaBank v. Broussard case: employers may sue employees under the CFAA only for written computer access policies ) whether employees have authorization to access an employer's computer is a matter of law, not fact employees may delete files if given access to the files by their employers employees may not delete files without permission Question 22 0/1 point If an IT services provider exaggerates its employees' skills and abilities to protect sensitive data when trying to convince Company A to sign a service agreement, this conduct may later serve as the basis of what type of allegation? breach of express warranty unjust enrichment fraud in the inducement negligent misrepresentation ) all of the above Question 27 0/1 point What cybersecurity failure plagued Bankia with attacks against critical applications before implmenting a security framework? lack of backups incorrect network segmentation ) inattention to patching inadequate testing of new applications Question 31 0 / 1 point Where would one find over two hundred pages of detailed security recommendations, including guidance for implementation, published by NIST? O SP 800-53, Appendix F ONIST Recommendation Roundup O SP 800-53, Appendix A OCIS Controls v. 7.1Question 34 0 / 1 point An attacker impersonating a legitimate user by misappropriating authentication data, typically a session cookie, is what type of attack? OXSS O SQLI O DDOS O CRSFQuestion 35 0/1 point As noted in the Chapman v. Wagener Equities case, gaps in custody of electronic evidence impact evidence in what manner? weight ) admissibility renders it hearsay foundation Question 36 0/1 point In the U.S. v. Fluker case, email evidence was not admitted because the government offered only circumstantial evidence to authenticate them. e) True False Question 40 0/1 point According to the Donaldson v. Central Illinois Public Service Co. case, Illinois courts must hold a hearing before admitting expert scientific testimony when: e) the expert's conclusions are not generally accepted in the field the witness offers an expert opinion the method of analysis is new to science the witness is not a recognized expert in the field
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


